Source: heimdalsecurity.com – Author: Cristian Neagu
A new ransomware operation emerges. Named “Buhti”, the operation uses the leaked code of the LockBit and Babuk ransomware families to target machines running Windows and Linux.
The group was first spotted in the wild by Palo Alto Networks’ Unit 42 team in February 2023, which identified it as a Go-based Linux-targeting ransomware. Even if the threat actors behind Buhti, now tracked as “Blacktail”, have not developed their own ransomware strain, they have created a custom data exfiltration they use to blackmail victims through double-extorsion.
What We Know About Buhti
The threat actors use a version of the Windows LockBit 3.0 builder, which was leaked on Twitter back in September 2022. When an attack is successful, the compromised machines’ wallpaper is changed to instruct the victims to read the ransom note, and all encrypted files are given the “.buthi” extension.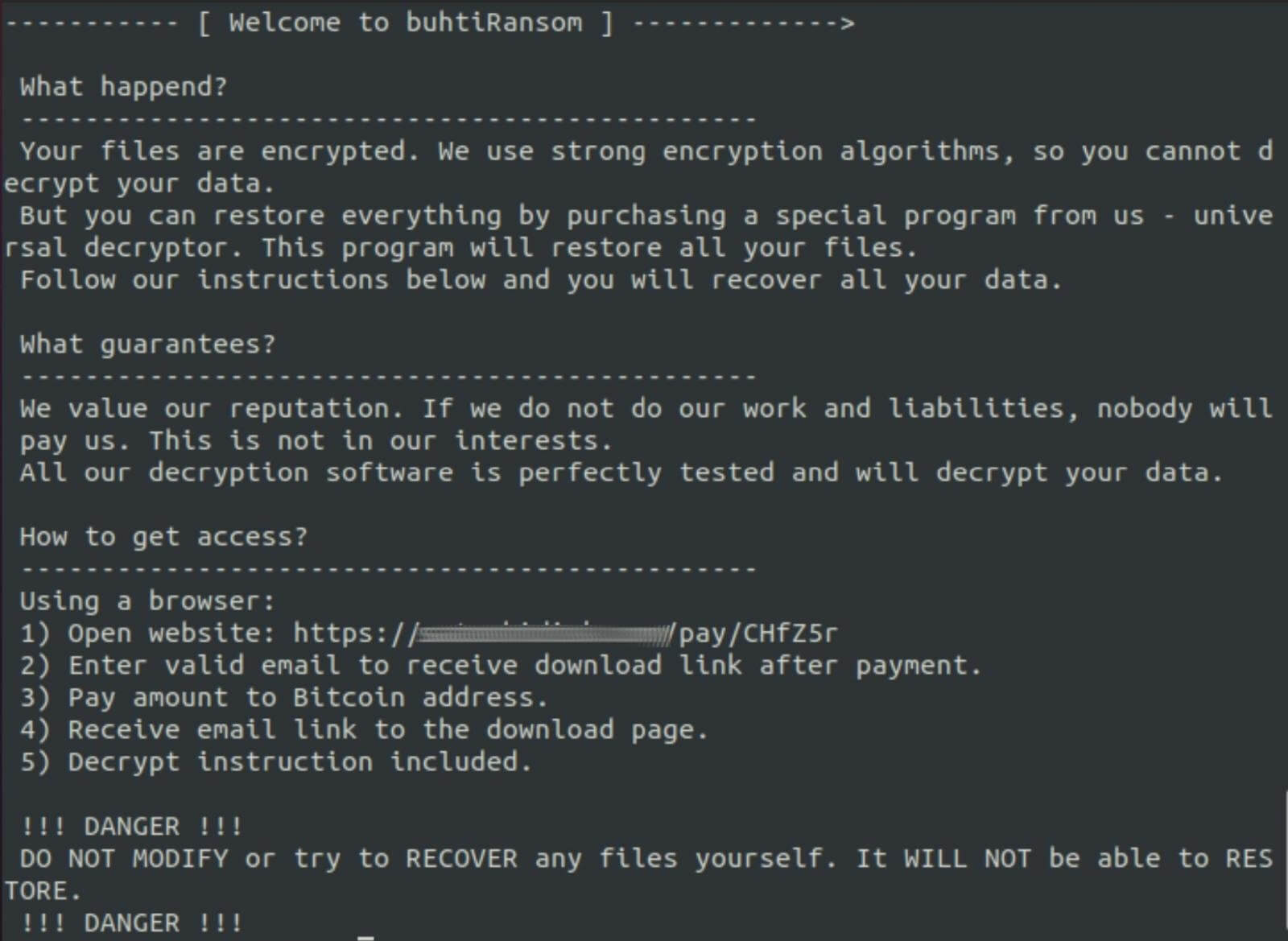
Buhti Ransom Note (Source)
Blacktail’s payload for Linux attacks is based on the Babuk source code, which a threat actor shared on a Russian-speaking hacking forum in September 2021.
How Blacktail Operates
Blacktail isn’t just a knockoff that uses other hackers’ tools with a few minor tweaks. Instead, the new group makes use of a unique network penetration technique and a unique exfiltration tool. Security researchers reported that Buhti attacks have been leveraging the recently disclosed PaperCut NG and MF RCE vulnerability, which was also exploited by LockBit and Clop ransomware.
The attackers leverage the CVE-2023-27350 vulnerability to install Cobalt Strike, Meterpreter, Sliver, AnyDesk, and ConnectWise on targeted machines, and use them to steal credentials and move laterally into compromised networks, launch payloads, steal files, and more. Another vulnerability leveraged by the group was CVE-2022-47986, a critical remote code execution flaw impacting the IBM Aspera Faspex file exchange product.
The tool targets the following types of files: pdf, php, png, ppt, psd, rar, raw, rtf, sql, svg, swf, tar, txt, wav, wma, wmv, xls, xml, yml, zip, aiff, aspx, docx, epub, json, mpeg, pptx, xlsx, and yaml.
According to BleepingComputer, researches have confirmed hits in multiple countries including the United States, the United Kingdom, China, India, France, Germany, Spain, Switzerland, Estonia, Belgium, Czechia, and Ethiopia, indicating that Buthi already a very active ransomware operation.
Blacktail’s tactic of quickly adopting exploits for newly disclosed vulnerabilities makes them a potent threat that calls for increased vigilance and proactive defense strategies like timely patching.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.
If you liked this post, you will enjoy our newsletter.
Get cybersecurity updates you’ll actually want to read directly in your inbox.
Original Post URL: https://heimdalsecurity.com/blog/buhti-ransomware-blacktails-newest-operation-affects-multiple-countries/
Category & Tags: Cybersecurity News – Cybersecurity News
Views: 0



















































