Source: www.tripwire.com – Author: Graham Cluley The US Cybersecurity and Infrastructure Security Agency (CISA), FBI, and others have issued a joint alert, advising organisations of the...
Day: May 19, 2023
CloudWizard APT: the bad magic story goes on – Source: securelist.com
Source: securelist.com – Author: Leonid Bezvershenko, Georgy Kucherin, Igor Kuznetsov In March 2023, we uncovered a previously unknown APT campaign in the region of the Russo-Ukrainian...
Keep Your Friends Close and Your Identity Closer – Source: www.darkreading.com
Source: www.darkreading.com – Author: Sameer Hajarnis, Chief Product Officer, OneSpan The digital world touches everything we do: work, shopping, even your wallet. And the one thing...
Google Debuts Quality Ratings for Security Bug Disclosures – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Editor, Dark Reading Google and Android will now assess device vulnerability disclosure reports based on the level of information that...
Enterprises Rely on Multicloud Security to Protect Cloud Workloads – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer, Dark Reading As enterprises move more of their business infrastructure into the cloud, they are grappling with the...
3 Ways Hackers Use ChatGPT to Cause Security Headaches – Source: www.darkreading.com
Source: www.darkreading.com – Author: Ron Reiter, Co-Founder & CTO, Sentra With ChatGPT making headlines everywhere, it feels like the world has entered a Black Mirror episode....
How business email compromise attacks emulate legitimate web services to lure clicks – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Karl Greenberg New BEC cyberattacks use phishing with a legitimate Dropbox link as a lure for malware and credentials theft. Image: Adobe...
LayerZero Labs Launches $15M Bug Bounty; Largest in the World – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 VANCOUVER, BC, May 17, 2023 /PRNewswire/ — LayerZero Labs, the team that launched the leading cross-chain messaging protocol LayerZero, today announced that it has...
Eagle Eye Networks and Brivo Announce $192M Investment — One of the Largest Ever in Cloud Physical Security – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 AUSTIN, Texas, BETHESDA, Maryland — May 17, 2023 — Eagle Eye Networks, the global leader in cloud video surveillance and Brivo,...
Rebinding Attacks Persist With Spotty Browser Defenses – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer, Dark Reading Browser companies and network-security vendors have created a variety of defenses for the three-decades-old attack technique...
Microsoft Digital Defense Report: Nation-State Threats and Cyber Mercenaries – Source: www.darkreading.com
Source: www.darkreading.com – Author: Microsoft Security, Microsoft Every year, Microsoft releases the “Microsoft Digital Defense Report” as a way to illuminate the evolving digital threat landscape...
Google Chrome 3rd Party Cookies Crumbling — Finally! – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings Privacy Sandbox inching towards reality. But concerns remain. Google’s plan to kill the third party cookie is moving forward. Remember...
9 Key Takeaways from a Platform Team’s Panel Discussion on Kubernetes – Source: securityboulevard.com
Source: securityboulevard.com – Author: Danielle Cook If you’re thinking about building a Kubernetes platform that your developers can use to build applications, you need to know...
BSidesSF 2023 – Breanne Boland, Amy Martin – No Adversaries: Getting Users On Your Side For Tough Transformations – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2023/05/bsidessf-2023-breanne-boland-amy-martin-no-adversaries-getting-users-on-your-side-for-tough-transformations/ Category & Tags: Security Bloggers Network,appsec education,BsidesSF,BSidesSF...
Delivering World-Class CIAM: The Product Management Journey at LoginRadius – Source: securityboulevard.com
Source: securityboulevard.com – Author: Deepak Gupta – Tech Entrepreneur, Cybersecurity Author As businesses continue to evolve in the digital era, it is becoming increasingly important to...
