Source: www.bleepingcomputer.com – Author: Sponsored by Outpost24
Pen testing, also known as “ethical hacking,” involves a team of cybersecurity professionals tasked to test the resilience of an organization’s security systems.
Unfortunately, traditional web application pen testing has limitations and often leaves organizations with gaps in their security. This is where Penetration Testing as a Service (PTaaS) comes into play, offering a comprehensive solution for continuous security monitoring .
In the rapidly evolving landscape of cybersecurity, organizations must stay ahead of the curve to protect their web applications to prevent vulnerabilities and attacks. But how do you choose the right security testing approach for your organization?
When Standard Pen Testing Doesn’t Meet the Mark
The cornerstone of any security program, manual penetration testing, is designed to identify potential vulnerabilities in your web applications by using techniques that attackers could use. While it’s essential for identifying existing weaknesses, this type of testing has drawbacks.
Pen testing is a labor-intensive and time consuming process that requires manual effort, which limits scalability and can lead to costly delays. Pen testers must often prioritize specific application or network system areas for testing due to time constraints.
This can lead to incomplete coverage, resulting in security loopholes not identified by the pen test. The main challenge of pen testing is that it does not offer continuous monitoring and fails to keep up with the constant changes in an application’s environment, making remediation efforts difficult. Thus, organizations are often left vulnerable to gaps in their security measures.
Key challenges of traditional pen testing:
- Skilled Resources: Difficulty hiring skilled resources is a major challenge, as pen testing requires specialized knowledge, experience, and expertise to perform accurate assessments of vulnerabilities.
- Time and Budget Constraints: Pen testing can be time-consuming and expensive, particularly when dealing with complex systems. Budget constraints may limit the extent and frequency of testing, potentially leaving vulnerabilities unaddressed.
- Inadequate Test Coverage: Ensuring comprehensive test coverage, as pen testers may overlook certain vulnerabilities or fail to simulate all possible attack scenarios, leaving the system exposed.
- Test Environment Configuration: Setting up an appropriate test environment that mirrors the production environment is crucial for accurate testing but can be difficult and time-consuming.
- Test Data Management: Managing and generating test data, as pen testers must create realistic data sets without compromising sensitive information.
- Rapidly Changing Technologies: With the continuous evolution of technologies, pen testers must constantly update their skills and knowledge to stay ahead of the curve and effectively identify potential security issues.
Scaling Web Application Security with PTaaS
PTaaS is an approach to application security testing that offers comprehensive coverage, frequent testing, automated processes, and integration with development processes.
By continuously monitoring web applications for vulnerabilities, PTaaS provides organizations with an effective way to safeguard against cyber-attacks and ensure their applications are secure.
PTaaS offers continuous security and a holistic view of AppSec, making it a great security service for organizations seeking comprehensive and ongoing protection for their digital assets.
Primary Benefits of PTaaS:
- Comprehensive coverage: PTaaS provides a holistic approach to security testing, covering a wide range of attack vectors and technologies.
- Cost-effectiveness: PTaaS can be more affordable than hiring a team of manual testers.
- Automation: By incorporating automated vulnerability scanning, PTaaS can efficiently identify vulnerabilities while reducing the time and effort required for manual processes.
- Continuous monitoring: provides ongoing security assessments, which helps organizations stay up to date with the latest threats.
- Integration with development processes & DevOps: can be integrated into the development lifecycle, enabling security measures to be incorporated throughout the software development process.
- Access to diverse skillset: provides organizations with access to a wide range of specialties and expertise, including application security experts and software developers, to ensure comprehensive coverage.
- Scalability: PTaaS is easily scalable, catering to organizations with multiple applications and projects, whereas traditional pen testing can be resource-intensive.
- Holistic approach: easily integrates with other security tools and systems..
