Source: securityaffairs.com – Author: Pierluigi Paganini Earth Lusca expands its arsenal with SprySOCKS Linux malware Pierluigi Paganini September 19, 2023 China-linked threat actor Earth Lusca used...
Day: September 19, 2023
Microsoft AI research division accidentally exposed 38TB of sensitive data – Source: securityaffairs.com
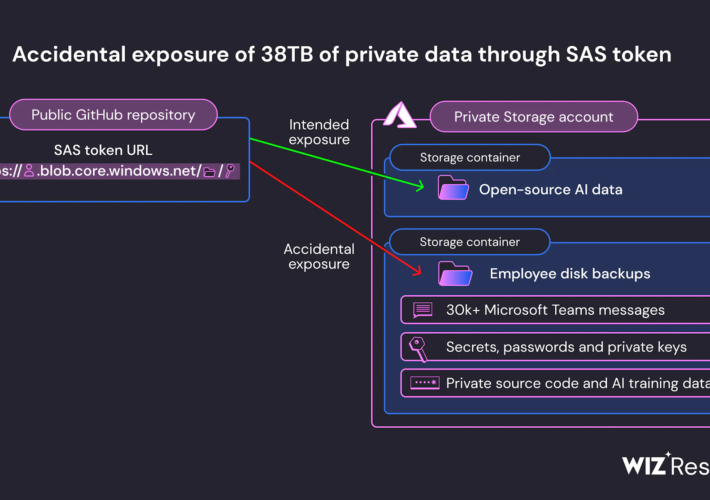
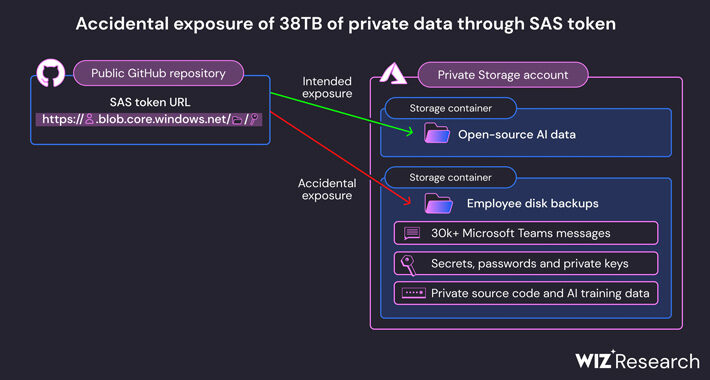
Source: securityaffairs.com – Author: Pierluigi Paganini Microsoft AI research division accidentally exposed 38TB of sensitive data Pierluigi Paganini September 18, 2023 Microsoft AI researchers accidentally exposed...
German intelligence warns cyberattacks could target liquefied natural gas (LNG) terminals – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini German intelligence warns cyberattacks could target liquefied natural gas (LNG) terminals Pierluigi Paganini September 18, 2023 The head of Germany’s...
Deepfake and smishing. How hackers compromised the accounts of 27 Retool customers in the crypto industry – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Deepfake and smishing. How hackers compromised the accounts of 27 Retool customers in the crypto industry Pierluigi Paganini September 18,...
Over 12,000 Juniper Firewalls Found Vulnerable to Recently Disclosed RCE Vulnerability – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 19, 2023THNNetwork Security / Exploit New research has found that close to 12,000 internet-exposed Juniper firewall devices are vulnerable to...
Transparent Tribe Uses Fake YouTube Android Apps to Spread CapraRAT Malware – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 19, 2023THNMobile Security / Malware The suspected Pakistan-linked threat actor known as Transparent Tribe is using malicious Android apps mimicking...
Microsoft AI Researchers Accidentally Expose 38 Terabytes of Confidential Data – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 19, 2023THNData Safety / Cybersecurity Microsoft on Monday said it took steps to correct a glaring security gaffe that led...
Niagara Networks and Scope Middle East Announce Strategic VAD Partnership – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 FREMONT, Calif., Sept. 18, 2023 /PRNewswire/ — Niagara Networks™, a Silicon Valley-based company that pioneers the award-winning Open Visibility Platform™, announced today a new partnership...
Omdia Research Finds Risk-Based Vulnerability Management Set to Encompass the Vulnerability Management Market by 2027 – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 LONDON, Sept. 18, 2023 /PRNewswire/ — The first comparative research into the evolution of the vulnerability management market authored by Omdia has found risk-based vulnerability management...
