Source: securityboulevard.com – Author: Michael Toback

Introduction
In today’s interconnected world, the significance of cybersecurity cannot be overstated. This is especially true as cyber threats continue to evolve at an alarming rate. The digital landscape of 2023 is fraught with sophisticated cyber-attacks, making robust security measures indispensable. Navigating through the intricate realms of cybersecurity, the debate surrounding “web application firewall vs firewall” emerges as a focal point. It illuminates the critical distinctions and synergies between these two fundamental pillars of digital protection.
In essence, the juxtaposition of a web application firewall vs a traditional firewall reveals the complementary roles they play in fortifying the cyber fortresses of organizations against the relentless onslaught of cyber adversaries. WAFs specialize in securing web applications. On the other hand, traditional firewalls are the guardians of network traffic. By doing so, each contributing uniquely to the overarching goal of maintaining a secure and resilient digital environment.
The Evolution of Firewalls
Tracing back the lineage of firewalls, we uncover a journey marked by continuous evolution and adaptation. Thus, reflecting the dynamic nature of the cyber realm. Firewalls, since their inception, have been the bulwarks of network security. They have evolved in tandem with the escalating sophistication of cyber threats.
In the early stages, firewalls were relatively simplistic. They were primarily designed to control inbound and outbound network traffic based on IP addresses and ports. These traditional firewalls are often referred to as packet-filtering firewalls. They operated at the network layer of the OSI model, serving as gatekeepers. Thus, allowing or blocking data packets based on predefined rules.
Firewalls: From the 1990s to the Present
This infographic illustrates the evolutionary journey of firewalls. Firewalls started from their inception in the early 1990s as packet filters. Now, they have become cloud-based and AI-driven. Each stage of evolution is represented with visual icons and brief descriptions. In doing so, it highlights the advancements in firewall technology over the years.
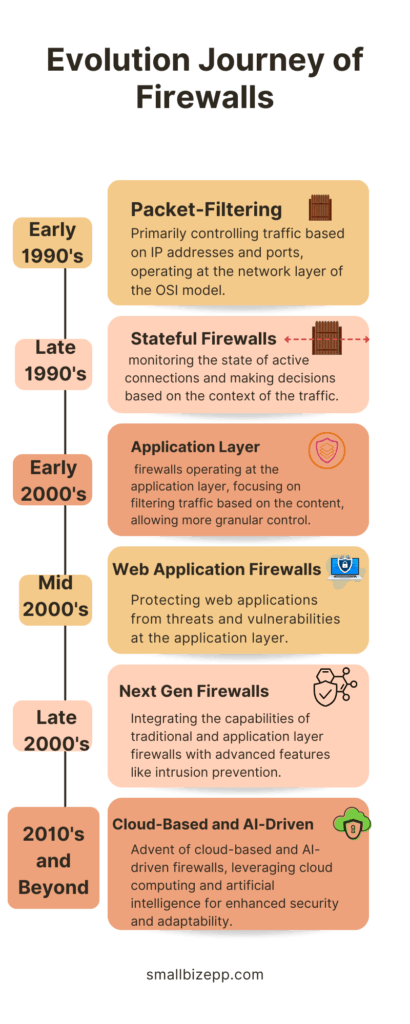
As cyber threats proliferated and diversified, the need for more advanced and nuanced security mechanisms became evident. This led to the development of stateful firewalls. Unlike their predecessors, stateful firewalls consider the state of active connections when making decisions. They monitor the state of active network connections. Thus, discern legitimate traffic from potentially malicious one, adding an extra layer of security.
Traditional firewalls focus on IP addresses, ports, and connection states. By doing so, they have been instrumental in protecting network perimeters from unauthorized access and various types of attacks. Traditional firewalls scrutinize network traffic. Thus, ensuring that only legitimate traffic traverses the network. Thereby maintaining the integrity and availability of network resources.
The rise of web applications and increase in application-layer attacks required a new focus on application layer security, beyond just network layer protection. This change highlighted the shortcomings of traditional firewalls, which couldn’t fully protect against advanced attacks targeting weaknesses in web applications.
In conclusion, the evolution of firewalls has been a response to the ever-changing threat landscape. From simple packet filtering to stateful inspection, traditional firewalls have paved the way for more advanced security solutions. They have adapted to meet the diverse and evolving needs of network security in the face of relentless cyber advancements.
