Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer, Dark Reading Taiwan Semiconductor Manufacturing Company (TSMC) — one of Apple’s biggest semiconductor suppliers — on Friday blamed...
Month: June 2023
Mobile Cyberattacks Soar, Especially Against Android Users – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer, Dark Reading Attackers are increasingly targeting users through their mobile devices, attacking vulnerabilities in services that are built into...
Iran-Linked APT35 Targets Israeli Media With Upgraded Spear-Phishing Tools – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dan Raywood, Senior Editor, Dark Reading The Iran-linked threat group known as APT35 (aka Charming Kitten, Imperial Kitten, or Tortoiseshell) has updated its cyberattack arsenal with...
African Nations Face Escalating Phishing & Compromised Password Cyberattacks – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dan Raywood, Senior Editor, Dark Reading Cyberattacks against large enterprises in African nations ramped up in 2022, with Kenyan businesses reporting an 82%...
Russian Hacktivist Platform ‘DDoSia’ Grows Exponentially – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading After being launched by Russian hacktivist group “NoName057(16)” in the summer of 2022 and quickly gaining a...
Make Diversity the ‘How,’ Not the ‘What,’ of Cybersecurity Success – Source: www.darkreading.com
Source: www.darkreading.com – Author: Ericka Chickowski, Contributing Writer, Dark Reading As more organizations try to dovetail diversity, equity, and inclusion (DEI) efforts with the broader business...
Perception Point Unveils AI Model to Thwart Generative AI-Based BEC Attacks – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 (Tel Aviv, Israel – June 29, 2023) — Perception Point, a leading provider of advanced threat prevention across digital communication channels, today...
CISA BOD 23-01: What Agencies Need to Know About Compliance – Source: www.darkreading.com
Source: www.darkreading.com – Author: Song Pang, Senior VP of Engineering, NetBrain By April, all federal agencies were required to begin complying with a new mandate from...
Russian Cybersecurity Executive Arrested for Alleged Role in 2012 Megahacks – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs Nikita Kislitsin, formerly the head of network security for one of Russia’s top cybersecurity firms, was arrested last week in Kazakhstan...
‘Wagner Mercenary’ Hackers Destroy Russian Satellite Comms – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings Dozor-Teleport hack, vandalism and data breach. But is it a Ukrainian false flag op? Russian satellite communications provider Dozor-Teleport has...
Vendor Risk Assessments: 3 Common Mistakes to Avoid – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richa Tiwari Few organizations can perform their daily tasks and operations without vendors and third-party partners. And even if they could, successful...
Applying Zero-Trust Principles: Case Studies and Lessons From the Field – Source: securityboulevard.com
Source: securityboulevard.com – Author: John McKenna As cloud architectures, software-as-a-service and distributed workforces have increasingly become the dominant reality of today’s modern organization, the zero-trust security...
Exploring the Controversy: The Pros and Cons of Environment Variables – PyCon Italia – Source: securityboulevard.com
Source: securityboulevard.com – Author: Mackenzie Jackson I recently had the opportunity to speak at PyCon Italia in the beautiful Italian city of Florence. This ancient city...
BSidesSF 2023 – Dean Liu – Disrupting Malicious Traffic with Egress Proxies – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
The Health Informatics Service Deploys LogRhythm Axon to Secure Healthcare Innovation in the UK – Source: securityboulevard.com
Source: securityboulevard.com – Author: Sherelle Spence London, UK, 29 June 2023 — LogRhythm, the company helping security teams stop breaches by turning disconnected data and signals into trustworthy...
The Cloud Security Risks of Overprivileged Vendors – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jason Martin Security and engineering teams are constantly adopting new technologies in their cloud environments, either to increase the velocity of development...
Hand out a Yellow or Red Card According to Your Rules of the Game – Source: securityboulevard.com
Source: securityboulevard.com – Author: Georgiy Yegazaren In Radware’s Cloud WAF solution, your application is protected from a virus violation, including other infractions like remote file inclusions,...
