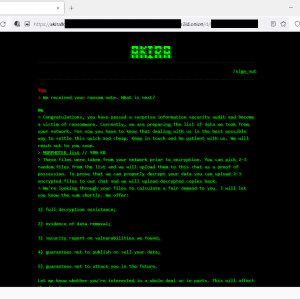
Source: securityaffairs.com – Author: Pierluigi Paganini The LockBit ransomware gang claims to have hacked Taiwan Semiconductor Manufacturing Company (TSMC). The LockBit ransomware group this week claimed...
Day: July 1, 2023
Avast released a free decryptor for the Windows version of the Akira ransomware – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Avast released a free decryptor for the Akira ransomware that can allow victims to recover their data without paying the...
Help spread the word about AZT – Source: securityboulevard.com
Source: securityboulevard.com – Author: Elliot Volkman Thank you for reading Adopting Zero Trust. When Neal and I started this (more so I told him to start...
Avoiding Insider Threats When Layoffs Occur – Source: securityboulevard.com
Source: securityboulevard.com – Author: Enzoic As layoffs continue in the tech sector, organizations need to be aware of insider threats associated with workforce reductions. As Josh Horwitz writes for...
Canada Day 2023 / La Fête du Canada 2023 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
What are account takeovers (ATOs)? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Sift Trust and Safety Team Account takeovers (ATOs) are a type of cyberattack, fraud risk, or identity theft that results in the...
BSidesSF 2023 – Tanya Janca – Secret Hunting – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
Human Risk Management vs Security Awareness: What’s the Difference? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Seed and Soil What is Security Awareness? Security Awareness is only one part of Human Risk Management. Its goal is to give...
Learn FAIR Quantitative Analysis for AI Risk in a Virtual Workshop – Source: securityboulevard.com
Source: securityboulevard.com – Author: Bernadette Dunn Artificial intelligence (AI) poses novel and powerful cyber threats both external and internal to your organization – but don’t fall...
Webinar Recap: Analyzing and Reporting Risks for MSPs and MSSPs: Introducing Seceon aiSecurity Score360 and aiSecurity BI360 with Seceon and partner, Logically – Source: securityboulevard.com
Source: securityboulevard.com – Author: William Toll Seceon and our partner Logically held a webinar to discuss the importance of scoring, benchmarking, and reporting risks, answering audits,...
Security Chiefs Take On IT Roles as More Infrastructure Moves Online – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: 1 Stay-at-home orders during the Covid-19 pandemic spurred new cloud computing and remote-technology setups, increasing company exposure to hackers. As a result,...
Connected Medical Devices—the Next Target for Ransomware Attacks – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: 1 The following is a guest article by Ryan Witt, Healthcare Cybersecurity Leader at Proofpoint The Internet of Medical Things, or IoMT,...
3 Ways to Build a More Skilled Cybersecurity Workforce – Source: www.darkreading.com
Source: www.darkreading.com – Author: Microsoft Security, Microsoft The Organisation for Economic Co-operation and Development (OECD), in partnership with Microsoft, recently released an extensive report analyzing over 400 million...
OTORIO Rolls Out Advanced Attack Graph Analysis for OT Security – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 TEL AVIV, Israel, June 28, 2023 /PRNewswire/ — OTORIO, the leading provider of operational technology (OT) cyber and digital risk management solutions, today announced...
Invary Raises $1.85M in Pre-Seed Funding to Close Critical Gap in Zero Trust Security – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 LAWRENCE, Kan., June 28, 2023 /PRNewswire/ — Invary, a cybersecurity pioneer focused on detecting hidden malware and preventing costly ransomware attacks, has raised pre-seed...
Mend.io Launches Inaugural Open Source Reliability Leaderboard – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 TEL AVIV, Israel and BOSTON, June 28, 2023 /PRNewswire/ — Mend.io, a leader in application security, released findings today from its latest report, the Mend.io Open...
AI-Enabled Voice Cloning Anchors Deepfaked Kidnapping – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer, Dark Reading An incident earlier this year in which a cybercriminal attempted to extort $1 million from an...
Thousands of Filipinos, Others Rescued From Forced Cybercrime Labor – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Thousands of workers in China, Indonesia, the Philippines, Vietnam, and a host of other countries who were tricked into performing...
US Patent Office Data Spill Exposes Trademark Applications – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading The US Patent and Trademark Office (USPTO) informed more than 60,000 trademark application filers that it mistakenly...
3 Tips to Increase Hybrid and Multicloud Security – Source: www.darkreading.com
Source: www.darkreading.com – Author: Microsoft Security, Microsoft Cloud technology is a powerful tool that facilitates collaboration among distributed workforces and allows businesses to quickly scale their...
Iranian APT Group Charming Kitten Updates Powerstar Backdoor – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime , Social Engineering Attackers Updating Malware to Conduct Espionage by Distributing Phishing...
Taiwan Semiconductor Denies LockBit’s $70M Hack Claim – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 3rd Party Risk Management , Fraud Management & Cybercrime , Governance & Risk Management Third-Party Supplier Hacked; TSMC Says Leak Only...
Live Webinar | Securing Financial Services in the Cloud – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Andre Labuschagne Global Account Manager, Skyhigh Security Andre is an accomplished professional in the cybersecurity field, currently serving as the Global...
Details of 1st Government Hack Are Disclosed, 20 Years Later – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime , Standards, Regulations & Compliance The 2003 Cyberattack Has Been Linked to...
HHS Tells Congress 100,000+ People Affected by MOVEit Hacks – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Breach Notification , Fraud Management & Cybercrime , Governance & Risk Management Department Says Attackers Gained Access to HHS Data Through...
7 ways to reduce security spend without compromising your security – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: In the current economic climate, CISOs face mounting pressure to reduce cyber security spending on account of factors like...
The Week in Ransomware – June 30th 2023 – Mistaken Identity – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams A case of mistaken identity and further MOVEit Transfer data breaches continue dominated the ransomware news cycle this week. This...
Hackers exploit zero-day in Ultimate Member WordPress plugin with 200K installs – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Hackers exploit a zero-day privilege escalation vulnerability in the ‘Ultimate Member’ WordPress plugin to compromise websites by bypassing security measures...
Twitter now forces you to sign in to view tweets – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Starting today, Twitter is no longer accessible on web and mobile apps if you don’t have an account, forcing all...
New proxyjacking attacks monetize hacked SSH servers’ bandwidth – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Attackers behind an ongoing series of proxyjacking attacks are hacking into vulnerable SSH servers exposed online to monetize them through...