Source: heimdalsecurity.com – Author: Livia Gyongyoși
“We have so many solutions now to solve single issues in our companies that the number of security solutions is becoming a risk itself” – Thomas Baasnes, Cybersecurity Director at Verdane.
How many cybersecurity point solutions does your organization use?
In an IBM survey, the average number of tools used in the businesses they asked was 45. But the exact figure likely depends on the size of your organization. According to one expert’s estimate, small companies have 15-20 on average, medium-sized firms use 50-60, and large enterprises deploy over 130.
This seems like an awful lot of tools. What is going on here? Why do organizations deploy so many cybersecurity point solutions? And why is it a problem?
In this blog, we will discuss:
- The causes behind the boom in cybersecurity point solutions
- Why the proliferation of tools is a problem
- How a cybersecurity platform model helps
The boom in cybersecurity point solutions
In a recent Heimdal webinar, we spoke with Thomas Baasnes of private equity firm Verdane. Thomas is the company’s cybersecurity lead – whenever they invest in a new company, he does due diligence to ensure those firms have appropriate cyber defenses in place.
During the webinar, Thomas described an issue he sees more and more today:
In my perspective, what has happened in the security industry for the last few years is that as the awareness [of cyber threats] in the market has increased … you have a lot of solution providers that have been coming up with new solutions for solving single problems.
Source – Thomas Baasnes webinar
There are now dozens of tools available that can be deployed on company networks to monitor for an ever-growing range of risks. Even a small company might be using 20 tools from multiple different providers – everything from standard antivirus or firewalls, through to fairly niche tech like intrusion detection systems or Wi-Fi protection software.
What’s behind the boom in cybersecurity point solutions?
There are several reasons why we’ve seen such a large rise in cybersecurity point solutions, including:
- Awareness: As Thomas alluded to, many companies are now more aware of cyber threats and have increased their budgets for cyber defenses as a result. Security staff will, naturally enough, invest in more tooling.
- Increased exposure: The simple fact is that most organizations are now facing a much higher level of security hazard than in the past. More work is done online, remotely, and people use more devices than ever. As a consequence, the attack surface grew.
- Fear, uncertainty and doubt (FUD): No one wants to be the person who said “no” to spending money on a cybersecurity tool that might have protected the company from a breach. Arguably, some cybersecurity spend goes on tools that probably aren’t necessary, but that people pay for out of ‘FUD’.
- Innovation: Vendors of cybersecurity point solutions are motivated to create new tools that will meet a market demand, respond to new types of threats, or new kinds of technology. They have effective sales and marketing departments to promote these tools.
For better or worse, these factors have driven up the number of tools all kinds of companies use to defend themselves. But, while keeping your data protected is of course vital, this approach does create problems.
The danger of having too many cybersecurity tools
During the webinar, Thomas noted that many companies have a large number of tools to manage various cyber risks. While this might at first seem like a sensible approach, it can actually be very problematic. Thomas sees the growth in cybersecurity point solutions as risky because:
All these tools need to be maintained, they need to be updated, you know they have license cost and it increases the complexity of your IT environment.
Source – Thomas Baasnes webinar
Let’s dig into the problems with having too many cybersecurity tools in a little more detail.
Siloes
If you have dozens of point solutions then information about your security posture inevitably becomes siloed. Your IT teams need to login to multiple systems to keep track of possible threats, and you don’t get a single view of your security position. As a result, misunderstandings can occur and alerts might be missed.
Notification overload
We’ve written before about the sheer number of notifications that security staff receive every day from security tools. The more point solutions you install, the more notifications you’re going to receive. And, unless you have enormous resources to deal with them all, many alerts will end up being ignored.
Creates security gaps
If your security tools are built by different vendors and don’t ‘talk’ to one another, hackers may be able to exploit gaps between them. For example, in a ‘living off the land’ (LotL) style breach, hackers can use endpoints as an entry to your wider system. Even if you had an endpoint security solution in place, it might still be possible for hackers to bypass it. If they get past that first layer, they can then move sideways without any further obstacles.
Encourages complacency
Having dozens of security point solutions can lead organizations to overestimate their level of protection. Paying for lots of tools means businesses may assume that they’ve got every base covered. This can lead to complacency about security and a failure to be alert to new threats. Remember – the top causes of data breaches remain simple human errors that tools often cannot prevent (such as emailing data to the wrong recipient).
