Source: securityboulevard.com – Author: Ahona Rudra
Reading Time: 4 min

Why is software security so important? Simply put, there are more threats these days and many of today’s mobile applications, specifically, are often available over lots of different networks – and are now also connected to the cloud. While cloud computing is a great way of crossing borders and opening up new potential online, it’s also a sure fire way to make yourself or your business even more vulnerable to malicious third parties than they already were.
This means that there are increased weaknesses, and thus that means a rise in security threats and breaches. Hackers are attacking apps more than they ever were and Appsec can help reveal those weaknesses at the application level and prevent these kinds of events from happening.
Couple that with the rise in pressure from companies to make sure everything is secure at the network level – and also within the applications themselves, especially smaller scale applications with increased vulnerabilites – and you have got all the reasons you need to understand why appsec matters so much.
Still, even in the current climate, plenty of people remain unaware of quite how important it is to be getting proactive about security and not just resting on ‘the basics’. With that in mind, we have put together a full guide detailing exactly why appsec is so important.
Appsec Testing in Brief

Part of the software development process is undertaking application security testing. It ensures that there are no vulnerabilities in new or updated versions of software applications. Appsec audits can ensure applications comply with all the security criteria they need to, giving you the peace of mind that can only come from an expert appraisal.
Once an app has successfully passed an audit, developers have to ensure that only those people who are authorized can have access to it – and that it stays that way. Shockingly, in a survey carried out earlier this year by Checkmarx, it was revealed that 92% of companies who were questioned had some form of security breach in the past year.
A lot of security breaches are relatively minor, which is why we’re not constantly hearing about them. But, even in those ‘minor’ cases, user data is inevitably put at risk and, in many cases, passed onto malicious third-parties who have no scruples about generating an income from it. Minor doesn’t mean much when you are one of those people being victimised.
And, of course, plenty of data breaches – far too many, in fact – are major. With so many companies, both SMEs and largescale enterprises alike falling foul to data breaches every year, it is only a matter of time before the threat draws close to home…for any of us.
Why Appsec Security Controls Matter
Appsec controls are techniques that are put in place when developing an app at the coding level. This makes apps less vulnerable to threats. Many appsec controls look at how an application responds to the kind of unexpected inputs a cybercriminal would try and use to exploit a weakness in the system.
Appsec programmers can write codes that mean they have more control over the outcome of anything unexpected like this – fuzz testing is one of them. Fuzzing is security testing whereby developers test results of unexpected values to find out which of them are making applications act in the wrong way. – and that might eventually open up a security hole.
The Hallmarks of Strong Appsec
So what makes a strong appsec? Well, different types of appsec features include:
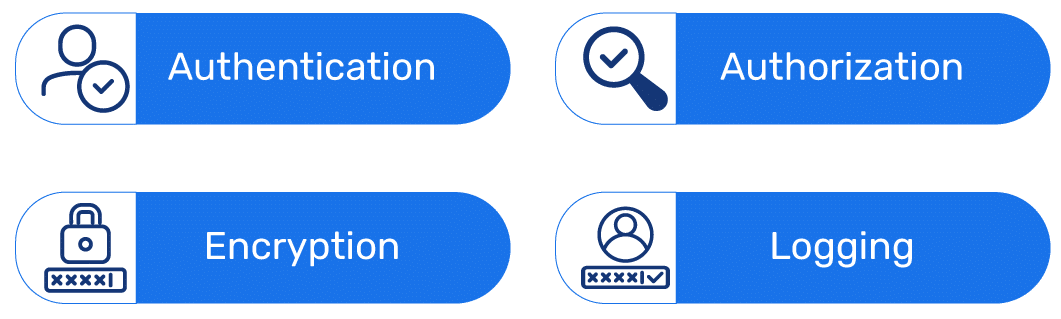
- authentication
- authorization
- encryption
- logging
Authentication: This is when software developers build procedures into an app to ensure that only people who are authorized have access to it – and they can also securely confirm that a user is who they say they are. In the old days, users simply provided a username and password just as normal, but now multi-factor authentication is becoming more prevalent, this requires more than one form of authentication, so you might need to provide an extra layer of protection such as a thumbprint or facial recognition and details from a smartphone.
Authorization: Once a user has been authenticated, they gain the authority to access and use the app. A system can validate that this is the case and they have permission by comparing their identity with a list of authorized users. Authorization can only happen after authentication has taken place. It’s an often forgotten feature that can really complement a 2- or 3-factor authentication process and give you extra peace of mind that no one is accessing features they should not be able to access.
Encryption: The third stage brings in other security measures that can help protect sensitive data from being seen or used by hackers – from your email to your smartphone. For instance, in cloud-based applications, where you are going to get traffic that contains sensitive data traveling between the end user and the cloud, it can be encrypted to keep the data safe. This means that any information ‘stolen’ between the sender and the receiver cannot be deciphered or read. This is very important for sensitive data like payment/banking details since, without encryption, that information is readily available to malicious third parties.
Logging: Logging helps to ascertain who got access to any secure data and exactly how they did it. Log files will give time-stamped records of who accessed what and what information they were party to, which is a great preventative measure against unwanted parties accessing your account. If potential trespassers are made aware of the fact that you have a log in place, they are a lot less likely to take the risk, since their activity will be there for you to see – and, if necessary, show to the police or the judicial courts.
The world we’re living in is dangerous for apps, and the problem is only getting worse. With strong security, however, apps can set up a line of defence and halt any attackers before they get a foothold. That’s why it’s so important to apply it sooner rather than later.

*** This is a Security Bloggers Network syndicated blog from PowerDMARC authored by Ahona Rudra. Read the original post at: https://powerdmarc.com/software-application-security-hallmarks/
Original Post URL: https://securityboulevard.com/2024/05/what-are-the-hallmarks-of-strong-software-security/
Category & Tags: Security Bloggers Network,Cybersecurity – Security Bloggers Network,Cybersecurity
Views: 0