Source: www.bleepingcomputer.com – Author: Bill Toulas

A Phemedrone information-stealing malware campaign exploits a Microsoft Defender SmartScreen vulnerability (CVE-2023-36025) to bypass Windows security prompts when opening URL files.
Phemedrone is a new open-source info-stealer malware that harvests data stored in web browsers, cryptocurrency wallets, and software like Discord, Steam, and Telegram. This data is then sent back to the attackers to be used in other malicious activities or to be sold to other threat actors.
The Microsoft Defender flaw exploited in the Phemedrone campaign is CVE-2023-36025, which was fixed during the November 2023 Patch Tuesday, where it was marked as actively exploited in attacks.
“The user would have to click on a specially crafted Internet Shortcut (.URL) or a hyperlink pointing to an Internet Shortcut file to be compromised by the attacker,” explains the CVE-2023-36025 security bulletin.
Not many details were initially shared about the exploitation of CVE-2023-36025 in the wild, but proof-of-concept exploits published shortly after elevated the risk for unpatched Windows systems.
Trend Micro’s researchers report that the Phemedrone campaign is not the only malware family they’ve seen targeting the particular flaw in Windows, with other cases involving ransomware.
Bypassing SmartScreen
The attackers host malicious URL files on trustworthy cloud services like Discord and FireTransfer.io and often disguise them using shortener services like shorturl.at.
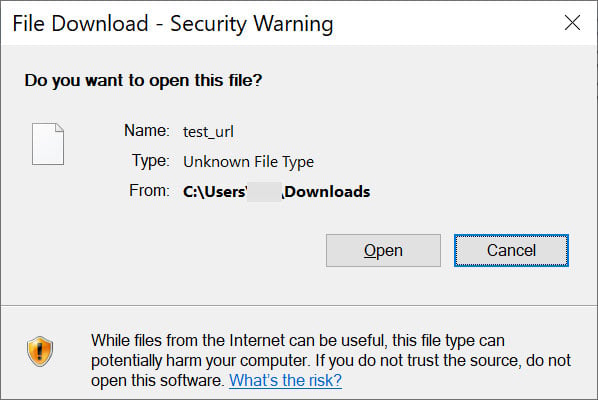
Usually, when opening URL files downloaded from the internet or sent via email, Windows SmartScreen will display a warning that opening the file could harm the computer.
Source: BleepingComputer
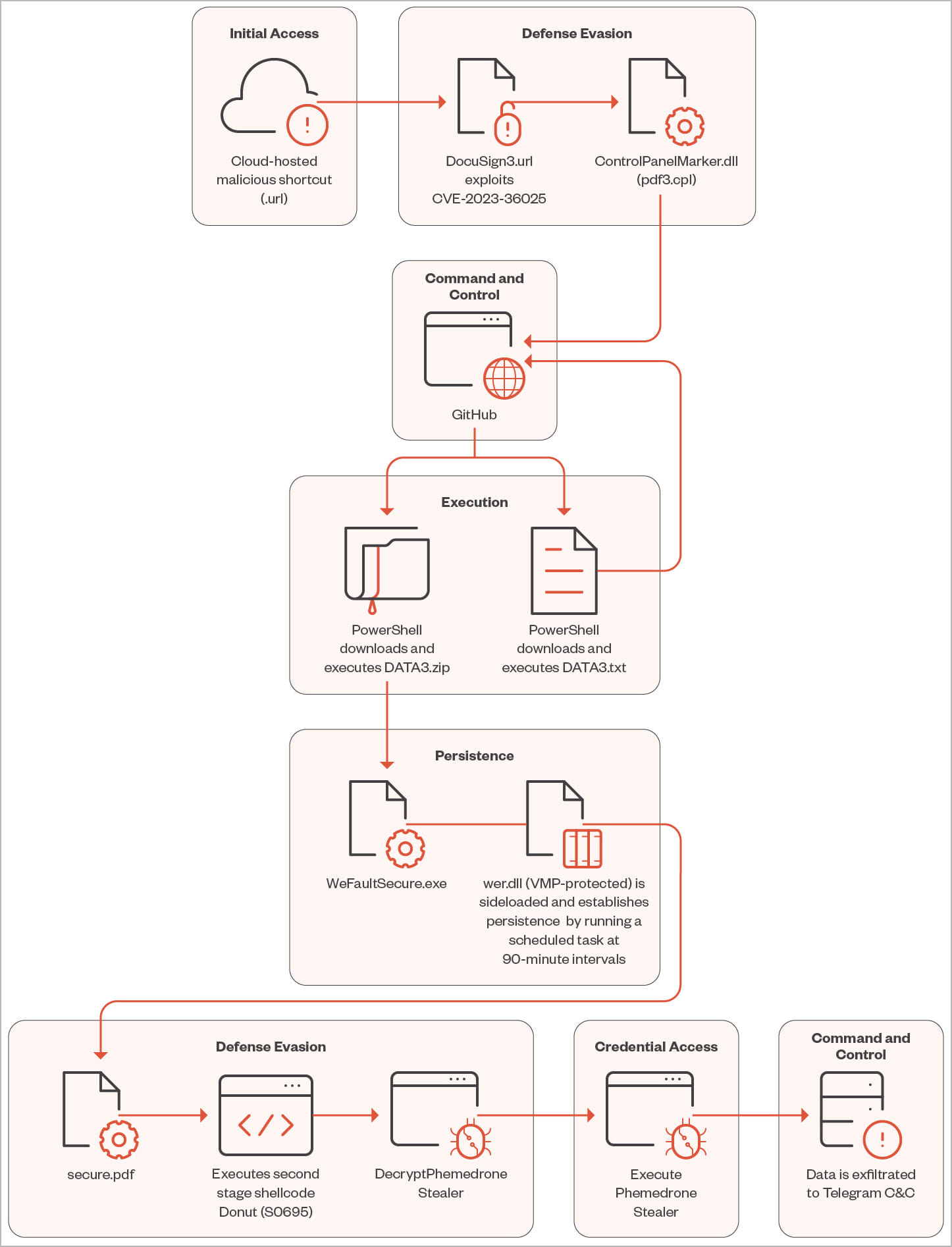
However, when the victim is tricked into opening one of the malicious URL files, they exploit the CVE-2023-36095 flaw in Windows SmartScreen so that this prompt is not shown and the command is executed automatically.