Does it actually work?
If the figures we mentioned above are to be believed, organizations are using far more security tools than ever before. Yet is this really solving the problem? In 2023, we saw record numbers of data compromises – even though organizations are supposedly using more security tools. This suggests the current approach just isn’t working.
Cost, time and practicality
In the same webinar, Heimdal’s Cybersecurity Solutions Expert, Andrei Hinodache, described some of the other issues that come with using multiple cybersecurity point solutions:
“Each cybersecurity product you implement takes time, right? You need to look at them, you then need to do meetings with the vendors, then you need to do proof of concepts. After that, you choose a product, you start implementation, then you need to do internal training, then you need to do some user communication so that they know that a new system is on the computer, and so on and so forth”.
This is bad enough for smaller companies with, say, 15-20 point solutions. But if you’re using dozens, or even hundreds of these tools, then the process becomes incredibly time consuming, expensive and inefficient.
Keep it simple: the platform approach to cybersecurity
If your cybersecurity team is using dozens, or even hundreds of point solutions, there is an alternative: the cybersecurity platform approach.
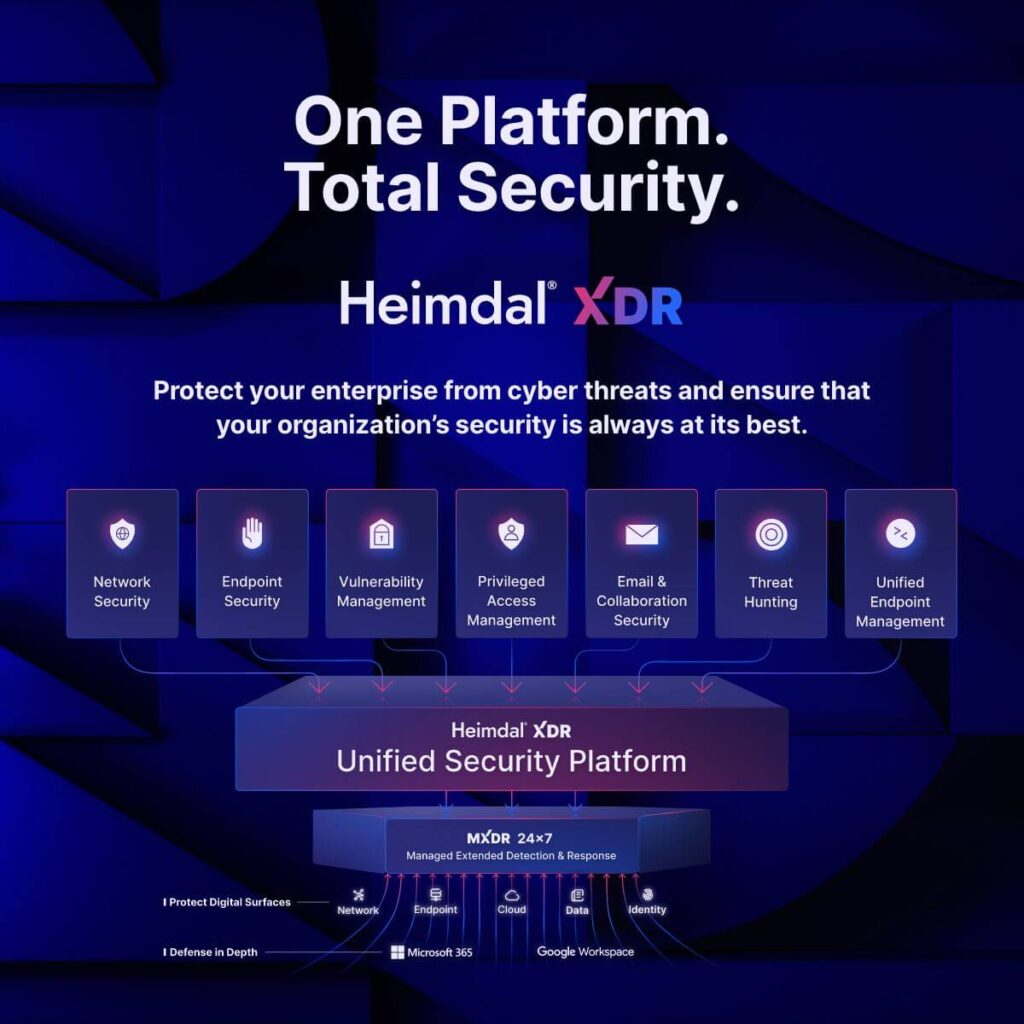
The aim of cybersecurity platforms is to provide you with all the tools you would need to keep your environment secure, in a single place. You then select the specific tools you want from the range and deploy them across your network.