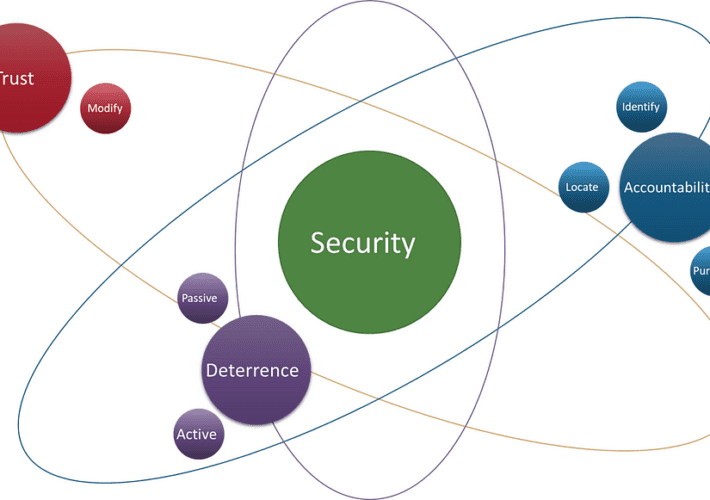
Security Distilled: Building a First-Principles Approach to Understanding Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Nathan D. By Nathan Davis This body of work also appears in the form of a webinar, which can be accessed here. What is...
Guarding the Gates: The Intricacies of Detection Engineering and Threat Hunting – Source: securityboulevard.com
Source: securityboulevard.com – Author: Cyborg Security In the ever-evolving landscape of cybersecurity, two disciplines stand out: Detection Engineering and Threat Hunting. While they share common objectives...
Learnings from the IDC South Africa CIO Summit 2023 #IDSACIO – Source: securityboulevard.com
Source: securityboulevard.com – Author: Lalit Shinde My colleagues and our partners attended the annual IDC South Africa CIO Summit 2023 on May 18, 2023 in Johannesburg....
Complete Guide to Elastic SIEM – Source: securityboulevard.com
Source: securityboulevard.com – Author: Gilad David Maayan Elastic Security, which includes Elastic security information and event management (SIEM), is a comprehensive security solution developed by Elastic....
cdCon + GitOpsCon – Co-evolving Open Source DevOps Communities In One Conference – Source: securityboulevard.com
Source: securityboulevard.com – Author: Dwayne McDaniel On the west coast of Canada, you will find Vancouver, British Columbia, home to the Canucks, breathtaking scenery, and the...
Federal Court Dismisses FTC Location Privacy Lawsuit – Source: securityboulevard.com
Source: securityboulevard.com – Author: Mark Rasch Geolocation data is among the most sensitive personal data. Marketers can use this data to determine what you are likely...
ISMG Editors: The Plot Thickens for Capita in Breach Fallout – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Blockchain & Cryptocurrency , Incident & Breach Response , Next-Generation Technologies & Secure Development Also: The EU Adopts a Crypto Regulation;...
Ukraine’s Cyber Defense Success: Top Takeaways – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime Experts Highlight the Importance of Preparation, Partnerships, Resilience Mathew J. Schwartz (euroinfosec)...
LockBit Leaks 1.5TB of Data Stolen From Indonesia’s BSI Bank – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Finance & Banking , Fraud Management & Cybercrime , Industry Specific Bank Syariah Indonesia Says Service Interruptions Were Maintenance Jayant Chakravarti...
LIVE Webinar | Hackers Don’t Back Down, So You Need to Back Up: Data Security’s Hardest Truths – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Steven Stone Head of Rubrik Zero Labs, Rubrik Steven Stone leads Rubrik’s new data threat research unit to uncover real-world intrusions...
French Privacy Watchdog Pledges Additional AI Oversight – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 General Data Protection Regulation (GDPR) , Governance & Risk Management , Privacy CNIL Says ‘Privacy-Friendly’ AI Systems Are a Must Akshaya...
Cryptohack Roundup: Uranium Finance, LayerZero, MiCA – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Blockchain & Cryptocurrency , Cryptocurrency Fraud , Fraud Management & Cybercrime Also: Ledger Faces Backlash on Seed Phrase Recovery Solution Rashmi...
Researchers Identify Second Developer of ‘Golden Chickens’ Malware – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Cybersecurity firm eSentire says it has identified the second developer of Golden Chickens, a malware suite used by financially-motivated cybercrime...
Cloudflare Unveils New Secrets Management Solution – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Cloudflare on Thursday announced Secrets Store, a new solution designed to help developers and organizations securely store and manage secrets...
Apple Patches 3 Exploited WebKit Zero-Day Vulnerabilities – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Apple on Thursday released security updates for its operating systems to patch dozens of vulnerabilities that could expose iPhones and...