Source: securityboulevard.com – Author: Veriti Research
In recent research by Veriti, a significant cyber security breach at Change Healthcare highlighted severe vulnerabilities in healthcare data security, affecting over 1.35 million files. This breach involved multiple healthcare and insurance providers, exposing sensitive data like medical records and personal identifiers, leading to far-reaching implications. The study aims to underscore the critical need for proactive and safe remediation across interconnected healthcare networks
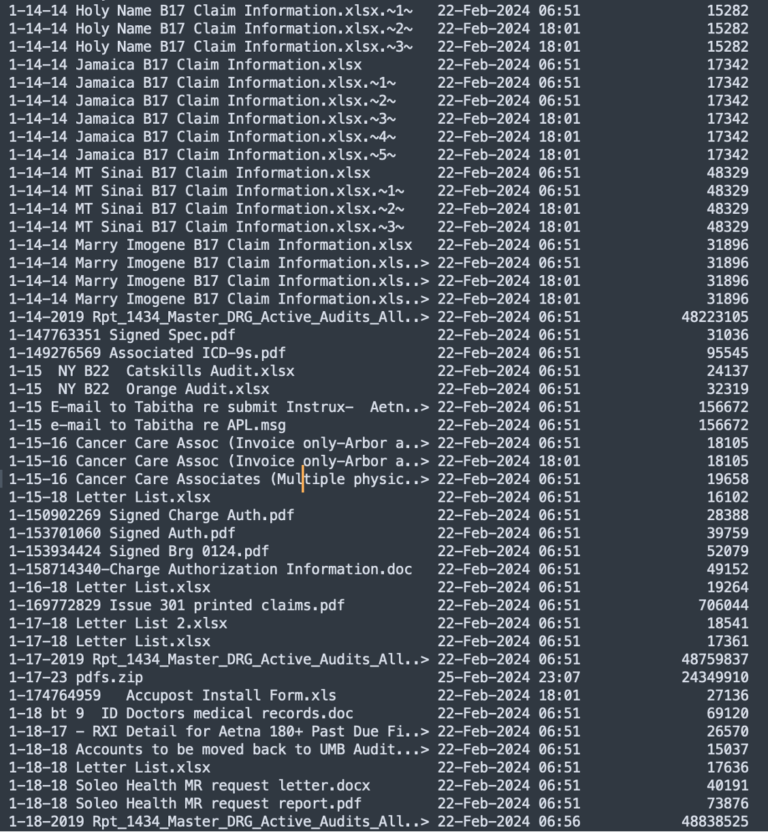
Example for sensitive data that was stolen:

Searching for the exposed vein: how the attackers started
In the recent attack on Change Healthcare, part of UnitedHealth Group, the ransomware group BlackCat, also known as AlphV, exploited crucial data exchange processes between healthcare providers and insurers. This breach led to the exposure of a vast array of sensitive information including medical records, financial details, and personal identifiers like Social Security numbers. The implications of such a breach are profound, affecting countless individuals and organizations connected within the healthcare ecosystem.
Spreading like cancer: the impact of the breach
Veriti’s research identified at least 30 organizations that were directly impacted by the breach. Among these, prominent health insurers like UnitedHealthcare, Blue Cross Blue Shield, Humana, and CareFirst have been severely affected due to their reliance on Change Healthcare for crucial data processing and claims management.
In addition to insurers, several regional hospitals and healthcare systems have felt the breach’s impact, including Erlanger Health System, Appalachian Regional Healthcare, Pelham Medical Center, and others spread across the U.S. longer-term challenges These institutions may not only be dealing with the immediate fallout from disrupted operational and financial processes, but are also facing long-term challenges related to patient trust and data security.
Tech-oriented healthcare entities like PatientPay & Epic Systems have also been impacted, facing potential risks related to intellectual property theft and loss of client confidence. Similarly, organizations with a broader humanitarian reach, such as the American Red Cross, as well as the National Council on Aging (NCOA), which deals with sensitive elderly information, are confronting issues related to the security of donor and volunteer information, which could affect their crucial operations and public perception. The exposure of such critical data places millions of individuals at risk of identity theft and financial fraud.
The geographic spread of the breach’s impact is extensive, affecting entities across multiple states, from large urban centers to smaller regional locales. The interconnected nature of modern healthcare infrastructure and the broad scale of potential disruption can stem from a single point of failure in cyber security measures.
The insights from Veriti research leads us to one conclusion for healthcare, the need to adopt continuous exposure assessment and safe remediation across the sector.
Sec and the Business: A Security Pro’s Guide to Exposure Assessments and RemediationUnderstanding the impact of remediation is crucial for mitigating the risks associated with security actions and ensuring that these interventions do not inadvertently compromise business operations. By conducting comprehensive impact analyses before implementing remediation measures, organizations can anticipate potential disruptions and weigh the benefits of security enhancements against operational risks. This involves evaluating the potential for:
- System Downtime
- The effect on User Experience
- False Positives leading to Business Disruption
Such assessments enable security teams to tailor their remediation strategies in a way that maximizes security benefits while minimizing any negative impact on business processes, ensuring that the organization maintains its operational integrity and resilience in the face of necessary security improvements.
References for Research:
Distribution by Known File Types:

