Source: heimdalsecurity.com – Author: Cristian Neagu A new ransomware operation emerges. Named “Buhti”, the operation uses the leaked code of the LockBit and Babuk ransomware families...
Month: May 2023
Elon Musk’s social security number allegedly leaked in Tesla data breach
Car manufacturer Tesla’s CEO, Elon Musk, may have had his social security number leaked in a data breach that saw 100GB of confidential information accessed. The...
Unprecedented security risks, electric vehicle chargers – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: Last year, global sales for electric vehicles (EVs) increased by 60% worldwide and one in every seven passenger cars...
Safeguarding SMBs: Trends, challenges, best practices & smart security strategies – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau Don’t miss this outstanding, knowledge-packed CyberTalk.org interview with Shahar Divon, Head of Global SMB Sales at Check Point. He delves into...
New Russian-Linked Malware Poses “Immediate Threat” to Energy Grids – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 New Russian-linked malware designed to take down electricity networks has been identified by Mandiant threat researchers, who have urged energy firms...
Romania’s Safetech Leans into UK Cybersecurity Market – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Romanian cybersecurity firm Safetech launched its official presence in the UK on May 23, 2023, underscoring the recent growth of the...
US govt contractor ABB confirms ransomware attack, data theft – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Swiss tech multinational and U.S. government contractor ABB has confirmed that some of its systems were impacted by a ransomware...
Emby shuts down user media servers hacked in recent attack – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Image: Bing Image Creator Emby says it remotely shut down an undisclosed number of user-hosted media server instances that were recently...
Mozilla stops Firefox fullscreen VPN ads after user outrage – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Firefox users have been complaining about very intrusive full-screen advertisements promoting Mozilla VPN displayed in the web browser when navigating an...
BlackByte ransomware claims City of Augusta cyberattack – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The city of Augusta in Georgia, U.S., has confirmed that the most recent IT system outage was caused by unauthorized access...
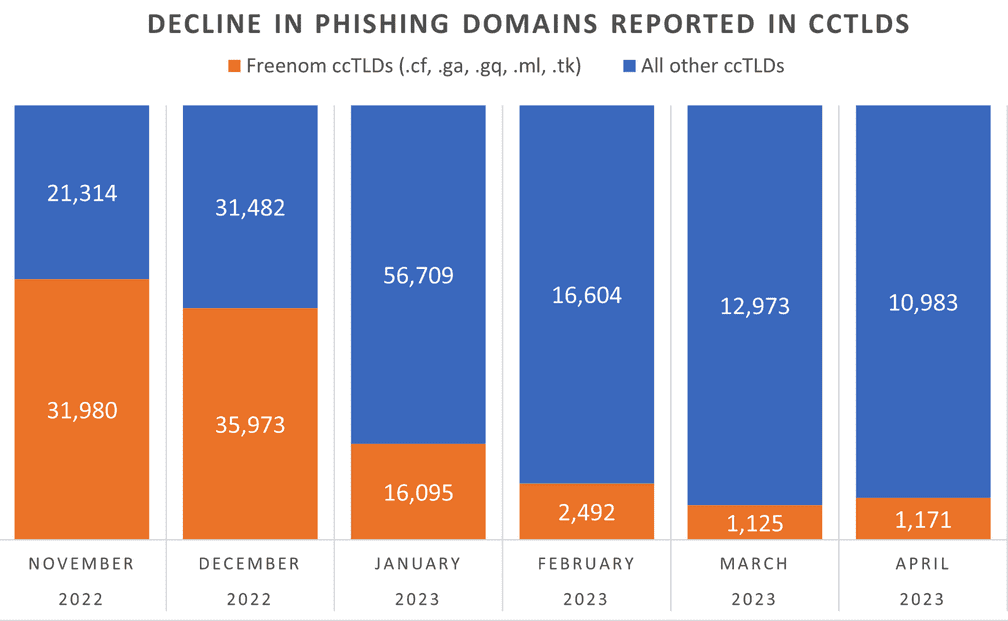
Phishing Domains Tanked After Meta Sued Freenom – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs The number of phishing websites tied to domain name registrar Freenom dropped precipitously in the months surrounding a recent lawsuit from...
