Source: – Author: 1 Browser fingerprinting is supposedly a more privacy-conscious tracking method, replacing personal information with more general data. But is it a valid promise?...
Month: August 2023
The grand theft of Jake Moore’s voice: The concept of a virtual kidnap – Source:
Source: – Author: 1 With powerful AI, it doesn’t take much to fake a person virtually, and while there are some limitations, voice-cloning can have some...
Quantum computing: Will it break crypto security within a few years? – Source:
Source: – Author: 1 Current cryptographic security methods watch out – quantum computing is coming for your lunch. Original Post URL: Category & Tags: – Views:...
Is backdoor access oppressive? – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Bills granting access to end-to-end encrypted systems, opportunity for cybercriminals, abuse by authority, human rights, and tech companies leaving the UK? Original...
Gathering dust and data: How robotic vacuums can spy on you – Source:
Source: – Author: 1 Mitigate the risk of data leaks with a careful review of the product and the proper settings. Original Post URL: Category &...
Dear all, What are some common subject lines in phishing emails? – Source:
Source: – Author: 1 Scammers exploit current ongoing events, account notifications, corporate communication, and a sense of urgency. Original Post URL: Category & Tags: – Views:...
What happens if AI is wrong? – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Responses generated by ChatGPT about individual people could be misleading or harmful or spill their personal information. What are the takeaways for...
8 common work-from-home scams to avoid – Source:
Source: – Author: 1 That ‘employer’ you’re speaking to may in reality be after your personal information, your money or your help with their illegal activities...
Child identity theft: how do I keep my kids’ personal data safe? – Source:
Source: – Author: 1 Why is kids’ personal information in high demand, how do criminals steal it, and what can parents do to help prevent child...
Protect yourself from ticketing scams ahead of the Premier League Summer Series USA Tour – Source:
Source: – Author: 1 There is a significant secondary marketplace where tickets can sell for several times their original value, opening the opportunity for scammers and...
Key findings from ESET Threat Report H1 2023 – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Here’s how cybercriminals have adjusted their tactics in response to Microsoft’s stricter security policies, plus other interesting findings from ESET’s new Threat...
The danger within: 5 steps you can take to combat insider threats – Source:
Source: – Author: 1 Some threats may be closer than you think. Are security risks that originate from your own trusted employees on your radar? Original...
How to combat the emergence of automated and AI-generated fraud – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kathryn Schneider The internet is abuzz with talk of the potential of generative AI and automation. But these advanced tools are also...
A Look Inside the Attacker’s Toolkit: DNS DDoS Attacks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Sharon Shirit DNS is a critical infrastructure for your online services, a DNS DDoS attack risks the availability of your services. Attackers...
Karma Catches Up to Global Phishing Service 16Shop – Source: securityboulevard.com
Source: securityboulevard.com – Author: BrianKrebs You’ve probably never heard of “16Shop,” but there’s a good chance someone using it has tried to phish you. A 16Shop...
New SEC Cybersecurity Rules and What It Means for Board Oversight – Source: securityboulevard.com
Source: securityboulevard.com – Author: Leigh Dow The SEC adopted new rules surrounding cybersecurity risk management, strategy, governance, and incident disclosure. As a CISO, this no doubt...
BSidesTLV 2023 – Elad Ernst – One Device To Rule Them All – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2023/08/bsidestlv-2023-elad-ernst-one-device-to-rule-them-all/ Category & Tags: CISO Suite,Governance, Risk &...
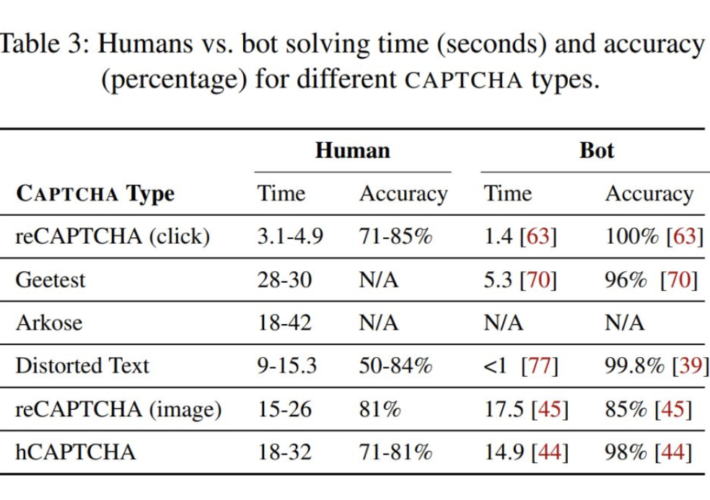
CAPTCHA: A Cost-Proof Solution, Not A Turing Test – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kevin Gosschalk Understanding the Inherent Limitations of CAPTCHAs At its core, a CAPTCHA (Completely Automated Public Turing Test to Tell Computers and...
