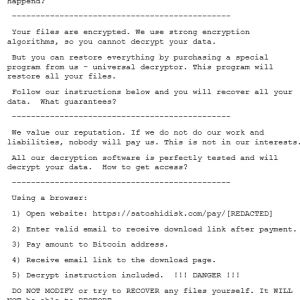
Source: thehackernews.com – Author: . May 25, 2023The Hacker NewsIncident Response A hospital with 2,000 employees in the E.U. deployed Cynet protections across its environment. The...
Month: May 2023
New PowerExchange Backdoor Used in Iranian Cyber Attack on UAE Government – Source:thehackernews.com
Source: thehackernews.com – Author: . May 25, 2023Ravie LakshmananEmail Security / Exploit An unnamed government entity associated with the United Arab Emirates (U.A.E.) was targeted by...
Alert: Brazilian Hackers Targeting Users of Over 30 Portuguese Banks – Source:thehackernews.com
Source: thehackernews.com – Author: . May 25, 2023Ravie LakshmananFinancial Security / Cyber Threat A Brazilian threat actor is targeting more than 30 Portuguese financial institutions with...
Webinar with Guest Forrester: Browser Security New Approaches – Source:thehackernews.com
Source: thehackernews.com – Author: . May 25, 2023The Hacker NewsBrowser Security / Tech In today’s digital landscape, browser security has become an increasingly pressing issue, making...
Buhti Ransomware Gang Switches Tactics, Utilizes Leaked LockBit and Babuk Code – Source:thehackernews.com
Source: thehackernews.com – Author: . May 25, 2023Ravie LakshmananEndpoint Security / Cyber Threat The threat actors behind the nascent Buhti ransomware have eschewed their custom payload...
China’s Stealthy Hackers Infiltrate U.S. and Guam Critical Infrastructure Undetected – Source:thehackernews.com
Source: thehackernews.com – Author: . May 25, 2023Ravie LakshmananCyber Threat / Espionage A stealthy China-based group managed to establish a persistent foothold into critical infrastructure organizations...
CISA warns govt agencies of recently patched Barracuda zero-day – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan CISA warned of a recently patched zero-day vulnerability exploited last week to hack into Barracuda Email Security Gateway (ESG) appliances....
QBot malware abuses Windows WordPad EXE to infect devices – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams The QBot malware operation has started to abuse a DLL hijacking flaw in the Windows 10 WordPad program to infect...
Hot Pixels attack checks CPU temp, power changes to steal data – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A team of researchers at Georgia Tech, the University of Michigan, and Ruhr University Bochum have developed a novel attack...
CISA adds recently patched Barracuda zero-day to its Known Exploited Vulnerabilities catalog – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini US CISA added recently patched Barracuda zero-day vulnerability to its Known Exploited Vulnerabilities catalog. US Cybersecurity and Infrastructure Security Agency...
Security Affairs newsletter Round 421 by Pierluigi Paganini – International edition – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Privacy Overview This website uses cookies to improve your experience while you navigate through the website. Out of these cookies,...
Is the BlackByte ransomware gang behind the City of Augusta attack? – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini The city of Augusta in Georgia, U.S., admitted that the recent IT system outage was caused by a cyber attack. While...
New Buhti ransomware operation uses rebranded LockBit and Babuk payloads – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini The recently identified Buhti operation targets organizations worldwide with rebranded LockBit and Babuk ransomware variants. Researchers from Symantec discovered a...
Industrial Giant ABB Confirms Ransomware Attack, Data Theft – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Swiss industrial giant ABB confirmed this week that it was recently targeted in a ransomware attack and that the cybercriminals...
Dental Health Insurer Hack Affects Nearly 9 Million – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Breach Notification , Cybercrime , Fraud Management & Cybercrime More than 100 Agencies, Health Entities Impacted by Data Breach Discovered in...
Weekly Update 349 – Source: www.troyhunt.com
Source: www.troyhunt.com – Author: Troy Hunt This week’s update is dominated by my experience with “Lena”, the scammer from Gumtree who tried to fleece my wife...
How an innocuous app morphed into a trojan – Week in security with Tony Anscombe – Source: www.welivesecurity.com
Source: www.welivesecurity.com – Author: Editor ESET research uncovers an Android app that initially had no harmful features but months later turned into a spying tool This...