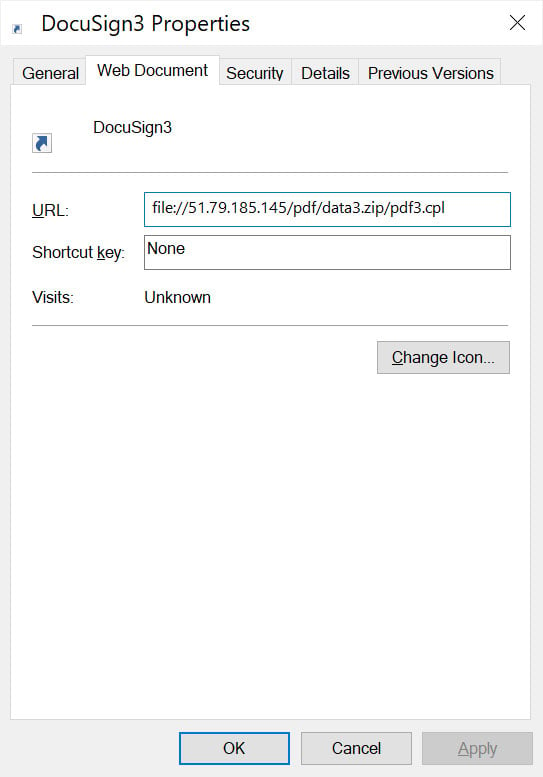
The URL file downloads a control panel item (.cpl) file from the attacker’s control server and executes it, launching a malicious DLL payload via rundll32.exe.
Source: BleepingComputer
The DLL is a PowerShell loader that fetches a ZIP file from a GitHub repository containing the second-stage loader masqueraded as a PDF file (Secure.pdf), a legitimate Windows binary (WerFaultSecure.exe), and ‘wer.dll,’ used in DLL side-loading and to establish persistence.
Source: Trend Micro
Once launched on the compromised system, Phemedrone initializes its configuration, decrypts necessary items, and steals data from targeted applications, using Telegram for data exfiltration.
Trend Micro reports that Phemedrone targets the following apps/data:
- Chromium browsers: Harvests passwords, cookies, and autofill from browsers and security apps like LastPass, KeePass, Microsoft Authenticator, and Google Authenticator.
- Gecko browsers: Extracts user data from Gecko-based browsers like Firefox.
- Crypto wallets: Extracts data from various crypto wallet apps, including Atom, Armory, Electrum, and Exodus.
- Discord: Gains unauthorized access by extracting authentication tokens.
- FileGrabber: Collects user files from folders like Documents and Desktop.
- FileZilla: Captures FTP details and credentials.
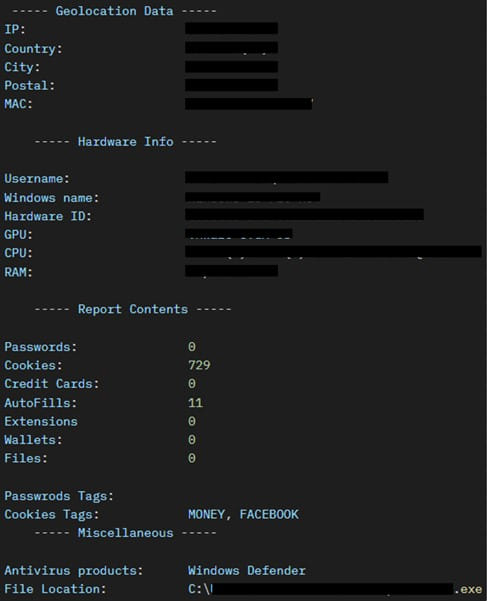
- System info: Gathers hardware specs, geolocation, OS details, and screenshots.
- Steam: Accesses files related to the platform.
- Telegram: Extracts user data, focusing on authentication files in the “tdata” folder.
Source: Trend Micro
Trend Micro has published the complete list of indicators of compromise (IoCs) for the newly observed Phemedrone campaign here.
Original Post URL: https://www.bleepingcomputer.com/news/security/windows-smartscreen-flaw-exploited-to-drop-phemedrone-malware/
Category & Tags: Security,Microsoft – Security,Microsoft




















