What is a Web Application Firewall (WAF)?
A Web Application Firewall (WAF) is a specialized form of protection. It focuses on securing web applications from potential threats and vulnerabilities. The WAF operates at the application layer of the OSI model. It meticulously analyzes HTTP traffic to identify and block malicious request. Thereby it shields web applications from attacks such as SQL injection and cross-site scripting (XSS). WAFs are instrumental in defending against the myriad of cyber threats that target the intricate structures of web applications. Thus, ensuring the integrity and confidentiality of sensitive data processed by web apps.
The Web Application Firewall (WAF) is a specialized firewall designed to protect web applications from threats. Focusing mainly on Layer 7, the application layer of the OSI model. Unlike traditional firewalls which work at the network layer, WAFs examine traffic content more deeply to secure web applications.
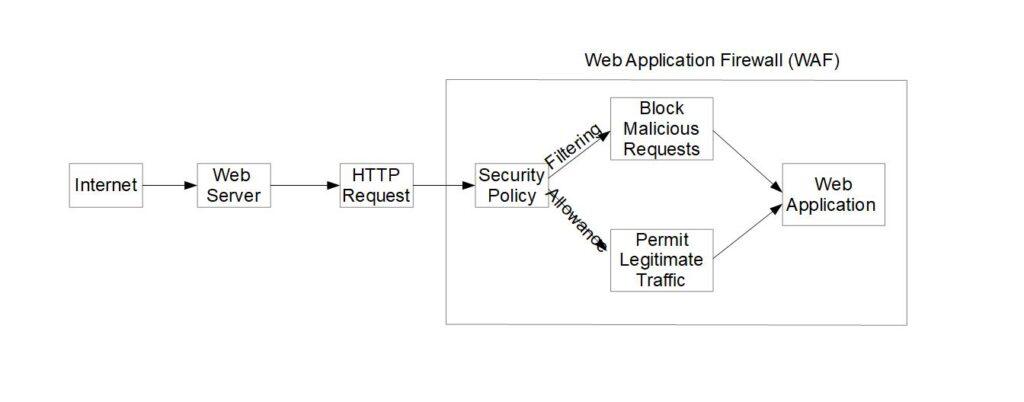
This diagram illustrates the intricate operation of a Web Application Firewall (WAF). The diagram depicts the flow of web traffic originating from the Internet. It then passes through the web server and being analyzed by the WAF based on predefined security policies. The WAF then makes decisive actions, either blocking malicious requests or permitting legitimate traffic to reach the web application.
WAFs play a pivotal role by providing a robust shield against types of attacks aimed at exploiting vulnerabilities inherent to web applications.. This includes a myriad of web application attacks such as Cross-Site Scripting (XSS) and SQL Injection. By operating at the application layer, WAFs are able to perform a more granular analysis of the incoming traffic. Thus, allowing them to discern between legitimate requests and potential threats with greater accuracy.
How WAFs Operate
WAFs operate by intercepting and analyzing incoming HTTP requests to a web application. WAFs employ a set of predefined security policies to filter the traffic. They serve to block requests that are deemed malicious and allowing those that are legitimate. This ensures that only safe and authorized access is granted to the web application. Thus, protecting the network from unauthorized access and potential exploitation.
Type of Security Provided by WAFs
WAFs provide specialized security aimed at protecting web applications from threats that traditional network firewalls may not be able to detect or prevent. They focus on securing web applications against attacks targeting vulnerabilities at the application level. Attacks such as SQL Injection, Cross-Site Scripting (XSS), and other OWASP Top Ten risks. By doing so, WAFs ensure the integrity, confidentiality, and availability of web applications. Thereby making them an indispensable component in the cybersecurity ecosystem, especially for web servers and internet-facing zones.
In conclusion, Web Application Firewalls (WAFs) stand as guardians of web applications. They provide a specialized layer of security that is crucial in the contemporary digital landscape. In this landscape, web applications are ubiquitous and the threats against them are ever-evolving. Businesses need to understand the operation and significance of WAFs. By doing so, businesses can better safeguard their web applications against the myriad of cyber threats lurking in the digital shadows.
What is a Traditional Firewall?
