Source: www.securityweek.com – Author: Ionut Arghire Freecycle.org, a platform that allows users to recycle their belongings, has prompted millions of users to reset their passwords after...
Day: September 6, 2023
Norfolk Southern Says a Software Defect — Not a Hacker — Forced It to Park Its Trains This Week – Source: www.securityweek.com
Source: www.securityweek.com – Author: Associated Press Norfolk Southern believes a software defect — not a hacker — was the cause of the widespread computer outage that...
Okta Says US Customers Targeted in Sophisticated Attacks – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Identity and access management solutions provider Okta warns that multiple customers based in the United States have been targeted in...
UK Boards Are Growing Less Concerned About Cyber-Risk – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Far fewer board members of UK companies are worried about cyber-risk than their global peers, according to a new study from...
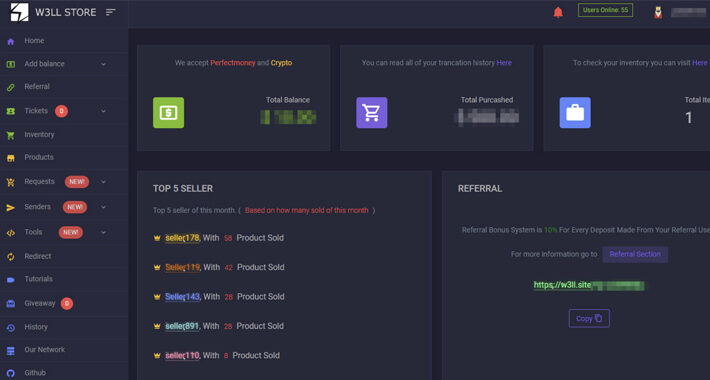
Experts Uncover Underground Phishing “Empire” W3LL – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Security researchers have uncovered a new covert phishing operation selling sophisticated tools used to target an estimated 56,000 Microsoft 365 accounts...
Crypto Casino Stake.com Back Online After $40m Heist – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Hackers have stolen over $40m in cryptocurrency from the self-styled “world’s leading betting platform,” the firm has revealed. Curaçao-headquartered Stake.com offers...
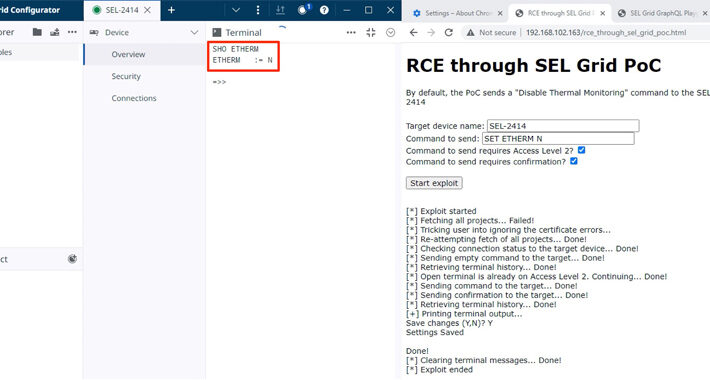
9 Alarming Vulnerabilities Uncovered in SEL’s Power Management Products – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 06, 2023THNVulnerability / ICS Nine security flaws have been disclosed in electric power management products made by Schweitzer Engineering Laboratories...
W3LL Store: How a Secret Phishing Syndicate Targets 8,000+ Microsoft 365 Accounts – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 06, 2023THNCyber Crime / Email Security A previously undocumented “phishing empire” has been linked to cyber attacks aimed at compromising...
Ukraine’s CERT Thwarts APT28’s Cyberattack on Critical Energy Infrastructure – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 06, 2023THNCyber Attack / Critical Infrastructure The Computer Emergency Response Team of Ukraine (CERT-UA) on Tuesday said it thwarted a...
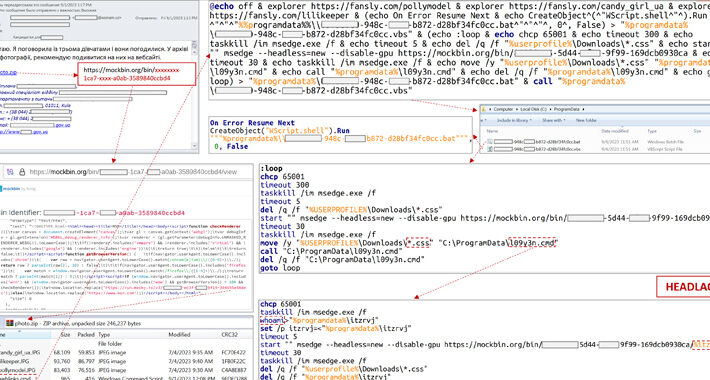
Coffee Meets Bagel says recent outage caused by destructive cyberattack – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams The Coffee Meets Bagel dating platform confirms last week’s outage was caused by hackers breaching the company’s systems and deleting...
Atlas VPN zero-day vulnerability leaks users’ real IP address – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas An Atlas VPN zero-day vulnerability affecting the Linux client leaks a user’s real IP address simply by visiting a website....
Crypto casino Stake.com loses $41 million to hot wallet hackers – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Image: Midjourney Online cryptocurrency casino Stake.com announced that its ETH/BSC hot wallets had been compromised to perform unauthorized transactions, with...
Chaes malware now uses Google Chrome DevTools Protocol to steal data – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The Chaes malware has returned as a new, more advanced variant that includes a custom implementation of the Google DevTools...
ASUS routers vulnerable to critical remote code execution flaws – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Three critical-severity remote code execution vulnerabilities impact ASUS RT-AX55, RT-AX56U_V2, and RT-AC86U routers, potentially allowing threat actors to hijack devices...