Payment Card-Skimming Campaign Now Targeting Websites in North America – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer, Dark Reading A Chinese-speaking threat actor that has been skimming credit card numbers off ecommerce sites and point-of-sale...
Microsoft Azure Data Leak Exposes Dangers of File-Sharing Links – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer, Dark Reading An overly permissive file-sharing link allowed public access to a massive 38TB storage bucket containing private...
Security Conferences Keep Us Honest – Source: www.darkreading.com
Source: www.darkreading.com – Author: Michael Bargury, CTO & Co-Founder, Zenity In August on a stage at Black Hat USA, I described in detail how Microsoft guest...
LockBit Is Using RMMs to Spread Its Ransomware – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer, Dark Reading The LockBit ransomware group is taking advantage of remote monitoring and management (RMM) software to spread...
How to Get Your Board on Board With Cybersecurity – Source: www.darkreading.com
Source: www.darkreading.com – Author: Brent Johnson, Chief Information Security Officer, Bluefin Nearly three-quarters (73%) of cybersecurity industry leaders have experienced burnout in the last 12 months...
Dragos Raises $74M in Latest Funding Round – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading ICS/OT vendor Dragos has raised $74 million in a Series D extension funding round led by investing...
A Playbook for Bridging Africa’s Cybersecurity Skills Shortage – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dan Raywood, Senior Editor, Dark Reading In July, the US government announced the National Cyber Workforce and Education Strategy (NCWES) which is aimed...
White Hat Hackers Discover Microsoft Leak of 38TB of Internal Data Via Azure Storage – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Megan Crouse on September 18, 2023, 6:10 PM EDT White Hat Hackers Discover Microsoft Leak of 38TB of Internal Data Via Azure...
Google Reveals Combined SIEM and SOAR Update for Chronicle Security Operations Platform – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Megan Crouse Users of the SecOps platform can preview Duet AI’s natural language questions and summarization capabilities. Google Cloud announced today that...
CISA Aims For More Robust Open Source Software Security for Government and Critical Infrastructure – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Megan Crouse The agency’s roadmap outlines a plan for prioritizing where open source software makes infrastructure potentially vulnerable. The US Cybersecurity and...
What Does Closed-Door Meeting With AI Industry Leaders Mean for Business? – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Megan Crouse Some of the United States’ top tech executives and generative AI development leaders met with senators last Wednesday in a...
Best IT Asset Management Software for 2023 – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Franklin Okeke Asset Panda: Best for allowing unlimited users SysAid: Best for ticket automation Freshservice: Best for intelligent alerting system UpKeep: Best...
Remote Access Checklist – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: This Remote Access Checklist from TechRepublic Premium should be used to ensure all employees have the requisite items, accounts, access and instructions...
Using Hacked LastPass Keys to Steal Cryptocurrency – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Remember last November, when hackers broke into the network for LastPass—a password database—and stole password vaults with both encrypted and...
Real World Impact of Medical Device Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Tony Bradley TechSpective Podcast Episode 116 Getting hacked sucks in all scenarios. In most cases, though, getting hacked is an inconvenience....
Uplevel to Next-Generation Vulnerability Management with our CISO Guide – Source: securityboulevard.com
Source: securityboulevard.com – Author: rezilion Vulnerability management is difficult and not getting any easier. CISOs and security teams struggle to keep their organizations safe from cyber...
Group Allegedly Behind MGM, Caesars Attacks is Fairly New to Ransomware – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt The threat group that claims to have been involved in the high-profile attacks earlier this month on casino operators MGM...
Guide to IoT in 2023: What’s New and Why It Matters? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Toback The Dawn of IoT: A Revolution in the Digital World In today’s interconnected world, the Guide to IoT is more...
If the worst happens: How to prep your accounts so your loved one can get into them – Source: securityboulevard.com
Source: securityboulevard.com – Author: Avast Blog It’s not fun to think about: But if you should unexpectedly die, could your spouse, partner, children or other loved...
Modernized Financial Cards for the Next Generation of Payments – Source: securityboulevard.com
Source: securityboulevard.com – Author: Nak Koh Financial cards have been a cornerstone of our monetary transactions for decades, providing us with convenience and security. Yet as...
An Enterprise Action Plan For CDR – Source: securityboulevard.com
Source: securityboulevard.com – Author: Votiro Team By David NeumanSenior Analyst, TAG Cyber [email protected] Introduction Information is the lifeblood of 21st-century businesses. They depend on the ability to...