Source: heimdalsecurity.com – Author: Cristian Neagu
What Is Patch Management?
Patch management is the process of identifying and deploying software updates. It is an important process that involves the acquisition, review, and deployment of ‘patches’ to IT infrastructure. The ‘patches’ are pieces of software code that improve an installed program – you can literally think about it as a ‘bandage’ applied to software. Common areas which need patches include operating systems, applications, and embedded systems such as network equipment. Patch management is sometimes considered part of the vulnerability management process.
Every time a security flaw or bug is discovered, or the program’s functionality needs to be enhanced, software developers create a patch to address these aspects. Patches can be deployed to your entire infrastructure including software/operating systems, routers, IoT equipment, servers, and more.
Patch Management vs. Vulnerability Management
These two practices are often mistaken to be the same one, but in reality they are not. Patching represents only a string in the net that keeps threat actors at bay, and is a part of the larger vulnerability management process. Vulnerability management is a process that involves detecting, assessing, remediating, and reporting vulnerabilities and threats found in a company’s or organization’s network.
Based on the severity level of the detected vulnerability, there are different methods which need to be employed in order to eliminate the threat, patch management is one of these techniques. If you want to learn more about the differences between the two processes, we recommend you read this article on patch vs vulnerability management, where we tackled the subject more in-depth.
Why Is Patch Management Important?
Ultimately, one of the primary goals of patch management is to safeguard your endpoints from threat actors and maintain optimal system performance. However, patch management also offers a number of other advantages:
- Reducing the attack surface: applications and software might have different vulnerabilities a hacker could exploit. By patching them, an organization is less exposed to cyberattacks or security breaches. Patching works as a prevention measure against many types of malware that can spread fast throughout a network.
- Increased productivity: patches can fix different errors and bugs and thus increase system stability. Your employees won’t come across system bugs or downtime every 2 days, so they will not waste unnecessary time waiting for the bug to be fixed. It takes on average 14 days to manually patch all the endpoints in an organization, and this number can increase based on the number of devices, but with our automated solution this process is done is less than 4 hours.
- Enhanced functionality: patching does not only fix software flaws, it can also improve features, as software updates often mean enhanced functionality.
- System uptime: a reliable patch management process ensures that your software and applications are kept up-to-date and run smoothly, supporting system uptime.
- Spotting old software: if your software vendor is out of business or has another problem, this solution will help you identify the software that has not received updates in a long time, so you can replace it in a timely manner.
- Achieving compliance: the required level of conformity with different regulations is accomplished and also the audit results will be satisfactory.
The Biggest Risks Associated With Improper Patching
A proper patch management strategy can really make the difference between a strong cybersecurity posture and a poor one. Poor patching practices can lead to the following risks:
1. Security Vulnerabilities
A vulnerability is a flaw that hostile actors can exploit in software, hardware, or systems. Operating systems and apps both have vulnerabilities. They can also be the result of bad design decisions or code mistakes. Because they require security patch management procedures with sufficient controls over access to vulnerable systems and networks, vulnerabilities are one of the most frequent reasons why patches fail.
2. Lost Data, Leakage, and Data Theft
Unpatched vulnerabilities, according to recently released studies, account for more than 60% of data breaches. Unexpectedly, firms aggressively search for vulnerabilities, but they might improve their patch management software or procedures. In order to minimize costly business interruptions and downtime, firms frequently forego patching, which contributes to data breaches.
3. Phishing and Social Engineering Attacks
Social engineering involves tricking someone into enabling access to data networks or revealing sensitive information. Phishing is a common attack that involves an email or text message posing as coming from a reliable source and requesting information. During a phishing scheme, malicious actors search for open windows or missing patches.
4. Compliance Violations
When organizations fail to patch vulnerabilities as soon as they become aware of them or put insufficient patch management procedures, compliance and audit problems may result. Your organization’s ability to comply with important cybersecurity standards or industry requirements may be hampered if your network devices aren’t getting frequent updates.