Take a Look at PTaaS vs. Standard Web Application Pen Testing
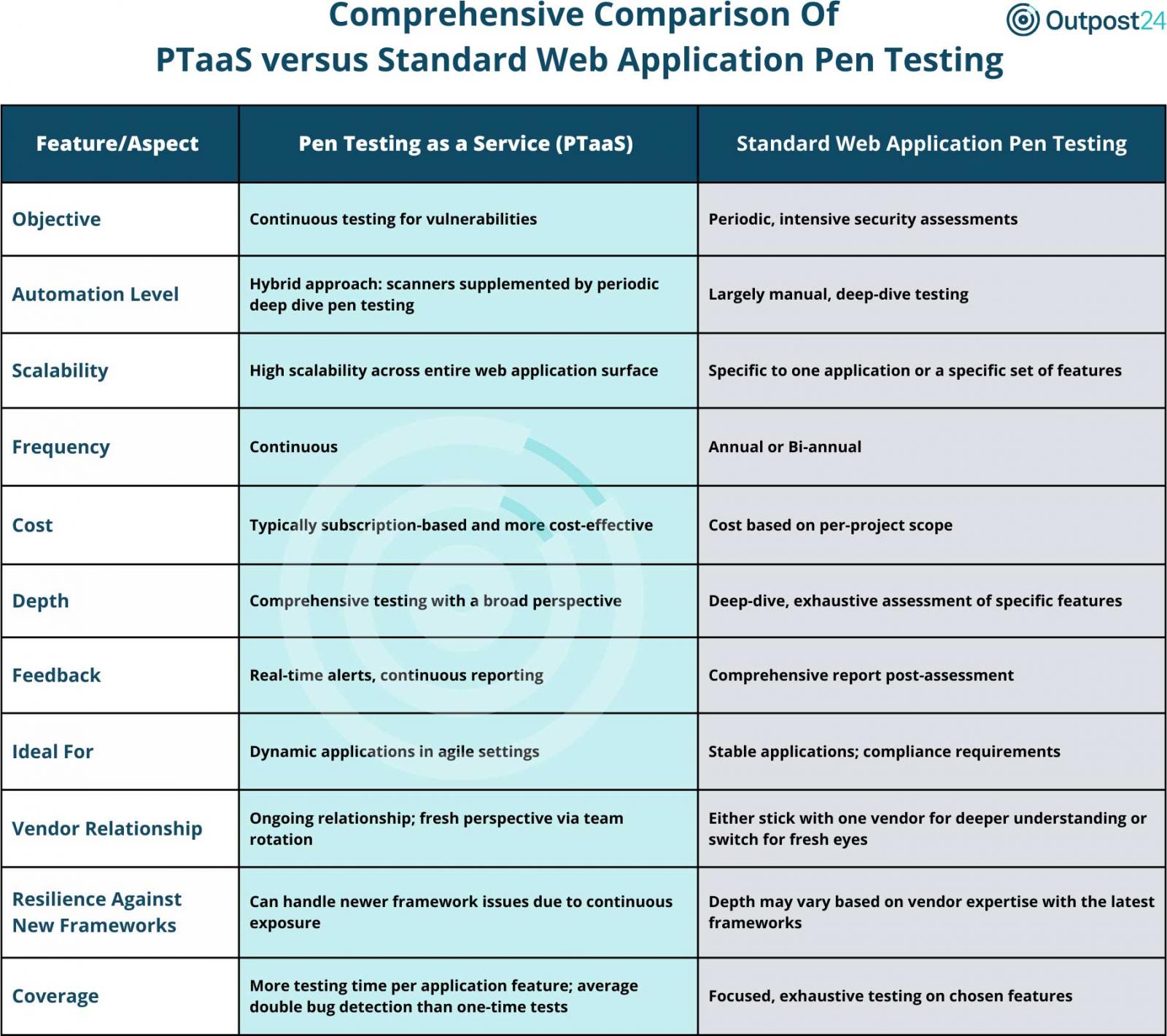
Traditional pen testing has its merits, but it falls short compared to PTaaS in several key areas:
- Frequency of testing: standard pen testing usually happens on an ad-hoc basis, while PTaaS enables continuous monitoring and frequent testing throughout the year.
- Lack of continuous monitoring: Traditional pen testing is not designed for ongoing monitoring, which could leave organizations exposed to new threats between tests.
- Scope of coverage: Traditional pen testing provides limited coverage, focusing primarily on manual processes, while PTaaS covers a wide range of attack vectors and technologies.
- Integration with development processes: Pen testing is typically performed after development is complete, while PTaaS can be integrated into the lifecycle for continual security checks.
- Reliance on manual processes: Pen testing relies heavily on manual processes, while PTaaS incorporates automated vulnerability scanning with manual testing to provide faster and more efficient results.
Application Processes that Should Be Using PTaaS
While once-yearly traditional pen testing may work for some organizations, the growing number of applications and release updates require a more robust solution. For example:
- Integrating security into DevOps: PTaaS seamlessly integrates with the development process, enabling continuous security testing throughout the software lifecycle. This approach ensures that vulnerabilities are identified and addressed at every stage, reducing the risk of security breaches early in the development cycle.
- Security to increase app performance & value: By identifying and addressing vulnerabilities early on, PTaaS can help improve application performance and overall value. By identifying and addressing vulnerabilities early on, PTaaS delivers high-performing, secure applications that enhance user experience and satisfaction.
- Multiple applications & projects that require continuous security: PTaaS is an ideal solution for organizations managing multiple applications and projects that require continuous security. Its scalability and continuous security monitoring capabilities cater to the diverse needs of such organizations, ensuring that their growing portfolio of applications remains safeguarded against emerging threats.
