Collaboration is key to balance customer experience with security, privacyThe way Yaron Cohen sees it, companies today must do in the digital world what came naturally...
Day: September 22, 2022
Customers’ personal data stolen as Optus suffers massive cyber-attack
Customers’ personal data stolen as Optus suffers massive cyber-attackPersonal information of potentially millions of customers exposed, including names, dates of birth, addresses, and contact details Optus...
Wormable Flaw, 0days Lead Sept. 2022 Patch Tuesday
Wormable Flaw, 0days Lead Sept. 2022 Patch TuesdayThis month’s Patch Tuesday offers a little something for everyone, including security updates for a zero-day flaw in Microsoft...
Learn Palo Alto Networks cybersecurity with this $20 training
Learn Palo Alto Networks cybersecurity with this $20 trainingStart deploying cutting-edge firewalls with this training certification course. The post Learn Palo Alto Networks cybersecurity with this...
Optus data breach: who is affected, what has been taken and what should you do?
Optus data breach: who is affected, what has been taken and what should you do?After a malicious cyber-attack, customers of Australia’s second-largest telco are advised they...
A third of enterprises globally don’t prioritize digital trust: ISACA
A third of enterprises globally don’t prioritize digital trust: ISACADigital trust is crucial for modern business relationships as increasingly, transactions require sensitive information to be shared...
Say Hello to Crazy Thin ‘Deep Insert’ ATM Skimmers
Say Hello to Crazy Thin ‘Deep Insert’ ATM SkimmersA number of financial institutions in and around New York City are dealing with a rash of super-thin...
Uber exposes Lapsus$ extortion group for security breach
Uber exposes Lapsus$ extortion group for security breachIn last week’s security breach against Uber, the attackers downloaded internal messages from Slack as well as information from...
Most common SAP vulnerabilities attackers try to exploit
Most common SAP vulnerabilities attackers try to exploitUnpatched vulnerabilities, common misconfigurations and hidden flaws in custom code continue to make enterprise SAP applications a target rich...
GUEST ESSAY: The rise of ‘PhaaS’ — and a roadmap to mitigate ‘Phishing-as-a-Service’
GUEST ESSAY: The rise of ‘PhaaS’ — and a roadmap to mitigate ‘Phishing-as-a-Service’Cybersecurity is a top concern for individuals and businesses in the increasingly digital world....
Pay-per-install services provide access to thousands of compromised computers
Pay-per-install services provide access to thousands of compromised computersPrivateLoader malware, which enables cybercriminals to buy thousands of infected computers in the U.S. and in other regions,...
Open Source Repository Attacks Soar 700% in Three Years
Open Source Repository Attacks Soar 700% in Three YearsSonatype says it has detected 95,000 since 2019Leer másSonatype says it has detected 95,000 since 2019
Video Game Publisher Admits Helpdesk Was Hijacked
Video Game Publisher Admits Helpdesk Was HijackedPlayers were sent malicious links disguised as support ticketsLeer másPlayers were sent malicious links disguised as support tickets
Uber links cyberattack to LAPSUS$, says sensitive user data remains protected
Uber links cyberattack to LAPSUS$, says sensitive user data remains protectedUber has linked its recent cyberattack to an actor (or actors) affiliated with the notorious LAPSUS$...
Uber’s hacker *irritated* his way into its network, stole internal documents
Uber’s hacker *irritated* his way into its network, stole internal documentsUber has suffered a security breach which allowed a hacker to break into its network, and...
Two-Fifths of US Consumers Suffer Personal Data Theft
Two-Fifths of US Consumers Suffer Personal Data TheftThose suffering emotional and physical impact surgesLeer másThose suffering emotional and physical impact surges
The Risk of Ransomware Supply Chain Attacks
The Risk of Ransomware Supply Chain AttacksOver the years, ransomware has become a major threat and it can put supply chains in deep trouble.Leer másTrend Micro...
SEC fines Morgan Stanley Smith Barney $35 million over failure to secure customer data
SEC fines Morgan Stanley Smith Barney $35 million over failure to secure customer dataThe financial giant hired a moving company with no experience in data destruction...