So, rather than having an antivirus from Company A, an endpoint detection & response tool from Company B and a threat hunting solution from Company C, you get them all in one package from Company Z.
There are several reasons why this approach is attractive:
Single pane of glass
Using a cybersecurity platform gives you a ‘single pane of glass’ view of all your tools and data. Instead of logging into and monitoring dozens of cybersecurity point solutions, you get all data from all tools drawn into a single dashboard. From there, you can make sense of information, identify threats easily and prioritize your response.
Closes security gaps
When you use multiple tools from different vendors, they do not ‘talk to each other’. This means that a hacker can exploit these gaps and move laterally through your environment. On the other hand, if all your tools are supplied by one vendor, they ‘understand’ each other and can identify suspicious activity on the network much faster (even if the hacker has bypassed one layer of defense).
Flex, scale and power
Within an environment like Heimdal’s Unified Security Platform, you can access dozens of point solutions. You might start with core products (e.g. network security or ransomware protection). But you can then add more tools at the click of a button. And, since they all have a similar interface and user experience, the learning curve is much shorter.
Efficiency
Using a cybersecurity platform is just much more efficient than relying on dozens of different tools. It’s much less expensive to get all your tools from one vendor, it’s far easier to manage (so you don’t need as many people to monitor it), and you don’t need to spend hours searching for new vendors each time you want to install an additional tool.
Time to end your reliance on cybersecurity point solutions?
Around the world, organizations are using more cybersecurity point solutions than ever before. Yet, given the continually rising number of breaches, it seems like this approach just isn’t working.
A cybersecurity platform can solve many of the risks that emerge from the current reliance on point solutions. From closing security gaps, to relieving alert fatigue, and cutting costs, shifting to this approach has the potential to significantly reduce breaches while making security far more effective.
Heimdal’s Unified Security Platform is already used by dozens/hundreds/thousands of companies to achieve more comprehensive, efficient and effective security. It gives you access to numerous state-of-the-art point solutions that all work seamlessly together. You can monitor and manage all through a single pane of glass.
Ready to end your dependence on cybersecurity point solutions? Get a Heimdal demo and see how a cybersecurity platform would work for you today.
Frequently asked questions
What is a cybersecurity point solution?
A cybersecurity point solution is a tool that is designed to protect your organization from one specific kind of threat. These tools are specialized and are very effective at tackling the kinds of attacks they’re built to deal with. For example, there are point solutions to address ransomware attacks, DoS attacks or code injection attacks.
Is a cybersecurity platform too ‘generalist’ in its approach to protection?
It depends. It’s true that some cybersecurity platforms offer a limited number of tools. Yes, this means you may not get the same level of power or control as you’d get from highly specialized point solutions. However, not all cybersecurity platforms are the same. Some are very advanced and will provide you with a large number of best-in-class tools, which means you don’t have to compromise on quality.
Can you use point solutions alongside a cybersecurity platform?
Yes, you often can. With Heimdal’s Unified Security Platform, our focus is on flexibility. Of course, we encourage you to use Heimdal’s tools as your primary form of security, but you are not ‘locked in’. You can also use specific point solutions that you rely on for very unique use cases, then use our platform for everything else.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.
Newsletter
If you liked this post, you will enjoy our newsletter.
Get cybersecurity updates you’ll actually want to read directly in your inbox.
Livia Gyongyoși is a Communications and PR Officer within Heimdal®, passionate about cybersecurity. Always interested in being up to date with the latest news regarding this domain, Livia’s goal is to keep others informed about best practices and solutions that help avoid cyberattacks.
Original Post URL: https://heimdalsecurity.com/blog/cybersecurity-point-solutions-risk/
Category & Tags: Cybersecurity Basics – Cybersecurity Basics
Views: 0