Source: www.darkreading.com – Author: Tiago Henriques, Vice President of Research, Coalition Risk aggregation is not a new phenomenon. The insurance industry has examined how shared assets...
Month: May 2023
FBI: Human Trafficking Rings Force Job Seekers Into Cryptojacking Schemes – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading The FBI is warning US citizens that are traveling to or living abroad in Southeast Asia of...
A New Look for Risk in Awareness Training – Source: www.darkreading.com
Source: www.darkreading.com – Author: Curtis Franklin, Senior Analyst, Omdia Cybersecurity awareness training has always, at one level, been about risk. Whether you subscribe to the notion...
Microsoft: BEC Attackers Evade ‘Impossible Travel’ Flags With Residential IP Addresses – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributor, Dark Reading Attackers have found a new way to avoid detection in business email compromise (BEC) and account takeover attacks by...
Bridgestone CISO: Lessons From Ransomware Attack Include Acting, Not Thinking – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer, Dark Reading As a CISO that helped his company navigate through the aftermath of a crippling ransomware attack...
US Sanctions N. Korean Entities for Sending Funds to Regime – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cybercrime , Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime One Worker Also Sanctioned for Transferring IT Earnings to North...
EU Committee Probes TikTok, UK’s Updated GDPR – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 General Data Protection Regulation (GDPR) , Governance & Risk Management , Privacy LIBE Committee Hears From Heads of UK and Irish...
Panel | The Four Steps to Build a Modern Data Protection Platform – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Salah Nassar Sr. Director Product Marketing, Zscaler Salah is a passionate and customer-centric marketer with a diverse background in networking and...
Sharp Decline in Crypto Hacks in Q1 2023 Unlikely to Last – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cryptocurrency Fraud , Finance & Banking , Fraud Management & Cybercrime Law Enforcement, Regulatory Action in US Likely Led to 70%...
North Korea’s BlueNoroff Group Targets macOS Systems – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cryptocurrency Fraud , Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime BlueNoroff Changed Attack Tactics in 2023 After Its TTPs...
Suzuki motorcycle plant shut down by cyber attack – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley The Indian manufacturing plant responsible for manufacturing Suzuki motorcycles has been forced to shut down following a cyber attack. Since...
The previously undocumented GoldenJackal APT targets Middle East, South Asia entities – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini A previously undocumented APT group tracked as GoldenJackal has been targeting government and diplomatic entities in the Middle East and...
Google announced its Mobile VRP (vulnerability rewards program) – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Google introduced Mobile VRP (vulnerability rewards program), a new bug bounty program for reporting vulnerabilities in its mobile applications. Google...
German arms manufacturer Rheinmetall suffered Black Basta ransomware attack – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini The German automotive and arms manufacturer Rheinmetall announced it was victim of a Black Basta ransomware attack that took place last month. Rheinmetall...
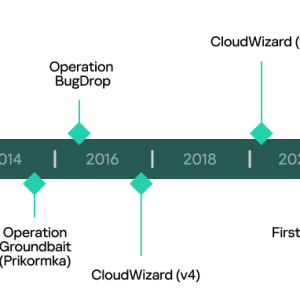
A deeper insight into the CloudWizard APT’s activity revealed a long-running activity – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Experts warn of a threat actor, tracked as CloudWizard APT, that is targeting organizations involved in the region of the Russo-Ukrainian...
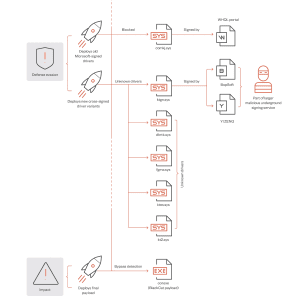
BlackCat Ransomware affiliate uses signed kernel driver to evade detection – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Experts spotted the ALPHV/BlackCat ransomware group using signed malicious Windows kernel drivers to evade detection. Trend Micro researchers shared details...
Axiado releases new security processors for servers and network appliances – Source: www.csoonline.com
Source: www.csoonline.com – Author: The new TCUs released by Axiado are built within a single SoC, with AI as added layer of security. Getty Images Security...
Teleport releases Teleport 13 with automatic vulnerability patching, enhanced DevOps security – Source: www.csoonline.com
Source: www.csoonline.com – Author: Teleport 13 features include Transport Layer Security routing and the ability to import applications/groups from Okta and AWS OpenSearch support for secure...
Think security first when switching from traditional Active Directory to Azure AD – Source: www.csoonline.com
Source: www.csoonline.com – Author: With the final release of Windows 10, the use of traditional Active Directory may be waning, and Azure AD on the rise....
RSAC Fireside Chat: The need to stop mobile apps from exposing API keys, user credentials in runtime – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido As digital transformation accelerates, Application Programming Interfaces (APIs) have become integral to software development – especially when it comes to adding...
Google Unveils Bug Bounty Program For Android Apps – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Google has enhanced the security of its first-party Android applications by launching the Mobile Vulnerability Reward Program (Mobile VRP). The tech...
Fata Morgana Watering Hole Attack Targets Shipping, Logistics Firms – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Cybersecurity experts at ClearSky have discovered a sophisticated watering hole attack targeting multiple Israeli websites. The malicious attempt, believed to be...
GoldenJackal Targets Diplomatic Entities in Middle East, South Asia – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A recently discovered advanced persistent threat (APT) group named GoldenJackal has been observed targeting government and diplomatic entities in the Middle...
ESET: Android App ‘iRecorder – Screen Recorder’ Trojanized with AhRat – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 In the digital world, what’s useful today can become harmful tomorrow. Unfortunately, this is precisely what happened with iRecorder – Screen...
Two-Thirds of IT Leaders Say GDPR Has Reduced Consumer Trust – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Two-thirds (66%) of IT leaders believe GDPR has made consumers less trusting of organizations, according to new research by Macro 4....
Credible Handwriting Machine – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier In case you don’t have enough to worry about, someone has built a credible handwriting machine: This is still a...
The Royal Gang Is Developing Its Own Malware Loader – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Madalina Popovici It has been reported that the Royal ransomware group is enhancing its arsenal with new malware. This group is said...
IAM-Driven Biometrics: The Security Issues with Biometric Identity and Access Management – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Bianca Soare The increase of cybersecurity incidents brings along a higher demand for enhanced security protections. Thus, in the attempt of preventing...
Privileged Access Management (PAM) Best Practices – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Mihaela Marian Privileged access management, PAM in short, is a crucial set of tools and technologies allowing organizations to maintain steadfast control and...
Dell Launches Project Fort Zero Service to Accelerate Zero-Trust IT Shift – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard Dell Technologies today launched a Project Fort Zero cybersecurity services initiative that promises to make it simpler for organizations to...