Multiple Vulnerabilities Discovered in Dataprobe’s iBoot-PDUs
Multiple Vulnerabilities Discovered in Dataprobe's iBoot-PDUsThey pose a number of risks to Dataprobe, including giving control of the iBoot-PDU to attackersLeer másThey pose a number of...
Palo Alto adds software composition analysis to Prisma Cloud to boost open-source security
Palo Alto adds software composition analysis to Prisma Cloud to boost open-source securityPalo Alto Networks has added a new software composition analysis (SCA) solution to Prisma...
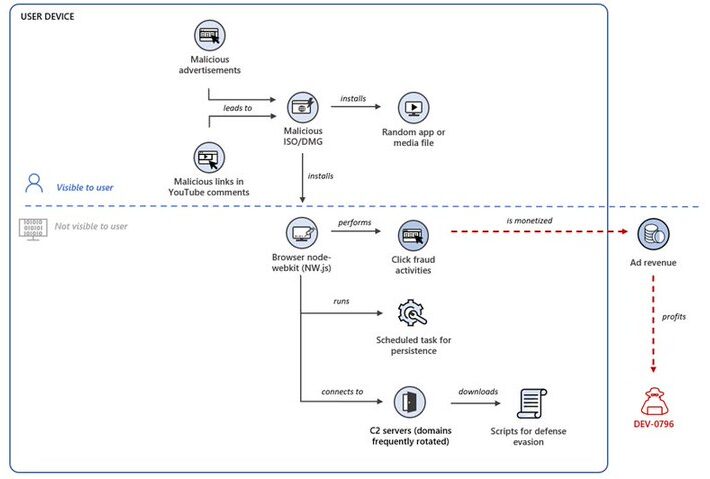
IT giants warn of ongoing Chromeloader malware campaigns
IT giants warn of ongoing Chromeloader malware campaignsVMware and Microsoft are warning of a widespread Chromeloader malware campaign that distributes several malware families. ChromeLoader is a...
CrowdStrike adds XDR, other capabilites across 4 key security products
CrowdStrike adds XDR, other capabilites across 4 key security productsCrowdStrike on Tuesday announced enhancements to four of its security products–Falcon Insight, CrowdStrike Cloud Security, Humio, and...
Use-after-freedom: MiraclePtr
Use-after-freedom: MiraclePtr Posted by Adrian Taylor, Bartek Nowierski and Kentaro Hara on behalf of the MiraclePtr team Memory safety bugs are the most numerous category of...
American Airlines disclosed a data breach
American Airlines disclosed a data breachAmerican Airlines disclosed a data breach, threat actors had access to an undisclosed number of employee email accounts. American Airlines recently suffered a...
Atlassian Confluence Vulnerability CVE-2022-26134 Abused For Cryptocurrency Mining, Other Malware
Atlassian Confluence Vulnerability CVE-2022-26134 Abused For Cryptocurrency Mining, Other MalwareUsers are advised to patch immediately: We found exploit samples abusing the Atlassian Confluence vulnerability (CVE-2022-26134) in...
NCSC: British Retailers Need to Move Beyond Passwords
NCSC: British Retailers Need to Move Beyond PasswordsThe UK’s national cybersecurity agency also advised organizations on what steps they should take if their brand has been...
Analyzing IP Addresses to Prevent Fraud for Enterprises
Analyzing IP Addresses to Prevent Fraud for EnterprisesHow can businesses protect themselves from fraudulent activities by examining IP addresses? The police would track burglars if they...
Botched Crypto Mugging Lands Three U.K. Men in Jail
Botched Crypto Mugging Lands Three U.K. Men in JailThree men in the United Kingdom were arrested this month for attempting to assault a local man and...
Uber believes that the LAPSUS$ gang is behind the recent attack
Uber believes that the LAPSUS$ gang is behind the recent attackUber disclosed additional details about the security breach, the company blames a threat actor allegedly affiliated...
SIM Swapper Abducted, Beaten, Held for $200k Ransom
SIM Swapper Abducted, Beaten, Held for $200k RansomA Florida teenager who served as a lackey for a cybercriminal group that specializes in cryptocurrency thefts was beaten...