Source: www.securityweek.com – Author: Ionut Arghire The US Cybersecurity and Infrastructure Security Agency (CISA) is requiring federal agencies to secure the network management interfaces of certain...
Day: June 14, 2023
Hundreds of Thousands of eCommerce Sites Impacted by Critical Plugin Vulnerability – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Hundreds of thousands of ecommerce websites could be exposed to attacks due to a critical vulnerability in the WooCommerce Stripe...
Threat Intelligence Firm Silent Push Launches With $10 Million in Seed Funding – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Silent Push, a startup that describes itself as a detection-focused threat intelligence company, launched on Wednesday with $10 million in...
Chrome 114 Update Patches Critical Vulnerability – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Google on Tuesday announced a new Chrome 114 update that resolves five vulnerabilities, including four critical- and high-severity bugs reported...
SAP Patches High-Severity Vulnerabilities With June 2023 Security Updates – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire SAP on Tuesday announced the release of eight new security notes as part of its June 2023 Security Patch Day,...
ICS Patch Tuesday: Siemens Addresses Over 180 Third-Party Component Vulnerabilities – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Siemens and Schneider Electric on Tuesday released a total of 16 advisories addressing well over 200 vulnerabilities affecting their industrial...
Spotify Fined $5 Million for Breaching EU Data Rules – Source: www.securityweek.com
Source: www.securityweek.com – Author: AFP Music streaming giant Spotify was on Tuesday fined 58 million kronor ($5.4 million) for not properly informing users on how data...
Proofpoint’s 2023 Human Factor Report: Threat Actors Scale and Commoditize Uncommon Tools and Techniques – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: 1 New research provides an in-depth analysis of the modern attack chain and today’s biggest threats SUNNYVALE, Calif., June 14, 2023 –...
New phishing and business email compromise campaigns increase in complexity, bypass MFA – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Cedric Pernet Read the technical details about a new AiTM phishing attack combined with a BEC campaign as revealed by Microsoft, and...
Cyberattacks surge to 61% of small and medium-sized businesses, says study – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Megan Crouse on June 13, 2023, 5:07 PM EDT Cyberattacks surge to 61% of small and medium-sized businesses, says study A poll...
Hiring kit: Cryptographer – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: A cryptographer uses their expertise in mathematics and computer science to develop algorithms, ciphers and other encryption systems to protect sensitive data....
Microsoft Patch Tuesday, June 2023 Edition – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs Microsoft Corp. today released software updates to fix dozens of security vulnerabilities in its Windows operating systems and other software. This...
Spotify Fined 5 Million Euros for GDPR Violations – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 General Data Protection Regulation (GDPR) , Standards, Regulations & Compliance Online Music Streamer Will Appeal Decision From Swedish Data Protection Authority...
Thales to Buy Tesserent for $119.1M to Aid Australian Growth – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Managed Security Service Provider (MSSP) , Security Awareness Programs & Computer-Based Training Tesserent’s $125.1M Business Will...
Live Webinar | Reimagining Network Security: Exploring the Power of Security Service Edge (SSE) – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Doug Browne Director for SaaS Security (SSE, Duo and Cloud Security), APJC at Cisco Systems Doug Browne has over 24 years’...
Gozi Host ‘Virus’ Sentenced to 3 Years in US Prison – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Mihai Ionut Paunescu Provided ‘Bulletproof Hosting’ for Trojans Rashmi Ramesh (rashmiramesh_) • June 13, 2023 A Romanian national who...
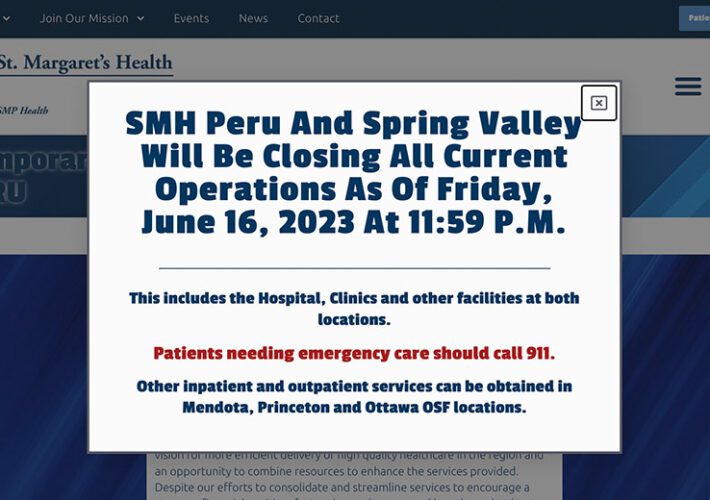
Rural Healthcare Provider Closing Due in Part to Attack Woes – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Healthcare , Industry Specific St. Margaret’s Health Is Permanently Shutting Hospitals and Clinics Marianne Kolbasuk McGee...
