Source: www.techrepublic.com – Author: Cedric Pernet
Read the technical details about a new AiTM phishing attack combined with a BEC campaign as revealed by Microsoft, and learn how to mitigate this threat.

A report from the Microsoft Defender Experts reveals a new multi-staged adversary in the middle phishing attack combined with a business email compromise attack targeting banking and financial institutions. The complex attack abuses trusted relationships between vendors, suppliers and more organizations involved in financial transactions.
Jump to:
- Stage one: Launching an AiTM phishing attack
- Stage two: Modifying the user’s account
- Stage three: BEC campaign starts
- How to stay safe from this cybersecurity threat
Stage one: Launching an AiTM phishing attack
AiTM attacks are operations in which a bad actor intercepts and modifies communications between two parties, typically a user and a legitimate authentication service, to steal sensitive or financial information, such as log-in credentials and credit card data. It might also be used to bypass multifactor authentication by stealing users’ session cookies.
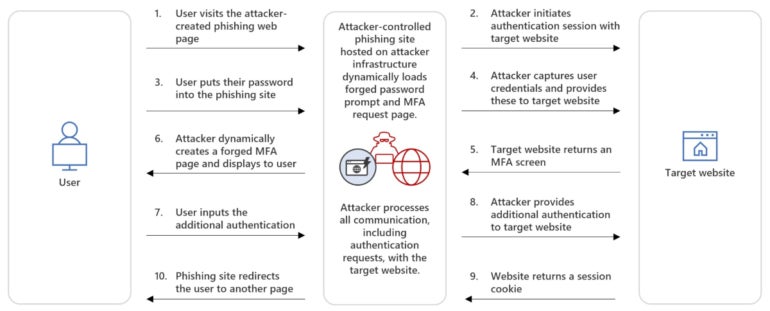
While previous AiTM attacks generally used reverse proxy techniques to handle the traffic between the user and the authentication service, this time the attackers used an indirect proxy method. This technique is slightly different as the attacker controls everything directly from a phishing website that mimics the sign-in page of the targeted service. The website processes all communication, including authentication requests, with the target.
The user is enticed to visit the phishing page, enters their credentials and fills in the additional MFA authentication, which is a fake MFA request coming directly from the attackers. In the background and straight from the phishing server, the attacker initiates communication with the targeted service and enters the valid users’ credentials and then the MFA information. The user is being redirected to another page at that moment, while the attacker receives a valid session cookie impersonating the user (Figure A).
Figure A
In the attack reported by Microsoft and run by a threat actor dubbed Storm-1167, the AiTM link is sent to the victim through email. The phishing email impersonates one of the target’s trusted vendors to appear more legitimate and blend with legitimate email traffic and bypass detections, especially when an organization has policies to automatically allow emails from trusted vendors.
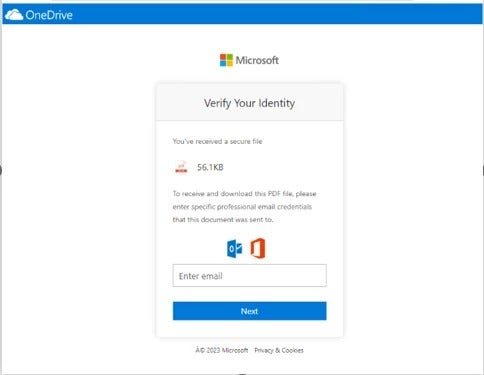
In Microsoft’s example, the threat actor abused Canva’s legitimate graphic design platform to host a page showing a fake OneDrive document leading to the phishing URL (Figure B).
Figure B
Stage two: Modifying the user’s account
Once the attacker was in possession of a valid session cookie, they started accessing email conversations and documents hosted in the cloud and generated a new access token in order to use the stolen session for longer.
Then, the Storm-1167 group added a new MFA method to the stolen user’s account for future use — once again showing its concerns for staying longer in the environment. Since adding a new MFA method does not require re-authentication, the attackers quietly added OneWaySMS, an SMS-based one-time password authentication service.