The Virtual Digital Stranger: What ChatGPT Means for Network Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Bob Friday The advent of ChatGPT has garnered significant attention recently and has dramatically reduced the number of AI skeptics—rightly so, considering...
FIRESIDE CHAT: Outrageous phone bills stun businesses targeted for ‘SMS toll fraud’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: bacohido By Byron V. Acohido SMS toll fraud is spiking. I learned all about the nuances of deploying – and defending –...
Free Akira ransomware decryptor helps recover your files – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Cybersecurity firm Avast has released a free decryptor for the Akira ransomware that can help victims recover their data without...
CISA issues DDoS warning after attacks hit multiple US orgs – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan The U.S. Cybersecurity and Infrastructure Security Agency (CISA) warned today of ongoing distributed denial-of-service (DDoS) attacks after U.S. organizations across...
TSMC denies LockBit hack as ransomware gang demands $70 million – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Chipmaking giant TSMC (Taiwan Semiconductor Manufacturing Company) denied being hacked after the LockBit ransomware gang demanded $70 million not to...
Iran-linked Charming Kitten APT enhanced its POWERSTAR Backdoor – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Iran-linked Charming Kitten group used an updated version of the PowerShell backdoor called POWERSTAR in a spear-phishing campaign. Security firm...
miniOrange’s WordPress Social Login and Register plugin was affected by a critical auth bypass bug – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini A critical authentication bypass flaw in miniOrange’s WordPress Social Login and Register plugin, can allow gaining access to any account on a...
North Korea-linked Andariel APT used a new malware named EarlyRat last year – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini North Korea-linked cyberespionage group Andariel used a previously undocumented malware called EarlyRat. Kaspersky researchers reported that the North Korea-linked APT group Andariel used a previously...
The phone monitoring app LetMeSpy disclosed a data breach – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Android app LetMeSpy disclosed a security breach, sensitive data associated with thousands of Android users were exposed. The phone monitoring app LetMeSpy...
Breach Roundup: Russians Sanctioned for Election Influence – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Breach Notification , Cybercrime as-a-service , Cyberwarfare / Nation-State Attacks Also: CISA Orders Federal Agencies to Patch Vulnerabilities Before July 13...
New Ransomware Actor 8Base Rivals LockBit in Extortion – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cybercrime , Fraud Management & Cybercrime , Next-Generation Technologies & Secure Development Group Has Listed Nearly 40 Victims on Its Dark...
Trauma, Terrorist Victim Data Breached in University Attack – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cybercrime , Fraud Management & Cybercrime , Governance & Risk Management NHS Patient Data, Student, Alumni Records Compromised at University of...
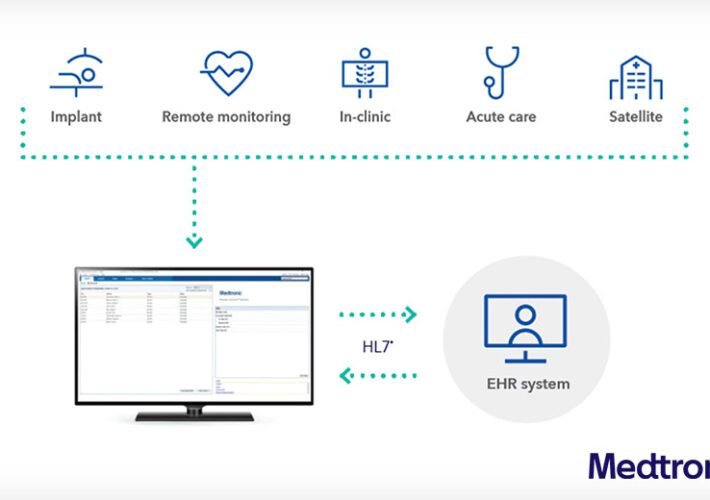
Feds, Medtronic Warn of Flaw in Cardiac Device Data Tool – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Endpoint Security , Internet of Things Security , Standards, Regulations & Compliance Denial of Service Attack, Remote Code Execution Could Affect...