A traditional firewall serves as the first line of defense against cyber threats, operating predominantly at the network layer. The WAF monitors and controls incoming and outgoing network traffic based on predetermined security rules. Doing so, it protects local-area networks from unauthorized access and a variety of network-based attacks. Traditional firewalls are the sentinels of network security,. They safeguard the internal network infrastructure from the plethora of external threats lurking in the vast expanse of the internet.
Traditional firewalls play a pivotal role in network security. They operate predominantly at Layers 3 and 4 of the OSI model, dealing with the Network and Transport layers respectively. These layers are crucial as they manage the movement of data packets around the network. they also manage the end-to-end communication between the source and the destination.

Layered Security Approach
Referencing the above diagram, the traditional firewall begins its operation by receiving incoming traffic from the external network. This traffic, consisting of various data packets, is then subjected to meticulous analysis based on predefined firewall rules. These rules are the backbone of a firewall, determining which traffic is benign and which is potentially harmful.
Filtering and Allowing Traffic
Post analysis, the firewall rules aid in filtering the traffic. Unwanted traffic could be malicious or simply not compliant with the organization’s policy,. This treffic is blocked, preventing it from entering the internal network. This is depicted in the “Block Unwanted Traffic” block in the diagram.
Conversely, traffic deemed safe and compliant is allowed to permeate through the firewall to access the internal network. This is as illustrated in the “Permit Authorized Traffic” block. This selective permeability ensures that only legitimate and necessary communication occurs between the external and internal networks. Thus, safeguarding the integrity and confidentiality of the internal network.
Protection at Network and Transport Layers
Tradition firewalls focus on Layers 3 and 4 of the OSI model. They are adept at managing IP addresses and ports, ensuring that only authorized entities can communicate with the internal network. This level of operation allows them to efficiently block unauthorized access. In doing so, they protect the network from a myriad of attacks,. These attack types, such as DDoS, exploit vulnerabilities at these layers.
Conclusion on Traditional Firewalls
Traditional firewalls have a rule-based operation and focus on the Network and Transport layers. Thus, form the first line of defense against cyber threats. They are instrumental in maintaining a secure and resilient network environment. They do this by allowing legitimate traffic and blocking unwanted or malicious traffic based on the organization’s security policies.
WAF vs Firewall: A Detailed Comparison
Let’s compare the Web Application Firewall (WAF) with a Traditional Firewall. It’s pivotal to discern their distinct functionalities, protection mechanisms, and modes of operation, as illustrated in the comparison table below.
| Feature | Web Application Firewall (WAF) | Traditional Firewall |
|---|---|---|
| Layer of Operation | Layer 7 (Application Layer) | Layers 3 and 4 (Network and Transport Layers) |
| Protection Focus | Protects web applications from targeted attacks | Protects the entire network from unauthorized access |
| Traffic Analysis | Analyzes HTTP/HTTPS traffic | Analyzes all incoming and outgoing network traffic |
| Functionality | Protects against application-level attacks such as SQL Injection, Cross-Site Scripting (XSS) | Blocks unwanted traffic and permits authorized traffic based on IP addresses and ports |
| Deployment | Can be deployed in-line or out-of-band | Typically deployed in-line |
| Customization | Highly customizable to protect against specific application vulnerabilities | Customizable to an extent, mainly based on IP addresses, ports, and protocols |
| Use Case | Ideal for protecting web servers and applications | Ideal for protecting internal networks and systems |
| Performance Impact | May impact web application performance due to deep packet inspection | Minimal impact on network performance |
Layer of Operation
A WAF operates predominantly at Layer 7, the Application Layer of the OSI model. It focuses on the protection of web applications from specific, often sophisticated, attacks. In contrast, a Traditional Firewall operates at Layers 3 and 4, the Network and Transport Layers. Thus, safeguarding the entire network from unauthorized access and generic threats.
Protection Mechanisms
WAFs specialize in analyzing HTTP/HTTPS traffic, shielding web applications from application-level attacks such as SQL Injection and Cross-Site Scripting (XSS). They are highly customizable, allowing for tailored protection against specific vulnerabilities inherent to the web applications they protect.
Conversely, Traditional Firewalls analyze all incoming and outgoing network traffic. They then block unwanted traffic and permit authorized traffic based on predefined rules related to IP addresses, ports, and protocols. Their customization, while present, is mainly confined to these parameters.
Functionalities and Deployment
The deployment of WAFs can be either in-line or out-of-band, allowing for flexibility based on organizational needs. However, their deep packet inspection can potentially impact the performance of web applications.
