Source: securityboulevard.com – Author: wlrmblog
Welcome to the 10th post in our weekly series on the new 2023 OWASP API Security Top-10 list, with a particular focus on security practitioners. This post will focus on API9:2023 Improper Inventory Management.
In this series we are taking an in-depth look at each category – the details, the impact and what you can do about it. To see previous posts you might have missed, click here.
TL;DR
When an API or the environment isn’t properly documented, you may end up with blind spots, resulting in undocumented APIs and endpoints or unknown data flows. Improper inventory management can result in data disclosure and expanded attack surface.
The Details
Improper inventory management is less of a technical vulnerability than a process problem that leads to technical failures. It stands apart from the other entries in the OWASP APIsec Top-10 because it’s not a problem that a developer fixes in the code.
Improper inventory management shows up as “blind spots” in your governance of APIs. It’s useful to think in terms of three facets: documentation, data, and audit. If you don’t adequately document the existence, purpose, version, and location of your APIs, then there are much more likely to have shadow or orphan APIs in your environments.
A failure to inventory the data and data flows in your APIs can result in unexpected exposure of sensitive information. Finally, while documentation is a clear requirement for proper inventory management, it’s also subject to error. When documentation and reality differ, it’s the result of failing to audit.
The common thread across these three facets is that failure to manage the APIs and associated metadata.
What’s the Impact?
In assessing the impact of improper inventory management, you should use the same three facets described above. A failure to adequately document your APIs results in shadow and orphan APIs in the environment, as well as outdated APIs and components. The impact of these results is the unnecessary exposure of risk. A shadow (or undocumented) API is unlikely to be adequately protected or updated, and could be exploited by an attacker. An orphan (documented, but unused) API increases code complexity and consumes developer resources, which can lead to other types of failures. Out-of-date APIs and components are well understood to increase the risk of unpatched vulnerabilities.
A failure to understand the data flows in your applications and APIs can expose sensitive data in unexpected ways. Customer data can end up in places you might not expect, or be exposed to other users and potentially attackers. It’s not just customer data that might be impacted, of course. Data about your organization or about the application itself might be exposed.
Finally, an organization that diligently documents all of their APIs and data flows might simply fail to see when reality doesn’t match the documentation. A failure to audit the environment can result in some of the very situations that documentation is meant to avoid. Removing an endpoint from an API’s documentation doesn’t mean it’s magically removed from the environment; that’s how shadow APIs happen. Likewise, updating the documentation for a data flow doesn’t automatically update the application’s code to do the same. Auditing the environment to ensure reality matches the documentation is simple good governance.
What Can You Do About It?
The antidote to improper inventory management is visibility. A good place to start is with API discovery. Inventorying the APIs already in your environment can jump start the process of proper inventory management. It often takes just one unexpected surprise from discovery to spur an organization towards better documentation. Of course, it’s also easier to document an environment for which you have an inventory; i.e., it’s easier to start from reality.
With a basic inventory in hand, you can move on to creating actual documentation, including building the creation of API specification into your development process, or requesting them from your vendors.
How Wallarm Can Help
API Discovery is part of the Wallarm platform. API Discovery enumerates all the APIs and endpoints in your environment, including what methods and parameters they support, and what types of data they present. Wallarm can also produce an OpenAPI specification for any discovered APIs. Wallarm also compares discovered APIs to customer-provided specifications, automatically surfacing shadow and orphan APIs. The API Discovery capability from Wallarm provides a solid foundation for proper inventory management.
Learn More
Come back next week as we dig into the details of another category of the new 2023 OWASP Top-10 API Security Risks list – or click here to see previous posts you might have missed.
In the meantime, here are some other resources which might help on your journey to end-to-end API security:
- Solution Brief: OWASP API Security Top-10 2023 Reference Guide (PDF)
- Blog Post: OWASP API Security Top-10 Risks for 2023 Released
- Blog Post: OWASP API Security Top-10 for 2023 Risk Ratings
- On-Demand Webinar: A Practitioner’s Guide to the New 2023 OWASP API Security Update
- On-Demand Webinar: A CISOs Guide to the New 2023 OWASP API Security Update
- Research Report: 2022 Year-End API ThreatStats™ Report (blog and linked full report)
Protect Your APIs from OWASP API Security Top-10 Threats
Wallarm End-to-End API Security solution provides comprehensive protection against the OWASP API Security Top-10 threats. And in 2023, we’ve made it even easier for you!
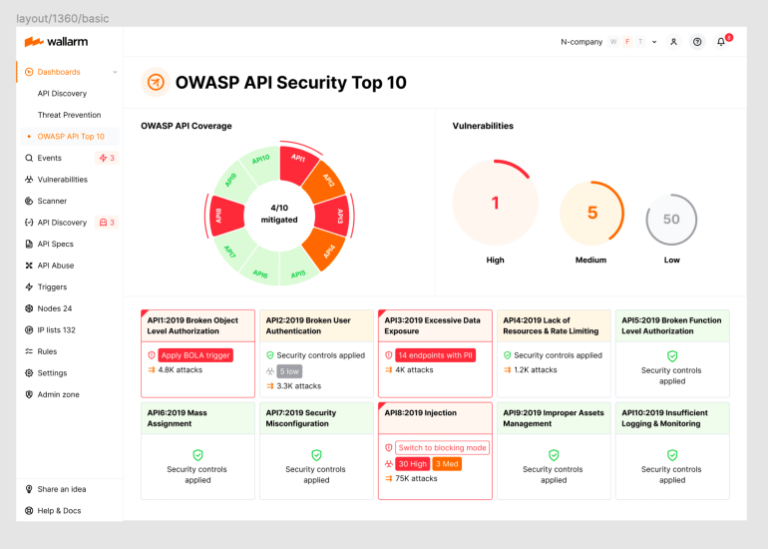
The Wallarm 2023 OWASP API Security Top-10 Dashboard provides you with complete visibility into the security state of your APIs, easy identification of your most critical security risks, and ability to immediately apply protective measures.

If you are interested in learning more about how we can help you protect your APIs, please schedule a demo with one of our security experts today!
The post 2023 OWASP Top-10 Series: API9:2023 Improper Inventory Management appeared first on Wallarm.
*** This is a Security Bloggers Network syndicated blog from Wallarm authored by wlrmblog. Read the original post at: https://lab.wallarm.com/api92023-improper-inventory-management/
Original Post URL: https://securityboulevard.com/2023/09/2023-owasp-top-10-series-api92023-improper-inventory-management/
Category & Tags: Application Security,Security Bloggers Network,owasp,OWASP APIsec Top-10 2023 Series,OWASP Top 10 – Application Security,Security Bloggers Network,owasp,OWASP APIsec Top-10 2023 Series,OWASP Top 10