Source: securityboulevard.com – Author: Michael Vizard
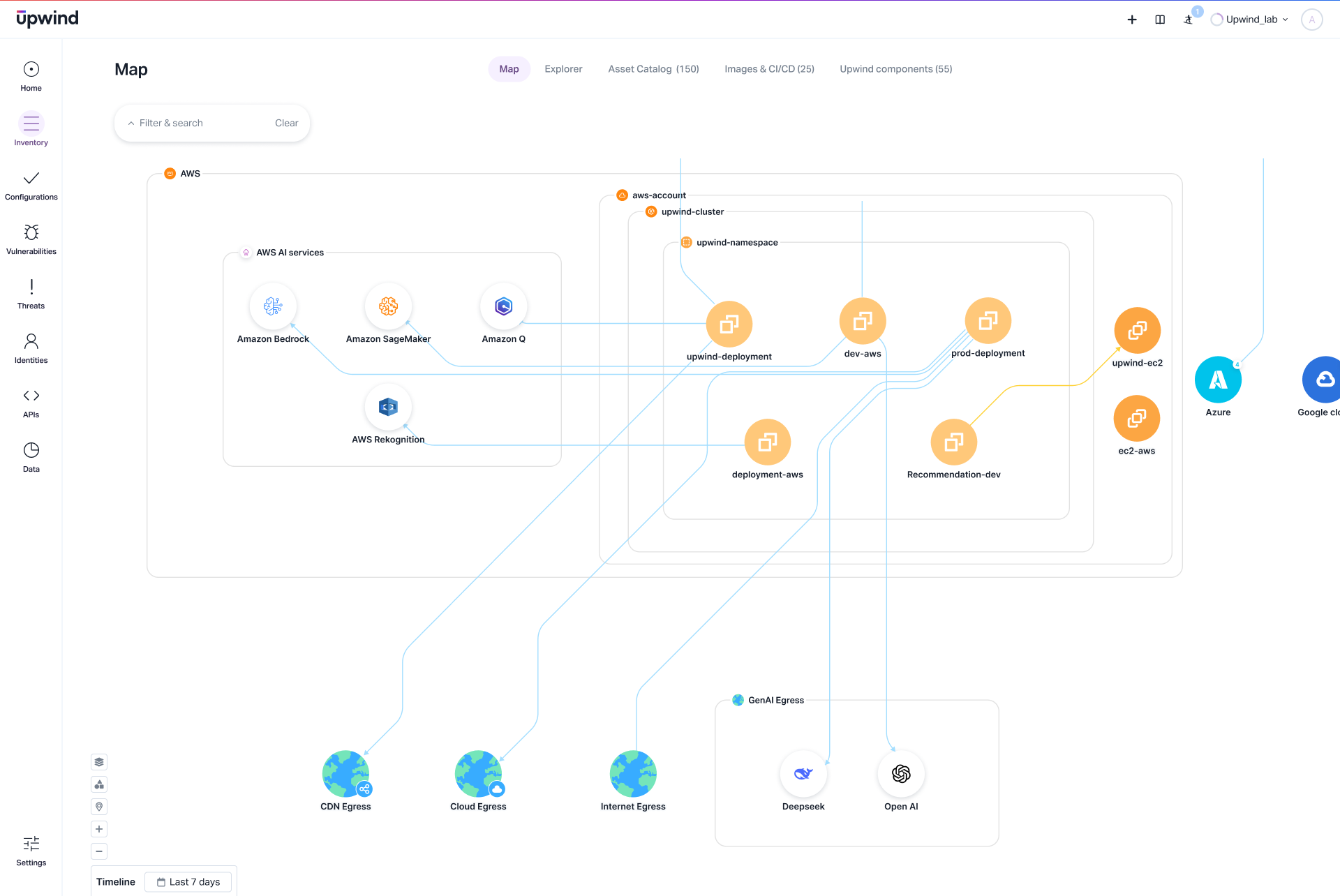
Upwind has added an ability to detect threats to application programming interfaces (APIs) in real time to its cloud application detection and response (CADR) platform, based on machine learning algorithms.
Company CEO Amiram Shachar said that by employing an extended Berkeley Packet Filtering (eBPF) that is available in the latest versions of Linux, it is now possible to collect telemetry data from Layers 3, 4, and 7 of the networking stack. Machine learning algorithms can then be applied to identify deviations and other anomalous behavior in API traffic that can now be continuously monitored, he added.
Additionally, machine learning algorithms can also be used to enable organizations to establish API traffic baselines. Those baselines can be used to enable cybersecurity teams to tailor policies to specific use cases involving API traffic, noted Shachar.
The overall goal is to reduce the amount of time required to investigate API security incidents by as much as a factor of 10, while reducing mean time to response (MTTR) times by as much as a factor of seven, he added.
In general, there is now a lot more focus on API security in the age of generative artificial intelligence (AI), said Shachar. Most AI services are invoked using APIs, a cybersecurity issue that many organizations are now discovering as they look to ensure that sensitive data isn’t being shared inadvertently with an AI model.
Historically, responsibility for securing APIs has often been unclear. Many cybersecurity teams assume that application development teams are securing APIs as they are developed. Unfortunately, many application developers assume cybersecurity teams are securing APIs. The end result can be thousands of APIs that cybercriminals can invoke to exfiltrate data or, worse yet, modify business logic.
More challenging still, application developers may create rogue APIs that no one on the cybersecurity team knows exist. Additionally, it’s not uncommon for there to be zombie APIs that have been abandoned by application development teams that might still be externally accessible.
On the plus side, there is now a greater emphasis being placed on securing software supply chains. A Futrum Research survey finds over the next 12-18 months, organizations specifically plan to increase software security spend on application programming interfaces (42%), DevOps toolchains (35%) incident response (34%) open source software (32%), software bill of materials (30%) and software composition analysis (27%) tools.
Hopefully, ongoing advancements in AI coupled with technologies such as eBPF will make it simpler to secure the entire software development lifecycle, including the building and deployment of APIs, by streamlining the collection and analysis of telemetry data.
In the meantime, cybersecurity teams would be well-advised to at the very least create an inventory of the APIs their own organization invokes. Most of these APIs will be for some internal purpose that can’t be easily accessed. However, external-facing APIs have become a rich target for cybercriminals and security teams need to ensure that best cybersecurity practices are being applied and maintained. Otherwise, it’s only a matter of time before cybersecurity teams discover those APIs have been abused for months, sometimes even years, without anyone ever being the wiser.
Recent Articles By Author
Original Post URL: https://securityboulevard.com/2025/04/upwind-adds-ability-to-detect-api-threats-to-cloud-security-platform/?utm_source=rss&utm_medium=rss&utm_campaign=upwind-adds-ability-to-detect-api-threats-to-cloud-security-platform
Category & Tags: AI and Machine Learning in Security,Cybersecurity,Featured,News,Security Boulevard (Original),Social – Facebook,Social – LinkedIn,Social – X,Spotlight,APIs,cybercriminals,ML – AI and Machine Learning in Security,Cybersecurity,Featured,News,Security Boulevard (Original),Social – Facebook,Social – LinkedIn,Social – X,Spotlight,APIs,cybercriminals,ML
Views: 2