Source: www.proofpoint.com – Author: 1 Relentless cyberattacks and pressure to fix security gaps despite budget constraints are raising the stress levels of corporate cyber leaders and...
Month: May 2023
Microsoft Teams is being hacked to crack Office 365 accounts – here’s how to stay safe – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: 1 Home News Computing (Image credit: Microsoft) Researchers have discovered more ways to abuse Microsoft Teams to steal Office 365 user credentials...
Pentagon Hacking Fears Fueled by Microsoft’s Monopoly on Military IT – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: 1 The Cybersecurity and Infrastructure Security Agency (CISA) released a shocking report on February 23, 2023, revealing the results from a red...
Identity-focused attacks remain the most vulnerable entry point to an organization – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: 1 The Cybersecurity and Infrastructure Security Agency (CISA) released a shocking report on February 23, 2023, revealing the results from a red...
Selena Larson on how cybercriminals use threat intelligence – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: 1 In this Risky Business News sponsor interview Tom Uren asks Proofpoint’s Selena Larson about how threat actors reacted en masse after...
Open-Source Infostealer RAT Hidden in Malicious NPM Packages – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Application Security , Next-Generation Technologies & Secure Development , Threat Intelligence TurkoRat Capable of Credential Harvesting, Possesses Features Like Wallet Grabber...
PyPI temporarily pauses new users, projects amid high volume of malware – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Ax Sharma PyPI, the official third-party registry of open source Python packages has temporarily suspended new users from signing up, and new...
Cloned CapCut websites push information stealing malware – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A new malware distribution campaign is underway impersonating the CapCut video editing tool to push various malware strains to unsuspecting...
HP rushes to fix bricked printers after faulty firmware update – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan HP is working to address a bad firmware update that has been bricking HP Office Jet printers worldwide since it was...
npm packages caught serving TurkoRAT binaries that mimic NodeJS – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Ax Sharma Researchers have discovered multiple npm packages named after NodeJS libraries that even pack a Windows executable that resembles NodeJS but instead...
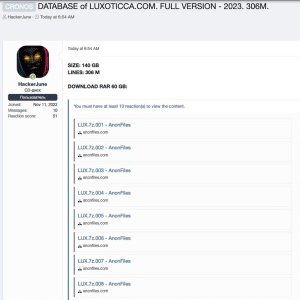
2021 data breach exposed data of 70 Million Luxottica customers – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Luxottica has finally confirmed the 2021 data breach that exposed the personal information of 70 million customers. Luxottica Group S.p.A. is...
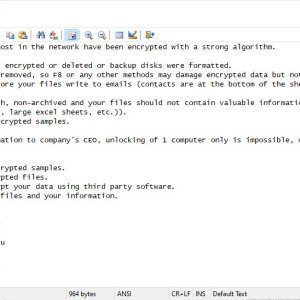
Cybercrime gang FIN7 returned and was spotted delivering Clop ransomware – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Cybercriminal gang FIN7 returned with a new wave of attacks aimed at deploying the Clop ransomware on victims’ networks. Researchers...
US CISA warns of a Samsung vulnerability under active exploitation – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini US CISA added the vulnerability CVE-2023-21492 flaw affecting Samsung devices to its Known Exploited Vulnerabilities Catalog. US CISA added the...
RSAC Fireside Chat: Counteracting Putin’s weaponizing of ransomware — with containment – Source: securityboulevard.com
Source: securityboulevard.com – Author: bacohido By Byron V. Acohido The ransomware plague endures — and has arisen as a potent weapon in geopolitical conflicts. Cyber extortion...
Live panel discussion on insider threats and abuse of privilege – Source: securityboulevard.com
Source: securityboulevard.com – Author: Scott Wright And as we move into artificial intelligence, we have to look at different things like hijacked artificial intelligence with inside...
Exposing The “Denis Gennadievich Kulkov” a.k.a Kreenjo/Nordex/Nordexin/Try2Check Cybercriminal Enterprise – An Analysis – Source: securityboulevard.com
Source: securityboulevard.com – Author: Dancho Danchev Who would have thought? The U.S Secret Service is currently offering $10M reward for Denis Gennadievich Kulkov also known as Kreenjo/Nordex/Nordexin...
