Source: www.bleepingcomputer.com – Author: Bill Toulas

Security researchers warn that the ‘Advanced Custom Fields’ and ‘Advanced Custom Fields Pro’ WordPress plugins, with millions of installs, are vulnerable to cross-site scripting attacks (XSS).
The two plugins are among WordPress’s most popular custom field builders, with 2,000,000 active installs on sites worldwide.
Patchstack’s researcher Rafie Muhammad discovered the high-severity reflected XSS vulnerability on May 2, 2023, which was assigned the identifier CVE-2023-30777.
XSS bugs generally allow attackers to inject malicious scripts on websites viewed by others, resulting in the execution of code on the visitor’s web browser.
Patchstack says the XSS flaw could allow an unauthenticated attacker to steal sensitive information and escalate their privileges on an impacted WordPress site.
“Note that this vulnerability could be triggered on a default installation or configuration of Advanced Custom Fields plugin,” explains Patchstack in the bulletin.
“The XSS also could only be triggered from logged-in users that have access to the Advanced Custom Fields plugin.”
This means that the unauthenticated attacker would still have to social engineer someone with access to the plugin to visit a malicious URL to trigger the flaw.
The plugin’s developer was notified of the issue upon Patchstack’s discovery and released a security update on May 4, 2023, in version 6.1.6.
The XSS flaw
The CVE-2023-30777 flaw stems from the ‘admin_body_class’ function handler, which failed to properly sanitize the output value of a hook that controls and filters the CSS classes (design and layout) for the main body tag in the admin area of WordPress sites.
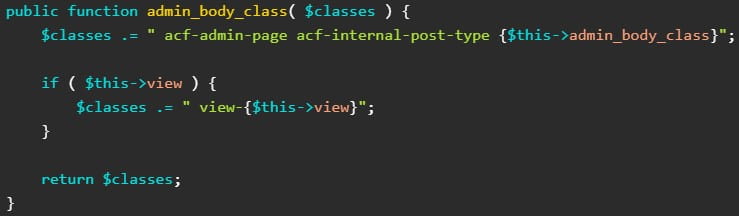
An attacker can leverage an unsafe direct code concatenation on the plugin’s code, specifically the ‘$this→view’ variable, to add harmful code (DOM XSS payloads) in its components that will pass to the final product, a class string.
The cleaning function used by the plugin, ‘sanitize_text_field,’ will not stop the attack because it won’t catch the malicious code injection.
All users of ‘Advanced Custom Fields’ and ‘Advanced Custom Fields Pro’ are advised to upgrade to version 6.1.6 or later as soon as possible.
Based on WordPress.org download stats, 72.1% of the plugin’s users are still using versions below 6.1, which are vulnerable to XSS and other known flaws.
Original Post URL: https://www.bleepingcomputer.com/news/security/wordpress-custom-field-plugin-bug-exposes-over-1m-sites-to-xss-attacks/
Category & Tags: Security – Security
- May 5, 2023
- 3:39 pm
- No Comments
- CISO2CISO post categories: 0 - CT, 0 - CT - SOC - CSIRT Operations - Cyber Incidents & Attacks Notepad, BLEEPINGCOMPUTER, Cyber Security News, rss-feed-post-generator-echo, Security




















