Traditional Firewalls are typically deployed in-line and have minimal impact on network performance. In doing so, they serve as the first line of defense against unauthorized access and a variety of attacks,. These attacks, like DDoS attacks, exploit vulnerabilities at the Network and Transport Layers.
Conclusions on the WAF vs Firewall Comparison
Understanding the detailed comparison between WAF and Network Firewalls is crucial for implementing the right security measures. WAFs offer specialized protection for web applications. Traditional Firewalls provide a broader shield for networks against unauthorized access and generic threats. The choice between the two should align with the specific security needs. This includes the nature of the assets that require protection within an organization.
Diving into Web Application Traffic
Web Application Firewalls (WAFs) are specialized entities that delve deep into web application traffic to identify and mitigate a myriad of sophisticated attacks targeting the vulnerabilities inherent in web applications. They operate by scrutinizing the HTTP/HTTPS traffic between the web application and the user. Thus, allowing them to detect and prevent attacks that traditional firewalls might overlook.
Analyzing Web Application Traffic
WAFs employ advanced techniques to analyze the intricacies of web application traffic. They examine each HTTP request and response to identify patterns or signatures of known attacks. These are attacks on the web such as SQL injection and cross-site scripting (XSS). By doing so, they can block malicious requests before they reach the web application, thereby preserving its integrity and confidentiality.
Real-life Examples of Attacks Prevented by WAFs
- SQL Injection Attack on a Retail Website: A prominent retail website once fell victim to a SQL injection attack. The attackers attempted to manipulate the site’s database by injecting malicious SQL code through the website’s search bar. A well-configured WAF identified and blocked the malicious requests, preventing potential data breaches and maintaining the security of customer information.
- Cross-Site Scripting (XSS) Attack on a Social Media Platform: A popular social media platform was targeted by attackers utilizing cross-site scripting (XSS). The attackers attempted to inject malicious scripts into the platform’s web pages viewed by other users. The deployed WAF detected the abnormal scripts and promptly blocked them. Thus, safeguarding the users from malicious content and potential account hijackings.
- Layer 7 DDoS Attack on an E-Commerce Site: An e-commerce site experienced a Layer 7 DDoS attack. The attackers flooded the site with HTTP requests, overwhelming the server and disrupting the service. The site’s WAF was able to discern the illegitimate traffic from the legitimate one. In doing so, it mitigated the attack by blocking the malicious requests, ensuring the site’s availability and functionality.
Conclusions on Web Application Traffic Analysis by WAFs
Web Application Firewalls play a crucial role in analyzing and protecting web application traffic against various sophisticated attacks. The WAF exames the HTTP/HTTPS traffic and then employes advanced detection techniques. WAFs can then identify and block attacks such as SQL injection and cross-site scripting (XSS), ensuring the security and reliability of web applications in real-world scenarios. The real-life examples underscore the significance of WAFs in preserving the sanctity of web applications amidst a landscape riddled with evolving cyber threats.
Understanding Network Traffic Protection
Traditional firewalls stand as the sentinels of network security. They meticulously examining network traffic to shield local-area networks from unauthorized access and a plethora of cyber threats. The traditional firewall operates by enforcing predefined rules related to IP addresses, ports, and protocols. Thus, ensuring that only legitimate traffic is allowed, while potentially harmful traffic is blocked.
Examining Network Traffic
Traditional firewalls scrutinize every packet that traverses through them, comparing the packet’s information against the firewall’s rule set. If a packet complies with the established rules, it is allowed to pass; if not, it is blocked. This rule-based approach is fundamental in protecting networks from unauthorized access. It can prevent various attacks targeting the network and transport layers of the OSI model.
Real-life Examples of Attacks Prevented by Traditional Firewalls
- Port Scanning Attack on a Financial Institution: A major financial institution was the target of a port scanning attack. The attackers were probing the network to identify open ports and exploit vulnerabilities. The institution’s traditional firewall detected the unauthorized port scans and blocked the incoming traffic from the attacker’s IP address. Thus, preventing potential intrusions and safeguarding sensitive financial data.
- IP Spoofing Attack on a Healthcare Provider: A healthcare provider experienced an IP spoofing attack. The attackers were disguising themselves by using a forged IP address to gain unauthorized access to the network. The traditional firewall, with its rule-based approach, identified the discrepancy in the IP address. It thenpromptly blocked the malicious traffic, ensuring the security of patient information and medical records.
