Source: www.infosecurity-magazine.com – Author: 1 It’s a done deal. The EU’s Artificial Intelligence Act will become law. The European Parliament adopted the latest draft of the legislation...
Month: June 2023
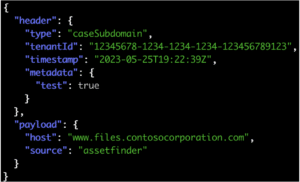
Researchers Uncover XSS Vulnerabilities in Azure Services – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Cybersecurity experts at Orca Security have identified two critical cross-site scripting (XSS) vulnerabilities in Microsoft Azure services. The flaws, which exploited...
#InfosecurityEurope: (ISC)² and CIISec Release Guide to Inclusive Language in Cybersecurity – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Ahead of Infosecurity Europe, (ISC)² and the Chartered Institute of Information Security (CIISec) have released a new guide to inclusive language...
#InfosecurityEurope: Cyber Leaders’ Plea to Tackle the Industry’s Mental Health Crisis – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Unsustainable pressures are being placed on cyber leaders and professionals’ mental health because of a combination of factors, such as the...
Europol Warns of Metaverse and AI Terror Threat – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 New and emerging technologies like conversational AI, deepfakes and the metaverse could be utilized by terrorists and extremists to radicalize and...
MFA Bypass Kits Account For One Million Monthly Messages – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Threat actors continued to evolve their tactics to sidestep user defenses in 2022, with multi-factor authentication (MFA) bypass kits accounting for...
No Zero-Days but PGM Flaws Cause Patch Tuesday Concern – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 System administrators breathed a sigh of relief yesterday after Microsoft issued a relatively light patch update round, with no zero-day vulnerabilities and...
It’s Official – FedRAMP has moved to Rev. 5 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jenn Sherman As of May 30, 2023, FedRAMP has officially approved and adopted the new Rev. 5 baselines – aligning with the...
Your Personal Data Sold to US Intelligence Agencies – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings Warrant not needed if info bought from brokers. An 18-month-old secret report—recently declassified—“raises significant issues related to privacy and civil...
Attacker Infrastructure: How Hackers Build It and How to Use It Against Them – Source: securityboulevard.com
Source: securityboulevard.com – Author: HYAS Hackers often spend weeks or months lurking on a target network to prepare for an eventual cyberattack. They will attempt to...
Tracking Patch Tuesday Vulnerabilities – Source: securityboulevard.com
Source: securityboulevard.com – Author: Flashpoint Intel Team June 2023 While most security vendors mainly focus on Microsoft releases on Patch Tuesday, our Flashpoint VulnDB team closely...
The Pros and Cons of reCAPTCHA Enterprise – Source: securityboulevard.com
Source: securityboulevard.com – Author: Heidi Anderson Google’s web security service, reCAPTCHA, is seemingly ubiquitous on the internet. Virtually anyone who has logged into one digital account...
AWS Expands Cloud Security Services Portfolio – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard Amazon Web Services (AWS) this week added a bevy of offerings and capabilities to its cloud security portfolio as part...
Unifying Your Cybersecurity Posture: A Guide to Assessing Your Enterprise Maturity – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kanika Thapar As technology relentlessly progresses, we witness a continuous stream of newer, more innovative tools replacing their antiquated counterparts. Rotary phones...
BSidesSF 2023 – Ben Schmerler – What I Learned About Security Working Minimum Wage At Hollywood Video – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
Improving Performance and Scalability: Updates and Lessons from Inspector, Our End-to-End Testing Solution – Source: securityboulevard.com
Source: securityboulevard.com – Author: emmaline Overview In a previous article titled Inspector or: How I Learned to Stop Worrying and Love Testing in Prod, we discussed...
CISA Instructs Federal Agencies to Secure Internet-Exposed Devices – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The US Cybersecurity and Infrastructure Security Agency (CISA) is requiring federal agencies to secure the network management interfaces of certain...
Hundreds of Thousands of eCommerce Sites Impacted by Critical Plugin Vulnerability – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Hundreds of thousands of ecommerce websites could be exposed to attacks due to a critical vulnerability in the WooCommerce Stripe...
Threat Intelligence Firm Silent Push Launches With $10 Million in Seed Funding – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Silent Push, a startup that describes itself as a detection-focused threat intelligence company, launched on Wednesday with $10 million in...
Chrome 114 Update Patches Critical Vulnerability – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Google on Tuesday announced a new Chrome 114 update that resolves five vulnerabilities, including four critical- and high-severity bugs reported...
SAP Patches High-Severity Vulnerabilities With June 2023 Security Updates – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire SAP on Tuesday announced the release of eight new security notes as part of its June 2023 Security Patch Day,...
ICS Patch Tuesday: Siemens Addresses Over 180 Third-Party Component Vulnerabilities – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Siemens and Schneider Electric on Tuesday released a total of 16 advisories addressing well over 200 vulnerabilities affecting their industrial...
Spotify Fined $5 Million for Breaching EU Data Rules – Source: www.securityweek.com
Source: www.securityweek.com – Author: AFP Music streaming giant Spotify was on Tuesday fined 58 million kronor ($5.4 million) for not properly informing users on how data...
Proofpoint’s 2023 Human Factor Report: Threat Actors Scale and Commoditize Uncommon Tools and Techniques – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: 1 New research provides an in-depth analysis of the modern attack chain and today’s biggest threats SUNNYVALE, Calif., June 14, 2023 –...
New phishing and business email compromise campaigns increase in complexity, bypass MFA – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Cedric Pernet Read the technical details about a new AiTM phishing attack combined with a BEC campaign as revealed by Microsoft, and...
Cyberattacks surge to 61% of small and medium-sized businesses, says study – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Megan Crouse on June 13, 2023, 5:07 PM EDT Cyberattacks surge to 61% of small and medium-sized businesses, says study A poll...
Hiring kit: Cryptographer – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: A cryptographer uses their expertise in mathematics and computer science to develop algorithms, ciphers and other encryption systems to protect sensitive data....
Microsoft Patch Tuesday, June 2023 Edition – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs Microsoft Corp. today released software updates to fix dozens of security vulnerabilities in its Windows operating systems and other software. This...
Spotify Fined 5 Million Euros for GDPR Violations – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 General Data Protection Regulation (GDPR) , Standards, Regulations & Compliance Online Music Streamer Will Appeal Decision From Swedish Data Protection Authority...
Thales to Buy Tesserent for $119.1M to Aid Australian Growth – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Managed Security Service Provider (MSSP) , Security Awareness Programs & Computer-Based Training Tesserent’s $125.1M Business Will...