Digital Trust Digest: This Week’s Must-Know News – Source: securityboulevard.com
Source: securityboulevard.com – Author: Keyfactor Team The Digital Trust Digest is a curated overview of the week’s top cybersecurity news. Here’s what you need to know...
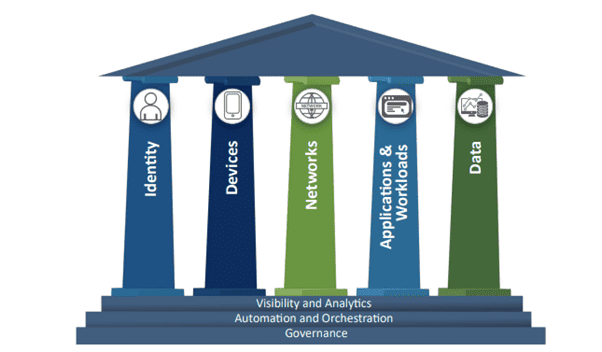
Zero Trust is More Than a Slogan – Source: securityboulevard.com
Source: securityboulevard.com – Author: Bhagwat Swaroop When it comes to Zero Trust, the conversation has moved from being a nebulous term several years ago to a...
How Companies Should Protect Sensitive Data: 6 Practical Tips – Source: securityboulevard.com
Source: securityboulevard.com – Author: Aimee Simpson It’s no secret that sensitive data management is a top priority for security teams, particularly during periods of widespread workforce...
Friday Squid Blogging: Peruvian Squid-Fishing Regulation Drives Chinese Fleets Away – Source: securityboulevard.com
Source: securityboulevard.com – Author: Bruce Schneier A Peruvian oversight law has the opposite effect: Peru in 2020 began requiring any foreign fishing boat entering its ports...
Your SOC 2 Toolkit Essentials for Compliance Excellence – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richa Tiwari Achieving SOC 2 compliance often necessitates the use of specialized tools and software to address specific application and data security...
BSidesSF 2023 – Ehsan Asdar, Nishil Shah – Building Production-Grade End To End Encrypted Applications – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2023/05/bsidessf-2023-ehsan-asdar-nishil-shah-building-production-grade-end-to-end-encrypted-applications/ Category & Tags: Security Bloggers Network,appsec education,BsidesSF,BSidesSF...
The Sky’s the Limit: The Growth of FedRAMP Compliant Cloud Service Offerings – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jenn Sherman As you’ll recall from our last post, FedRAMP just soared to a major milestone – 300 FedRAMP Authorized Cloud Service...
Phishing Vendor Sells IP Addresses to Duck Anomaly Detection – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Business Email Compromise (BEC) , Fraud Management & Cybercrime BulletProofLink Found a Way to Thwart Impossible Travel Detection Prajeet Nair (@prajeetspeaks)...
Zero Trust Authentication: Foundation of Zero Trust Security – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Remote Workforce , Zero Trust Beyond Identity’s Husnain Bajwa on a Solution That Supports Zero Trust...
Cyberattacks on Taiwan Surge Amid Chinese Aggression – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime Rise in Use of PlugX Malware Points to Chinese Nation-State Activity Jayant...
Apple Fixes 3 Zero-Days Exploited in the Wild – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Endpoint Security , Governance & Risk Management , Patch Management Vulnerabilities Exist in Apple-Mandated WebKit Browser Engine Mihir Bagwe (MihirBagwe) ,...
The FTC Pushes Boundaries With Proposed Health Rule Change – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Privacy , Standards, Regulations & Compliance Consumer Health Data Needs More Protections – Is the FTC...
Healthcare attacks are increasing: Why zero trust will prevent care disruptions – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau By Itai Greenberg, Chief Strategy Officer, Check Point. EXECUTIVE SUMMARY: Healthcare cyber attacks are on the rise. Zero trust is a...
What is business identity theft and how can you prevent it? – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: In the way that the identity of a person can be stolen, the identity of a business can also...