Conclusions on Network Traffic Protection by Traditional Firewalls
Understanding the mechanisms of how traditional or network firewalls protect network traffic is pivotal for maintaining a secure and resilient network environment. Traditional firewalls examine network traffic based on predefined rules to block unauthorized access and malicious traffic. In doing so, they play a crucial role in safeguarding local-area networks from a myriad of cyber threats. The real-life examples illustrate the efficacy of traditional firewalls in thwarting various attacks. In doing so, they preserve the integrity and confidentiality of networks in diverse sectors.
The Complementary Roles of WAF and Firewall
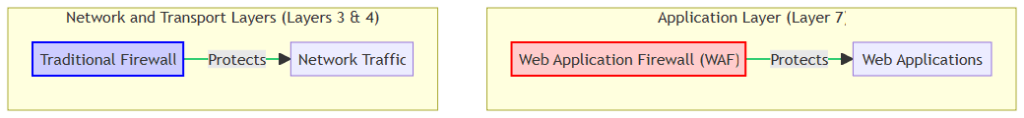
Web Application Firewalls (WAFs) and traditional firewalls emerge as complementary forces,. Each type of firewall fortifying distinct layers of the network against a myriad of cyber threats. The above diagram illustrates their synergistic roles in a layered security model. In doing so, it provides a visual guide to their operational realms within the OSI model.
Securing Different Layers
Traditional firewalls operate at the Network and Transport Layers (Layers 3 & 4) of the OSI model. In doing so, they serve as the guardians of network traffic. They meticulously scrutinize every packet that traverses the network, enforcing predefined rules related to IP addresses, ports, and protocols. It allows legitimate traffic and blocking potentially harmful ones. By doing so, traditional firewalls shield local-area networks from unauthorized access and a plethora of cyber threats.
Conversely, WAFs specialize in securing the Application Layer (OSI Layer 7), the layer where web applications reside. They focus on protecting web applications from specific, often sophisticated attacks such as SQL injection and cross-site scripting (XSS), which traditional firewalls might not detect. By analyzing the content of HTTP/HTTPS traffic, WAFs can identify and block malicious requests targeting web applications.
Comprehensive Security Approach
The integration of both WAFs and traditional firewalls provides a holistic security approach, ensuring that both the network traffic and web applications are shielded from various forms of cyber threats. Traditional firewalls lay the foundational security at the network level. WAFs extend this security to the application level, addressing the vulnerabilities inherent to web applications.
This complementary approach ensures that organizations can maintain a secure and resilient network environment, safeguarding their assets from the network layer to the application layer. By employing both firewalls, organizations can fortify their defenses against a broader spectrum of cyber threats. Thus, ensuring the integrity, confidentiality, and availability of their information and services.
In conclusion, the harmonious collaboration between WAFs and traditional firewalls is pivotal for achieving comprehensive security across different layers of the network. Their combined efforts provide a robust security posture. In doing so, it enables organizations to navigate the digital realm with enhanced confidence. Thus enhancing resilience against the ever-evolving landscape of cyber threats.
Next-Generation Firewalls: The Best of Both Worlds?
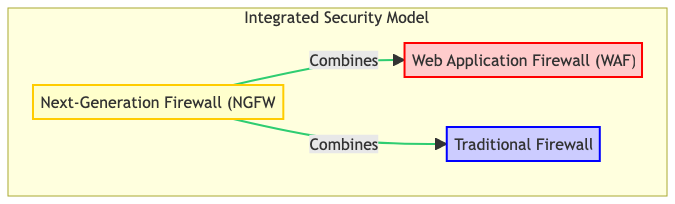
The advent of Next-Generation Firewalls (NGFWs) marks a significant stride forward. It amalgamates the specialized functionalities of Web Application Firewalls (WAFs) and traditional firewalls. This integration fosters a more robust and versatile security posture. In doing so, it is capable of thwarting a diverse array of cyber threats across different layers of the network.
Integrated Security Model
The integrated security model diagram above provides a visual representation of how NGFWs seamlessly blend the protective mechanisms of WAFs and traditional firewalls. It illustrates the convergence of application-level and network-level security features. Thus offering a holistic view of the enhanced security landscape facilitated by NGFWs.