File Types Per Category:
- Document: csv, doc, fmt, html, pdf, ppt, rpt, rtf, txt, xls, xml
- Executable: bat, cmd, dll, exe, jar
- Data File: bcp, cfg, dat, dbf, edi, log, mdb, pgp, sql, tmp, zip
- Image: bmp, emf, gif, img, jpg, png, tif
- Email: email, msg
File Types Count:
| pdf: 204398log: 111751txt: 61380html: 43981zip: 25655bcp: 23117csv: 16552email: 13333pgp: 7008emf: 5981xls: 5287edi: 4614grp: 3104ppq: 3034rcv: 2756png: 2529ack: 2491doc: 2127sql: 1848msg: 1614xml: 1488def: 1192rtf: 1084fmt: 927jpg: 913rpt: 716eps: 435 | dll: 432pkg: 375trn: 343lnk: 340eob: 331stm: 250941: 231pcx: 203mdb: 193err: 185asc: 172lxf: 167exe: 153dat: 150duc: 143dbf: 141tgz: 133prg: 131era: 129000: 112271: 100837: 99out: 99don: 98url: 91dtd: 90pma: 90 | trc: 83pdb: 78gif: 78css: 75bad: 74bch: 71xlk: 70cmp: 64fix: 64sfv: 64bat: 63hrr: 61ini: 58inq: 55hrn: 50prt: 45ttf: 44wav: 39del: 38tag: 37cli: 35cdx: 35ppt: 35ghr: 32bak: 30ldf: 29hhr: 28 | vsd: 28msi: 27bmp: 26cfg: 24obj: 24tmp: 23cab: 23chm: 23cpp: 22nte: 21img: 21tif: 20cmd: 20jar: 18 |
Distribution of File Sizes in Megabytes:

File count by Associated Organization:
| San Mateo County Health: 105756Epic Systems Corporation: 57639OpenText StreamServe: 49099Community Oncology Alliance: 45406Pelham Medical Center: 34893Health Partners Plans: 31955University Medical Center: 16183Carolinas Medical Center: 2606PatientPay: 8227American Red Cross: 5416Appalachian Regional Healthcare: 5127Arkansas Best Corporation: 3124Community Health Centers: 2606Appalachian Regional Healthcare in Montana: 2415Humana Inc.: 2015 | Erlanger Health System: 1947Anthem Inc.: 1934Aetna Inc.: 1831UnitedHealthcare: 1692Geisinger Health: 1572Massachusetts Nurses Association: 1511Blue Cross Blue Shield: 944Palmetto GBA: 1449MedicAid: 620Change Healthcare: 781CareFirst: 551NCOA: 573Whitesburg: 494Middlesboro: 459McDowell: 443 |
Life Support aka Safe Remediation
The final analysis on Change Healthcare reveals a compelling narrative on the critical need for safe and calculated remediation strategies in the healthcare sector. Addressing vulnerabilities with smart remediation plans is essential to ensure that necessary security updates do not lead to unintended consequences such as system downtime, degraded user experience, or operational disruptions due to false positives. This approach helps maintain the operational integrity and trust essential in healthcare, ensuring systems remain robust and secure while minimizing impacts on critical healthcare services and patient care.
The post Hospitals Hacked: Urgent Care Needed appeared first on VERITI.
*** This is a Security Bloggers Network syndicated blog from VERITI authored by Veriti Research. Read the original post at: https://veriti.ai/blog/hospitals-hacked-urgent-care-needed/
Original Post URL: https://securityboulevard.com/2024/05/hospitals-hacked-urgent-care-needed/
Category & Tags: Security Bloggers Network,Blog,research – Security Bloggers Network,Blog,research
Views: 0