Researchers find new ICS malware toolkit designed to cause electric power outages – Source: www.csoonline.com
Source: www.csoonline.com – Author: Mandiant recommends threat-hunting steps to detect COSMICENERGY despite no confirmed attacks in the wild. Over the past few years state-sponsored attackers have...
BrandPost: New report reveals tips for building a skilled cybersecurity workforce – Source: www.csoonline.com
Source: www.csoonline.com – Author: About | When you have comprehensive security, the future is yours to build. Learn about the strategies and solutions to secure your...
BrandPost: The state of operational technology and cybersecurity – Source: www.csoonline.com
Source: www.csoonline.com – Author: About | CISOs today face an expanding attack surface, increasingly threats, and a cybersecurity skills gap. An integrated and automated approach to...
COSMICENERGY: ‘Russian’ Threat to Power Grids ICS/OT – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings Shouty name—dangerous game. Red-team tool ripe for misuse. Researchers have discovered new malware that disrupts electricity grids. The sophisticated threat,...
Revolutionize Zero-Trust Security With a Converged Identity Platform – Source: securityboulevard.com
Source: securityboulevard.com – Author: Faith Kilonzi The world of cybersecurity is ever-evolving, and organizations are facing new and complex security challenges every day. The traditional approach...
Digital Trust Digest: This Week’s Must-Know News – Source: securityboulevard.com
Source: securityboulevard.com – Author: Keyfactor Team The Digital Trust Digest is a curated overview of the week’s top cybersecurity news. Here’s what you need to know...
Revolutionizing DMARC Solutions: Permission Management – Source: securityboulevard.com
Source: securityboulevard.com – Author: Hasmik Khachunts EasyDMARC’s cloud-native platform has been evolving since we first made it in 2018, but our new Permission Management System is...
Consumers Wary of Biometric Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Nathan Eddy Early releases of identity verification and facial recognition technology have failed to deliver on the promise of trustworthy digital identification...
How to Scan Zip Files for Malware Threats – Source: securityboulevard.com
Source: securityboulevard.com – Author: Votiro Antivirus solutions and antivirus scanning is the status quo for preventing malware in files. Hackers realize this and have developed techniques...
Connecting the dots: Development + business risk + due diligence – Source: securityboulevard.com
Source: securityboulevard.com – Author: Phil Odence Organizations should emphasize processes that connect the dots between software development practices, business risk and due diligence activities. Sponsorships Available...
Federal Appellate Court Approves ‘Pretext’ Border Search – Source: securityboulevard.com
Source: securityboulevard.com – Author: Mark Rasch For almost nine years, Chinese national and U.S. resident Haitao Xiang had been employed by the Monsanto company in St....
Expeditionary Cyberspace Operations – Source: securityboulevard.com
Source: securityboulevard.com – Author: Bruce Schneier Cyberspace operations now officially has a physical dimension, meaning that the United States has official military doctrine about cyberattacks that...
Complete guide to data access governance – Source: securityboulevard.com
Source: securityboulevard.com – Author: Emma Kelly Every company knows the challenges of data access governance: too much data from too many sources, an unprecedented number of...
OpenAI CEO Altman ‘Blackmails’ EU Over AI Regulation – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development , Standards, Regulations & Compliance ‘No Plans to Leave,’ Altman...
Capita Hack Fallout: Regulator Sees Breach Reports Surge – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Incident & Breach Response , Ransomware ICO Receives ‘Large Number of Reports’ From Organizations Affected by...
Iranian Hackers Deploy New Ransomware Against Israeli Firms – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime , Ransomware Researchers Discover Moneybird Ransomware Strain, Warn of Growing Sophistication Anviksha...
ISMG Editors: How Ukraine’s Cyber Defenders Prepped for War – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime , Governance & Risk Management Also: Meta Fined 1.2 Billion Euros for...
How Safe Is Your Wearable Device? – Source: www.darkreading.com
Source: www.darkreading.com – Author: Ján Lunter, CEO & CTO, Innovatrics In 2018, 34-year-old Bobbi Leverette was lying in bed beside her newborn baby when her heart...
Russia’s War in Ukraine Shows Cyberattacks Can Be War Crimes – Source: www.darkreading.com
Source: www.darkreading.com – Author: Andrada Fiscutean, Contributing Writer, Dark Reading Russia’s cyberattacks against Ukrainian civilian and critical infrastructure has shown what it looks like when cyberattacks...