Combining Specialized Functionalities
NGFWs stand as the epitome of integrated security solutions. It inherits the application-specific protections from WAFs and the network-centric defenses from traditional firewalls. NGFWs delve deep into the intricacies of web traffic. Scrutinizing application behaviors and content to identify and mitigate sophisticated threats such as application-layer attacks and zero-day exploits.
Enhanced Network Security
While traditional firewalls lay the foundational security by filtering IP addresses, ports, and protocols, NGFWs elevate this protection by incorporating advanced technologies like intrusion prevention systems (IPS) and deep packet inspection (DPI). This enhancement enables NGFWs to analyze the content and context of network traffic, allowing for more accurate detection and blocking of malicious activities.
Application-Level Protection
Drawing from the expertise of WAFs, NGFWs extend their protective umbrella to the application layer, safeguarding web applications from targeted attacks like SQL injection and cross-site scripting (XSS). This specialization empowers organizations to secure their web-facing applications, ensuring the integrity and availability of services and data.
Unified Security Approach
The amalgamation of diverse security features within NGFWs facilitates a unified approach to cybersecurity. Organizations can leverage the comprehensive protection offered by NGFWs to secure their networks and applications against a broad spectrum of threats, from common network attacks to advanced application vulnerabilities.
Next-Generation Firewalls emerge as the harmonious blend of the best features of Web Application Firewalls and traditional firewalls, providing a multifaceted security solution. Their ability to offer both network and application-level protection makes them an indispensable asset for organizations aiming for a resilient and comprehensive security posture in today’s dynamic and evolving cyber threat landscape.
By embracing the integrated security model of NGFWs, organizations can fortify their defenses across multiple layers of the network, ensuring the seamless and secure operation of their digital ecosystems. The convergence of specialized functionalities within NGFWs paves the way for a safer and more secure digital future.
Conclusion: Which Shields You Better?
Web Application Firewalls (WAFs) and traditional firewalls emerge as the twin sentinels. Each type of firewall wielding distinct protective mechanisms. WAFs, with their focus on the application layer, shield web applications from a myriad of sophisticated attacks like SQL injection and cross-site scripting (XSS). In doing so, WAFs ensure the sanctity of application-specific data and functionalities. Conversely, traditional firewalls serve as the guardians of the network layer. They do this by filtering and monitoring network traffic to prevent unauthorized access and intrusions.
While each firewall type excels in its domain, their synergistic implementation fortifies the security landscape, providing a layered defense against the multifaceted threats lurking in the digital shadows. The integration of these firewalls in the form of Next-Generation Firewalls (NGFWs) epitomizes the evolution of cybersecurity, offering a unified security solution that amalgamates the specialized protections of both firewall types.
The digital realm, with its boundless opportunities, is also fraught with ever-evolving cyber threats. The convergence of WAFs and traditional firewalls not only enhances the resilience of our digital ecosystems but also empowers organizations to navigate the cyber seas with confidence and assurance. The pursuit of knowledge in cybersecurity is a journey, not a destination, and it is imperative for individuals and organizations to continually explore, learn, and adapt to the shifting cyber terrains.
What’s Next??
Embark on your cybersecurity odyssey! Delve deeper into the realms of network and application security, and arm yourself with the knowledge to safeguard your digital domains. We encourage you to explore more about the intricate workings of firewalls. Engage in enlightening discussions. Share your insights and experiences. Let’s foster a community of cyber guardians. Let’s be united in our quest to secure the digital world and protect the invaluable treasures of information and privacy it holds. Join the conversation, share your thoughts, and let’s build a safer, more secure cyber future together!
The post Web Application Firewall vs Firewall: What You Need to Know appeared first on Endpoint Security.
*** This is a Security Bloggers Network syndicated blog from Endpoint Security authored by Michael Toback. Read the original post at: https://smallbizepp.com/web-application-firewall-vs-firewall/?utm_source=rss&utm_medium=rss&utm_campaign=web-application-firewall-vs-firewall
Original Post URL: https://securityboulevard.com/2023/09/web-application-firewall-vs-firewall-what-you-need-to-know/
Category & Tags: Endpoint,Security Bloggers Network,Endpoint security – Endpoint,Security Bloggers Network,Endpoint security
Views: 0





















