The final step for the attacker at this stage was to create new inbox rules to move all incoming emails on the user’s mailbox to its archive folder and mark all the emails as read.
Stage three: BEC campaign starts
Next, the attacker — in full control of the target’s mailbox — initiated a massive phishing campaign of more than 16,000 emails, focusing on the user’s contacts and distribution lists, all of which were identified in previous email threads from the user’s mailbox.
After the phishing emails were sent, the attacker monitored the mailbox and responded to the recipients, who answered with doubts about the phishing email, to falsely confirm that the email was legitimate. Undelivered and out-of-office replies were deleted.
This entire activity enabled the attacker to collect more valid email accounts in different organizations and also initiate the BEC fraud (Figure C).
Figure C
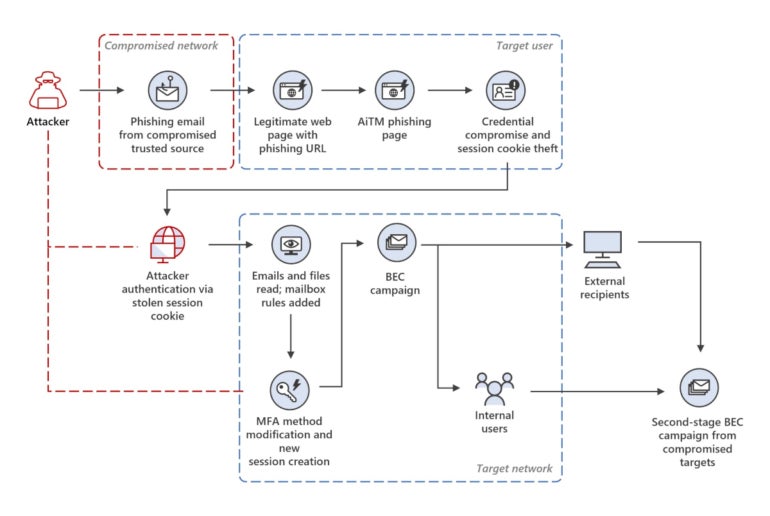
While Microsoft does not go further in explaining the BEC fraud from the threat actor, it is expected at this point that the actor would impersonate one of the people involved in regular money transfer operations to have the victim send the money to a cybercriminal-owned banking account.
How to stay safe from this cybersecurity threat
Since the initial attack vector is a phishing email, it is necessary to deploy mailbox security solutions that can detect phishing attempts and raise alerts on emails coming from outside of the company when they follow suspicious behavioral patterns.
Email box configuration changes should also be carefully monitored. Email boxes suddenly starting to send a massive number of emails or suddenly forwarding a lot of emails to another email address should raise alerts and be analyzed carefully.
When possible, email access should be restricted to trusted IP addresses via corporate virtual private networks, for example; MFA should be deployed on those services. In case such restrictions cannot be deployed, careful monitoring of every sign-in operation should be done to detect any attempts that show anomalies.
SEE: Best VPNs for small businesses in 2023 (TechRepublic)
Deploying security solutions that enable the profiling of users is also recommended. Any unusual characteristic of a sign-in operation from a user will raise alerts and can be analyzed with such solutions.
As for the BEC fraud, any change regarding money transactions should be carefully investigated. If a trusted partner suddenly asks to change a wire transfer destination, the request should be investigated with that partner through a communication channel other than email, and preferably not using computers — perhaps phones instead — in case the attacker planted malware on the target’s computer and could intercept all communications.
Disclosure: I work for Trend Micro, but the views expressed in this article are mine.
Original Post URL: https://www.techrepublic.com/article/microsoft-news-business-email-compromise-attacks-phishing/
Category & Tags: Cloud,Microsoft,Networking,Security,adversary-in-the-middle phishing,azure active directory,business email compromises,microsoft 365 defender,Microsoft Defender – Cloud,Microsoft,Networking,Security,adversary-in-the-middle phishing,azure active directory,business email compromises,microsoft 365 defender,Microsoft Defender
Views: 0




















