The Key Steps of a Patch Management Process
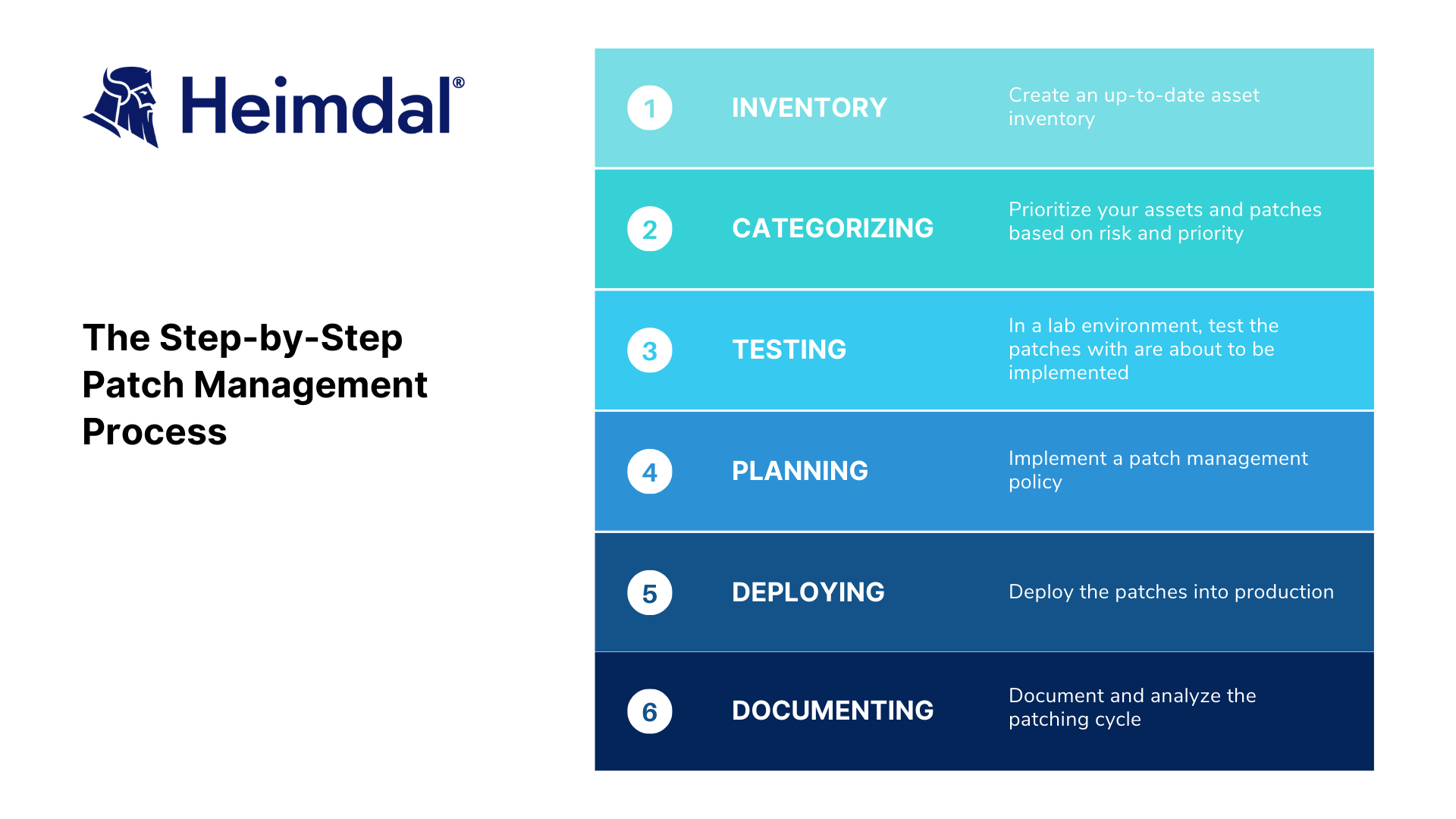
If you want to have a seamless and effective patch management process, there are a few stages that must be followed during the patching process. Here are the key steps:
- Develop an up-to-date IT asset inventory of all your current software solutions and devices.
- Categorize assets and patches by risk and priority. An inventory will help you define if the existing patches meet your software needs and determine which applications are vulnerable and their level of importance or sense of urgency. Choose a patch management tool that will fit your needs and target the most vulnerable parts of your system, as patch management is part of vulnerability management – a topic that goes hand in hand when talking about patching. This tool will scan for available patches, then it will analyse the results and determine what needs to be patched, it will apply the patches and eventually monitor the process.
- Test the patches in a lab environment prior to production. You should determine if your software supports the vendor’s patches you want to use, before deploying live. A testbed that imitates your production network is a good solution to determine if your network will really support the patch you want to apply. This part comes with disadvantages too, because it will take time and make use of the organization’s resources and will delay the patching process itself.
- Plan the release into production and implement a patch management policy. A patch management policy will set clear rules to make sure your patching process runs the right way, schedule patches to be applied on time, and document patching results properly.
- Deploy the patches into production. It is recommended to deploy in small batches when you’re going live. Even if your lab tests went smoothly there’s always a chance to encounter conflicts in a production environment.
- Asses and document the results. Documenting and analyzing every patching cycle will help you improve and optimize the patching process.
An automated patching solution is desirable if you want your organization to be protected and updated constantly. Heimdal’s Patch & Asset Management solution is specifically designed to streamline the patch management process so that you won’t have to worry about cyberattacks or data breaches. Our automated patching system will make sure that your software, systems, or devices are always up-to-date and protected against the latest threats.
Multiple deployment tools may create confusion in your operations, slow down your reaction time, and ultimately open your organization to devastating malware, breaches, ransomware, and other types of attacks. But with Heimdal®, you have everything you need in one place:
- Software & Asset Inventory;
- Vulnerability Management;
- Automated Patch Management and Deployment (for both proprietary and third-party software).
all with granular controls for precise actions, accessible anytime from anywhere in the world.
Book a meeting with our experts and discover how our solution will help you improve your organization’s cybersecurity posture!
Automate your patch management routine.
Heimdal® Patch & Asset Management Software
Remotely and automatically install Windows, Linux and 3rd party application updates and manage your software inventory.
- Schedule updates at your convenience;
- See any software assets in inventory;
- Global deployment and LAN P2P;
- And much more than we can fit in here…
Patch Management Best Practices
Creating the optimal patch management strategy starts with evaluating all the necessary steps involved. Here are the best patch management practices for you to implement today:
- Create an Asset Inventory;
- Determine and Prioritize Your Assets Based on Risks;
- Establish a top-notch Patch Management Policy;
- Test the Patches Prior to Deployment;
- Analyze the Results Pre and Post-Patching;
- Automate the Patching Process;
If you want to dive more in-depth into how to configure your patching strategy, we have an article on what are the best patch management practices to follow for you to check out.
Conclusion
A good automated patch management solution is a crucial aspect when it comes to software updates. Maintaining the security, integrity, and accessibility of the data and systems of every organization should be as thorough as possible but simple and fast in the same time. The more you keep up with your patching and update all your critical (and non-critical) systems, the less likely it is that your company will be compromised.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.
If you liked this post, you will enjoy our newsletter.
Get cybersecurity updates you’ll actually want to read directly in your inbox.
Original Post URL: https://heimdalsecurity.com/blog/patch-management/
Category & Tags: Patch management,patch management – Patch management,patch management





















