New Golang-based Skuld Malware Stealing Discord and Browser Data from Windows PCs – Source:thehackernews.com
Source: thehackernews.com – Author: . Jun 14, 2023Ravie LakshmananCyber Threat / Malware A new Golang-based information stealer called Skuld has compromised Windows systems across Europe, Southeast...
Where from, Where to — The Evolution of Network Security – Source:thehackernews.com
Source: thehackernews.com – Author: . Jun 14, 2023The Hacker NewsThreat Intel / Network Security For the better part of the 90s and early aughts, the sysadmin...
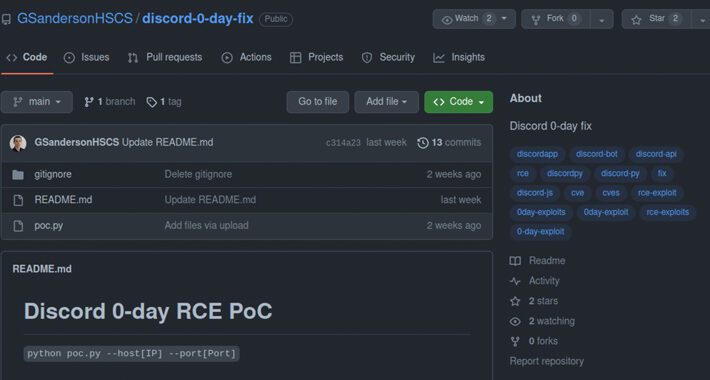
Fake Researcher Profiles Spread Malware through GitHub Repositories as PoC Exploits – Source:thehackernews.com
Source: thehackernews.com – Author: . Jun 14, 2023Ravie LakshmananMalware / Zero-Day At least half of dozen GitHub accounts from fake researchers associated with a fraudulent cybersecurity...
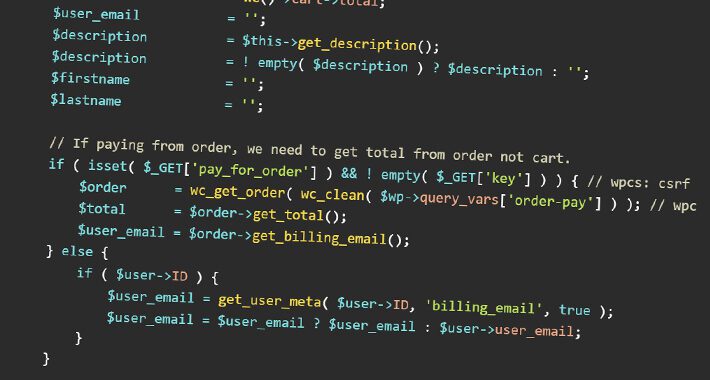
Critical Security Vulnerability Discovered in WooCommerce Stripe Gateway Plugin – Source:thehackernews.com
Source: thehackernews.com – Author: . Jun 14, 2023Ravie LakshmananWebsite Security / Hacking A security flaw has been uncovered in the WooCommerce Stripe Gateway WordPress plugin that...
Microsoft Releases Updates to Patch Critical Flaws in Windows and Other Software – Source:thehackernews.com
Source: thehackernews.com – Author: . Jun 14, 2023Ravie LakshmananPatch Tuesday / Vulnerability Microsoft has rolled out fixes for its Windows operating system and other software components...
Agencies Are Compelled to Secure All Internet-exposed Equipment by CISA Orders – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Andreea Chebac The American Cybersecurity & Infrastructure Security Agency (CISA) issued on June 13, 2023, a binding operational directive (BOD) requiring federal...
British watchdog Ofcom latest victim of MOVEit attack
British television watchdog Ofcom is the latest victim of a supply chain attack against document transfer service MOVEit. The cyber attack against MOVEit saw Russian ransomware...
Cycode Launches CI/CD Pipeline Monitoring Solution (Cimon) to Prevent Supply Chain Attacks – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 SAN FRANCISCO, June 12, 2023 – Cycode, the leading application security platform, today announced the launch of Cimon, a seamless solution that enhances the...
Analysis: Social Engineering Drives BEC Losses to $50B Globally – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributor, Dark Reading Business email compromise (BEC) continues to evolve on the back of sophisticated targeting and social engineering, costing...
Chinese Threat Actor Abused ESXi Zero-Day to Pilfer Files From Guest VMs – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer, Dark Reading A Chinese cyber-espionage group that researchers previously have spotted targeting VMware ESXi hosts has quietly been...
Popular Apparel, Clothing Brands Being Used in Massive Phishing Scam – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Threat actors have been impersonating more than 100 apparel, clothing, and footwear brands such as Nike, New...
Harness the Power of PKI to Battle Data Breaches – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 Identity is the key to unlocking zero-trust environments, but it is also the key to a lucrative payday for cybercriminals selling...
How Security Leaders Should Approach Cybersecurity Startups – Source: www.darkreading.com
Source: www.darkreading.com – Author: Ross Haleliuk , Product Leader and Head of Product, LimaCharlie Security leaders are tired of aggressive sales tactics, and cybersecurity companies must...