Source: www.securityweek.com – Author: Eduard Kovacs SecurityWeek is publishing a weekly cybersecurity roundup that provides a concise compilation of noteworthy stories that might have slipped under...
Day: June 9, 2023
Blackpoint Raises $190 Million to Help MSPs Combat Cyber Threats – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Cybersecurity company Blackpoint Cyber this week announced that it has raised $190 million in a growth funding round led by...
Google Introduces SAIF, a Framework for Secure AI Development and Use – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend The Google SAIF (Secure AI Framework) is designed to provide a security framework or ecosystem for the development, use and...
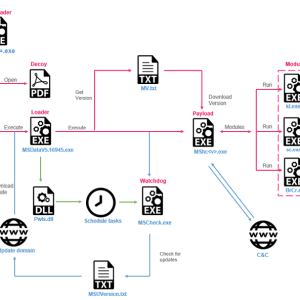
‘Asylum Ambuscade’ Group Hit Thousands in Cybercrime, Espionage Campaigns – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire A threat actor tracked as ‘Asylum Ambuscade’ has been engaging in both cybercrime and espionage campaigns for roughly three years,...
Evidence Suggests Ransomware Group Knew About MOVEit Zero-Day Since 2021 – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Newly uncovered evidence suggests that cybercriminals have known about the recently patched MOVEit Transfer zero-day vulnerability since mid-2021. The zero-day...
SaaS Ransomware Attack Hit Sharepoint Online Without Using a Compromised Endpoint – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend Cybersecurity firm Obsidian has observed a successful ransomware attack against Sharepoint Online (Microsoft 365) via a Microsoft Global SaaS admin...
Google Cloud Now Offering $1 Million Cryptomining Protection – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Google on Thursday announced that it is offering up to $1 million in financial protection to cover expenses associated with...
Democrats and Republicans Are Skeptical of US Spying Practices, an AP-NORC Poll Finds – Source: www.securityweek.com
Source: www.securityweek.com – Author: Associated Press As it pushes to renew a cornerstone law that authorizes major surveillance programs, the Biden administration faces an American public...
DOS Attacks Dominate, but System Intrusions Cause Most Pain – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer, Dark Reading Denial-of-service attacks continued to dominate the threat landscape in 2022, but breaches — those security incidents...
Brand-New Security Bugs Affect All MOVEit Transfer Versions – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer, Dark Reading Just days after Progress Software patched a widely exploited zero-day vulnerability in its MOVEit Transfer app,...
‘Asylum Ambuscade’ Cyberattackers Blend Financial Heists & Cyber Espionage – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading Researchers have linked a series of financially motivated attacks and a group of advanced persistent...
3 Elite Communication Skills to Help Security Pros Get Projects Funded – Source: www.darkreading.com
Source: www.darkreading.com – Author: Steve Shelton, CEO, Green Shoe Consulting This example scenario was built using real-world insights from Fred Kwong, chief information security officer at...
Cl0P Gang Sat on Exploit for MOVEit Flaw for Nearly 2 Years – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer, Dark Reading Turns out the Cl0p ransomware group sat on a zero-day vulnerability it discovered in Progress Software’s...
South African Female Students Offered Cyber Scholarship – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading A scholarship is to be offered to women of color in South Africa, to enable them to...
5 Tips for Modernizing Your Security Operations Center Strategy – Source: www.darkreading.com
Source: www.darkreading.com – Author: Andrew Hollister, CISO, LogRhythm; VP, LogRhythm Labs Investing time, money, or resources to improve security maturity, increase resilience against cyberattacks, and lower...
How Continuous Monitoring and Threat Intel Can Help Prevent Ransomware – Source: www.darkreading.com
Source: www.darkreading.com – Author: Microsoft Security, Microsoft Given the number of cybersecurity tools available on the market today, it’s easy for security leaders to become overwhelmed....
Firm study predicts big spends on generative AI – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Karl Greenberg Image: Tierney/Adobe Stock Software-as-service spend management software firm G2 reported that products with artificial intelligence functionality — particularly large language...
BBC, British Airways, Boots hit with hackers’ ultimatum after suffering MOVEit supply-chain attack – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Franklin Okeke Image: SomYuZu/Adobe Stock British Airways, BBC and Boots have all been served an ultimatum after they were hit with a...
Duo vs Microsoft Authenticator (2023): In-depth comparison – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Franklin Okeke Two-factor authentication, which is a form of multi-factor authentication, has emerged as a crucial security measure for organizations to enhance...
Russians charged with hacking Mt. Gox exchange and operating BTC-e – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Two Russian nationals have been charged with the hack of the cryptocurrency exchange Mt. Gox in 2011 and money laundering....
Japanese Pharmaceutical giant Eisai hit by a ransomware attack – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini This week, the Japanese pharmaceutical giant Eisai has taken its systems offline in response to a ransomware attack. Eisai is...
Clop ransomware gang was testing MOVEit Transfer bug since 2021 – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Researchers discovered that the Clop ransomware gang was looking for a zero-day exploit in the MOVEit Transfer since 2021. Kroll...
Stealth Soldier backdoor used is targeted espionage attacks in Libya – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Researchers detected a cyberespionage campaign in Libya that employs a new custom, modular backdoor dubbed Stealth Soldier. Experts at the...
Researchers published PoC exploit code for actively exploited Windows elevation of privilege issue – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Researchers published an exploit for an actively exploited Microsoft Windows vulnerability tracked as CVE-2023-29336. The Microsoft Windows vulnerability CVE-2023-29336 (CVSS score 7.8)...
Barracuda Urges Replacing — Not Patching — Its Email Security Gateways – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs It’s not often that a zero-day vulnerability causes a network security vendor to urge customers to physically remove and decommission an...
Weekly Update 351 – Source: www.troyhunt.com
Source: www.troyhunt.com – Author: Troy Hunt I spent most of this week’s update on the tweaking I went through with Azure’s API Management service and then...
Asylum Ambuscade: crimeware or cyberespionage? – Source: www.welivesecurity.com
Source: www.welivesecurity.com – Author: Matthieu Faou A curious case of a threat actor at the border between crimeware and cyberespionage 8 Jun 2023 – 11:30AM A...
Cyera Taps Microsoft OpenAI Service to Improve Data Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard Cyera this week revealed it integrated its namesake data security platform with the Microsoft Azure OpenAI cloud service to enable...
Cybersecurity Insights with Contrast CISO David Lindner | 6/9 – Source: securityboulevard.com
Source: securityboulevard.com – Author: David Lindner, Director, Application Security Insight #1 ” Treat AI-generated code as inaccurate and insecure from the start and make sure it...
API Security Reconnaissance As A Service using Noname Recon – Source: securityboulevard.com
Source: securityboulevard.com – Author: Filip Verloy, Noname Security & Graham Rowe, Avord UK Avord, a cybersecurity services and solutions organization based in the UK, is working...