Continuous Security: PTaaS Bridges the Gap within Application Security – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sponsored by Outpost24 Pen testing, also known as “ethical hacking,” involves a team of cybersecurity professionals tasked to test the resilience of an...
Freecycle Confirms Data Breach Affecting Over 7 Million Users – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Madalina Popovici Freecycle, a global online platform promoting the exchange of used items, announced a significant data breach affecting over 7 million...
5 Ways Heimdal® Protects You From DNS Attacks – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Madalina Popovici As cyber-attacks continue to proliferate, it’s essential for organizations to stay ahead of the game when it comes to security....
Heimdal Announces Expansion into the Indian Market – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Danny Mitchell Mumbai, 31st August 2023 — Heimdal, a global leader in cybersecurity solutions, is thrilled to announce its official entry into...
Explainable AI: Empowering Advanced Bot Prevention Strategies – Source: securityboulevard.com
Source: securityboulevard.com – Author: Vikas Shetty In an era marked by unprecedented advancements in artificial intelligence (AI), the pursuit of “Explainable AI” has emerged as a...
GraphQL Vulnerabilities and Common Attacks: What You Need to Know – Source: securityboulevard.com
Source: securityboulevard.com – Author: Sarit Yerushalmi GraphQL is a powerful query language for APIs that has gained popularity in recent years for its flexibility and ability...
Clicked on a Phishing Email? All Is Not Lost – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt Phishing continues to be a bane of organizations. Phishing accounts for 36% of all data breaches, according to Verizon, and...
Takeaways from Our Roundtable at the Millennium Alliance – Source: securityboulevard.com
Source: securityboulevard.com – Author: Dylan Broxson A few days ago our team met with security leaders at an event hosted by the Millennium Alliance. Over the...
The Product Pulse – Source: securityboulevard.com
Source: securityboulevard.com – Author: Natalie Anderson Monthly Release Notes for August Looking to learn about Apptega’s monthly product updates? Well, you’re in the right place. Here’s...
BSides Cheltenham 2023 – James Stevenson – Identifying Rogue Android Devices: The World Of Android Attestation – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2023/09/bsides-cheltenham-2023-james-stevenson-identifying-rogue-android-devices-the-world-of-android-attestation/ Category & Tags: CISO Suite,Governance, Risk &...
Item Recycling Site Freecycle is Hit with a Massive Data Breach – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt Millions of people who use the Freecycle online forum to swap unwanted items may now have their passwords, email addresses,...
Navigating the XDR Landscape: Choosing the Right Solution through Independent Test Results – Source: securityboulevard.com
Source: securityboulevard.com – Author: SecureIQLab In the rapidly evolving digital landscape, organizations are confronted with the mounting challenge of safeguarding their networks, data, and assets against...
Geopolitical Warfare in the Digital Age: The NATO Summit Cyber Incursion – Source: securityboulevard.com
Source: securityboulevard.com – Author: Votiro Team Cybercrime, once chiefly associated with shadowy individuals seeking personal gains, has rapidly evolved into a formidable weapon of modern warfare....
Noname Security Aligns With OWASP on API Security Risks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard Noname Security has added full support for reducing the top ten application programming interface (API) security risks for 2023 as...
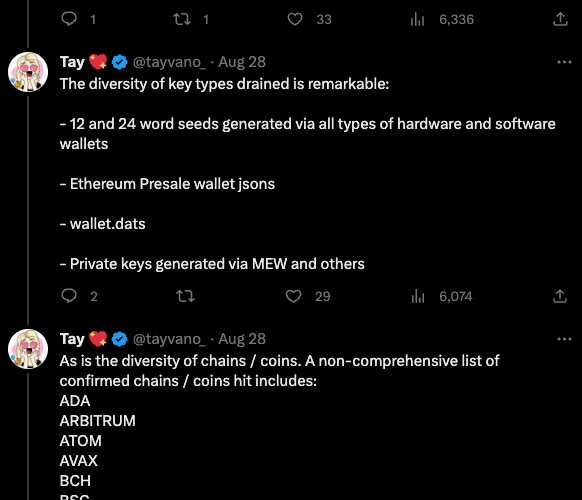
Experts Fear Crooks are Cracking Keys Stolen in LastPass Breach – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs In November 2022, the password manager service LastPass disclosed a breach in which hackers stole password vaults containing both encrypted and...
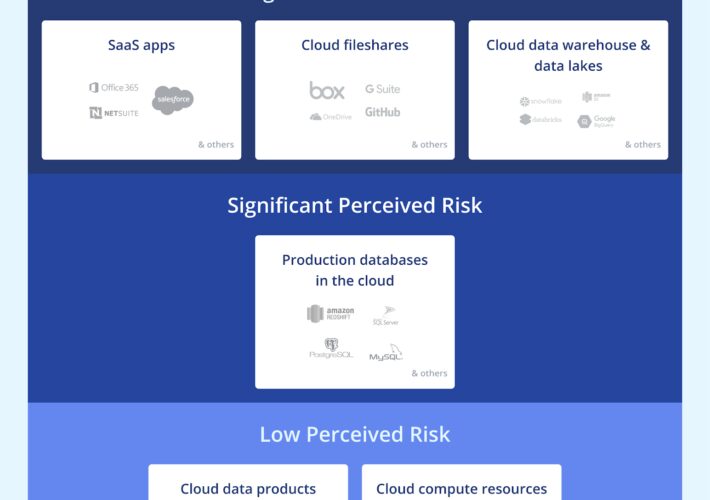
Zscaler Data Security Platform Takes on Symantec, CASB Tools – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cloud Access Security Brokers (CASB) , Data Loss Prevention (DLP) , Endpoint Security CEO Jay Chaudhry: In-Line Inspection, App-to-App Protection Aid...