Red Team Security Open Source Toolkit
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
BSidesSF 2023 – Alexis Hancock – HSMs in Plain Envelopes: A Code Signing Story – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2023/05/bsidessf-2023-alexis-hancock-hsms-in-plain-envelopes-a-code-signing-story/ Category & Tags: Security Bloggers Network,appsec education,BsidesSF,BSidesSF...
Live phishing tests not getting the results you want? Here’s what to do. – Source: securityboulevard.com
Source: securityboulevard.com – Author: Scott Wright Well, now what? Many companies will require employees to retake the training or even worse send out more phishing tests...
BSidesSF 2023 – Leif Dreizler – Tracking Meaningful Security Product Metrics – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2023/05/bsidessf-2023-leif-dreizler-tracking-meaningful-security-product-metrics/ Category & Tags: Security Bloggers Network,appsec education,BsidesSF,BSidesSF...
The Developer’s Guide to Mobile Authentication – Source: securityboulevard.com
Source: securityboulevard.com – Author: Deepak Gupta – Tech Entrepreneur, Cybersecurity Author Mobile app developers must ensure that the mobile app is effortless while protecting internal information....
What are FedRAMP Requirements? (And Who Needs to Know) – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richa Tiwari For SaaS applications and cloud service providers (CSPs), maintaining compliance with FedRAMP requirements is critical to the bottom line. It...
Daniel Stori’s ‘# $ To Devops Or Not To Devops’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman via the webcomic talent of the inimitable Daniel Stori at Turnoff.US Permalink *** This is a Security Bloggers Network syndicated...
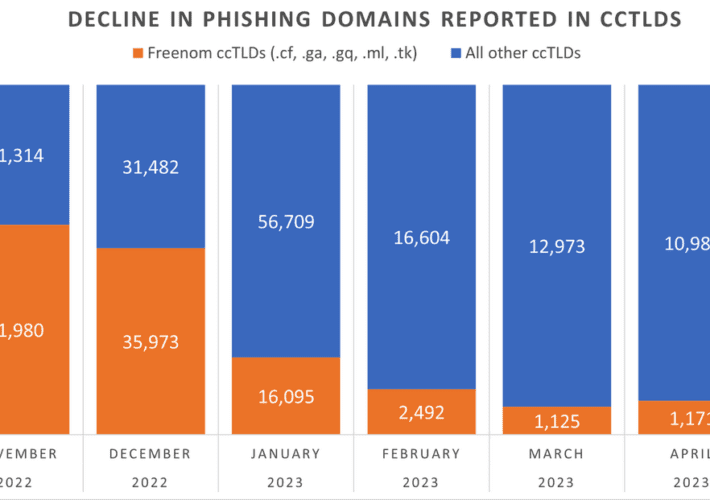
Phishing Domains Tanked After Meta Sued Freenom – Source: securityboulevard.com
Source: securityboulevard.com – Author: BrianKrebs The number of phishing websites tied to domain name registrar Freenom dropped precipitously in the months surrounding a recent lawsuit from...
Are Your Company Secrets Safe on GitHub? Here’s Why You Need to Request a Complimentary Audit – Source: securityboulevard.com
Source: securityboulevard.com – Author: Thomas Segura As a company with a large number of developers, it’s highly likely that some of your company secrets (API keys,...
BSidesSF 2023 – Shobhit Mehta – Lessons Learned While Building a Privacy Operations Center at Headspace Health – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2023/05/bsidessf-2023-shobhit-mehta-lessons-learned-while-building-a-privacy-operations-center-at-headspace-health/ Category & Tags: Security Bloggers Network,appsec education,BsidesSF,BSidesSF...
Latitude Financial Attack Costs Company Up to AU$105 Million – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cybercrime , Finance & Banking , Fraud Management & Cybercrime Hackers Obtained Access Through a Compromised Credential Mihir Bagwe (MihirBagwe) •...
Pegasus Spyware Spotted in Nagorno-Karabakh War – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime Access Now Calls Infections 1st Documented Evidence of Pegasus in Context of...
Webinar | Outsmarting the Hackers: Next-Level Strategies for Battling Third-Party Cyber Risks – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Chris Holden CISO, Crum & Forster Chris Holden is the Chief Information Security Officer (CISO) for Crum & Forster, a leading...