Randall Munroe’s XKCD ‘Types of Solar Eclipse’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2023/08/randall-munroes-xkcd-types-of-solar-eclipse/ Category & Tags: Humor,Security Bloggers Network,Aerospace Humor,Astronomical...
The Week in Security: Researchers hack ‘unbreakable’ card-shuffling hardware, Discord.io shut after breach – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kate Tenerowicz Welcome to the latest edition of The Week in Security, which brings you the newest headlines from both the world...
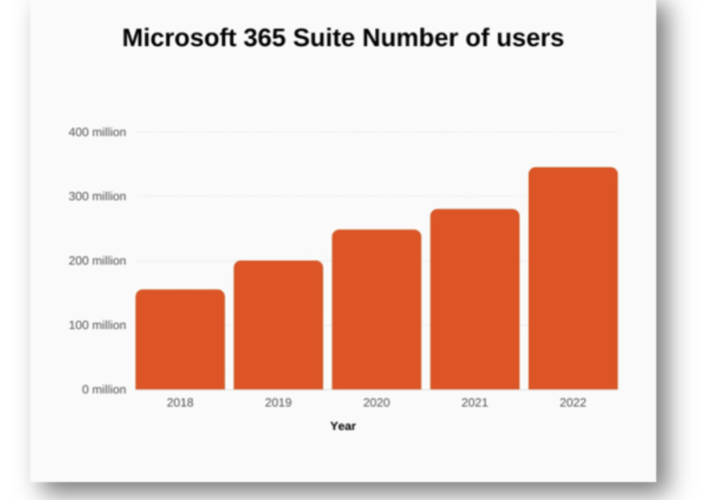
Adding File Security to Your Email Platform – Source: securityboulevard.com
Source: securityboulevard.com – Author: Votiro Team By John Masserini, Senior Research Analyst, TAG Cyber Since 2018, the user base of Microsoft Office 365 has steadily grown...
Malware Is Turning Windows Machines Into Proxies – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cybercrime as-a-service , Fraud Management & Cybercrime , Social Engineering Proxy App Is Covertly Installed Via Alluring Offers or Compromised Software...
LIVE Webinar | Why Data Security is the Foundation for Your Security Posture – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
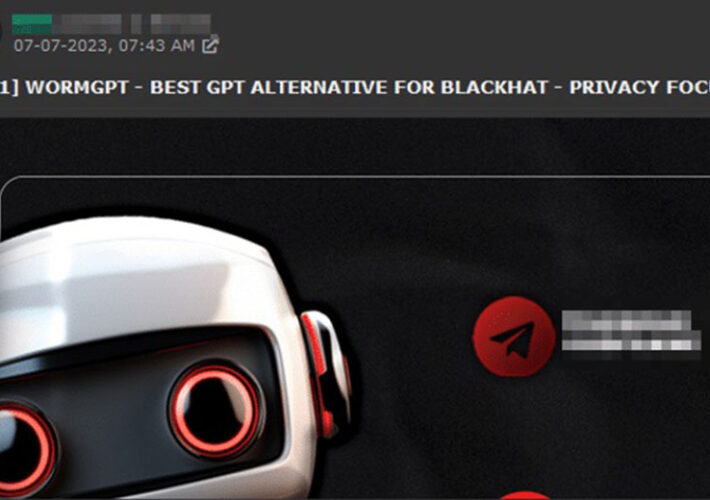
Inside the Rise of ‘Dark’ AI Tools – Scary, But Effective? – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development WormGPT, DarkGPT and Their Ilk Underdelivered – or Were Scams,...
Panel Discussion | Before & After AWS: Transforming Cloud’s Most Common Pitfalls into Progress – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Nate Kettlewell Principal, Application Security, Coalfire Nate Kettlewell is a specialist in information security, network engineering, and web application security. His...
LIVE Webinar | Straighten Up Your (Security) Posture: A Data Security Deep Dive – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
Breach Roundup: Raccoon Stealer Makes a Comeback – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cybercrime , Fraud Management & Cybercrime , Incident & Breach Response Also: QR Codes Used in Phishing Campaign; Belarus ISPs Used...
Cryptohack Roundup: Argentina Investigates WorldCoin – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cloud Access Security Brokers (CASB) , Cybercrime , Fraud Management & Cybercrime Also: Milk Sad Vulnerability, FBI Forfeiture, X Crypto Scams...
Sophos: ‘Royal’ Is Trying to Make Itself the King of Ransomware – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading John Shier of Sophos shares findings of a company report on “Royal,” a dangerous new variation of...
Israel-US Binational Industrial R&D Foundation to Invest $3.85M in Critical Infrastructure Cybersecurity Projects – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 TEL AVIV, Israel, Aug. 17, 2023 /PRNewswire/ — While the cybersecurity industry experienced record-breaking investments and continuous growth in recent years, most cyber...