If you’re unsure where PTaaS or standard pen testing for web applications is best suited, see the chart below.
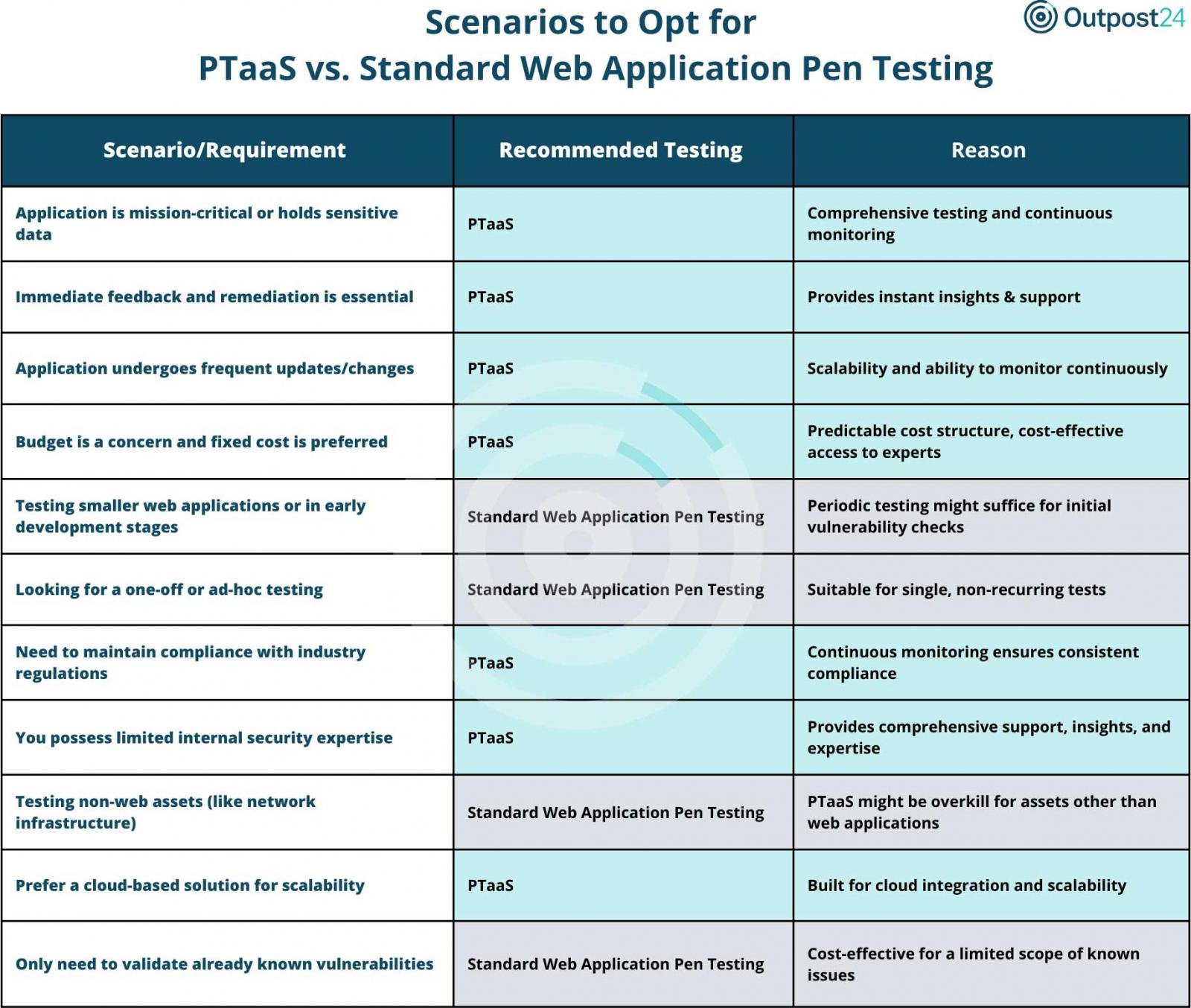
With its scalability, continuous monitoring capabilities, and holistic view of AppSec, PTaaS delivers a reliable solution for companies looking for comprehensive protection for their digital assets. Outpost24’s Pen Testing as a Service (PTaaS) is a powerful solution for organizations looking for comprehensive protection for their digital assets.
This cloud-based service provides continuous security, expert manual testing combined with automated vulnerability scanning, enabling organizations to detect and address security threats quickly and effectively.
Sponsored and written by Outpost24
Original Post URL: https://www.bleepingcomputer.com/news/security/continuous-security-ptaas-bridges-the-gap-within-application-security/
Category & Tags: Security – Security





















































