Source: securityboulevard.com – Author: Michael Toback
Introduction
The convergence of the Internet of Things (IoT) and endpoint security has become a pivotal focal point for small businesses. These businesses are striving to safeguard their digital landscapes. The integration of IoT has revolutionized operational processes. By doing so, they offer unprecedented opportunities for innovation and growth. However, it has also introduced a myriad of security challenges that necessitate robust protective measures.
Take, for instance, a hypothetical local bakery, “Sweet Delights,” that embraced IoT to streamline its operations. The bakery has integrated smart refrigeration units and ovens connected to the internet. By doing so, the bakery aimed to optimize energy consumption and monitor baking processes remotely. However, the incorporation of these interconnected devices inadvertently expanded the bakery’s digital footprint, creating numerous entry points susceptible to cyber-attacks. One day, an unsuspecting click on a seemingly harmless email link led to a security breach. This allowed hackers to manipulate the bakery’s smart devices, disrupting operations and causing substantial financial loss.
This scenario underscores the criticality of IoT endpoint security. It highlights the dire need for small businesses to fortify their defenses against the ever-growing cyber threats. These threats are lurking in the shadows of technological advancements. It is imperative for small business managers to delve deeper into understanding the tapestry of IoT and endpoint security. They need to do this in order to protect their enterprises from the vulnerabilities and risks inherent in IoT devices. By doing so, they can harness the full potential of IoT innovations while maintaining a secure and resilient business environment.
Interested in a foundational understanding of IoT and endpoint security? our guides on A Comprehensive Guide to IoT and The Importance of Endpoint Security offer in-depth insights into these domains. These guides can serve as valuable resources in navigating the complexities of the digital world.
The Evolution of IoT: A Quick Recap
The journey of the Internet of Things (IoT) is a fascinating tale of innovation and integration. IoT transforms the way businesses operate and interact with the world. The detailed evolution of IoT is meticulously illustrated in our Guide to IoT. Still, it’s crucial to grasp the essence of its progression to comprehend the significance of IoT endpoint security fully.
IoT has evolved from a concept of interconnected objects to a fundamental business tool. This enables real-time data collection, analysis, and automation. It has permeated various industries, from healthcare to manufacturing, creating a seamless blend of the physical and digital worlds. The integration of IoT devices into business operations has unlocked new possibilities. However, it has also necessitated a reevaluation of security protocols to safeguard against the unique vulnerabilities they introduce.
You might want to delve deeper into the evolution of IoT and explore the milestones that have shaped its journey. We encourage you to refer to the comprehensive timeline provided in our Guide to IoT. This resource will equip you with a richer understanding of the transformative impact of IoT. It will also give you the foundational knowledge required to navigate the complexities of IoT endpoint security.
In the subsequent sections, we will explore the critical aspects of IoT endpoint security. We will be shedding light on the vulnerabilities, best practices, and advanced solutions. These ideas are pivotal for small businesses in this interconnected era.
Why IoT Endpoint Security is Crucial for Small Businesses
The integration of IoT devices within business operations has opened up a realm of possibilities. These IoT devices offer enhanced efficiency, automation, and data insights. However, the convergence of IoT and endpoint security is not merely an additive combination of their individual components. It is also a complex interplay that demands meticulous attention and specialized protective measures.
Our articles on Endpoint Security and IoT Security Risks delve into the respective intricacies of these domains. Still, it’s imperative to understand that the intersection of these technologies creates a unique set of vulnerabilities and challenges. The interconnected nature of IoT devices expands the attack surface. Thus, exposing businesses to a diverse array of cyber threats. These threats range from data breaches to ransomware attacks. Each of these threats are capable of inflicting severe damage to business operations and reputations.
Example Scenario for IoT Endpoint Security
Consider the scenario of a small healthcare clinic utilizing IoT-enabled medical devices to monitor patient health. A seemingly minor vulnerability in one of the devices could serve as a gateway for cybercriminals. This is a gateway to access sensitive patient data and infiltrate the clinic’s entire network. Thus, jeopardizing patient privacy and the clinic’s credibility.
This example underscores the criticality of implementing robust IoT endpoint security measures to shield small businesses from the multifaceted risks lurking in the digital shadows. It is not merely about protecting individual devices or the perimeters of the network security. It is also about constructing a resilient defense mechanism that can adapt to the evolving threat landscape. In doing so, it can safeguard the integrity of business ecosystems.
In this interconnected era, the boundaries between the digital and physical worlds are blurring. The significance of IoT endpoint security for small businesses cannot be overstated. It is a pivotal component in fostering a secure and conducive environment. In doing so, it enables businesses to leverage the transformative potential of IoT while mitigating the associated security risks.
In the following sections, we will delve deeper into the common threats and vulnerabilities inherent to IoT devices. Further, we will explore the proactive measures and advanced solutions that can fortify small businesses against the escalating wave of cyber threats in this digital age.
Common Threats and Vulnerabilities in IoT Devices
The fusion of IoT and endpoint security brings forth a spectrum of threats and vulnerabilities. Each threat with the potential to compromise the sanctity of business networks and data. Our articles on OWASP IoT Top 10 Vulnerabilities and IoT Security Risks provide extensive insights into the myriad of risks associated with IoT devices. Still, it’s crucial to understand the amplified implications at their intersection with endpoint protection.
IoT devices, with their inherent vulnerabilities such as insecure firmware and weak credentials, act as potential entry points for cybercriminals. THese entry points allow them to infiltrate business networks and exploit endpoint vulnerabilities. For instance, a compromised IoT device can serve as a conduit for attackers to access and manipulate other connected devices within the network. Thus, leading to data breaches, operational disruptions, and loss of intellectual property.
Consider referring to our detailed infographic which illustrates the common threats and vulnerabilities in IoT devices. So, offering a visual guide to understanding the diverse risks that businesses need to mitigate.
For small businesses, the repercussions of such security breaches can be devastating, resulting in financial losses, reputational damage, and loss of customer trust. It underscores the imperative need for small businesses to be vigilant and proactive in securing both IoT devices and endpoints, implementing robust security protocols to thwart the multifaceted threats lurking in the interconnected digital landscape.
In the ensuing sections, we will explore the best practices and advanced solutions that can empower small businesses to fortify their defenses, ensuring the secure integration of IoT devices within their operational ecosystems.
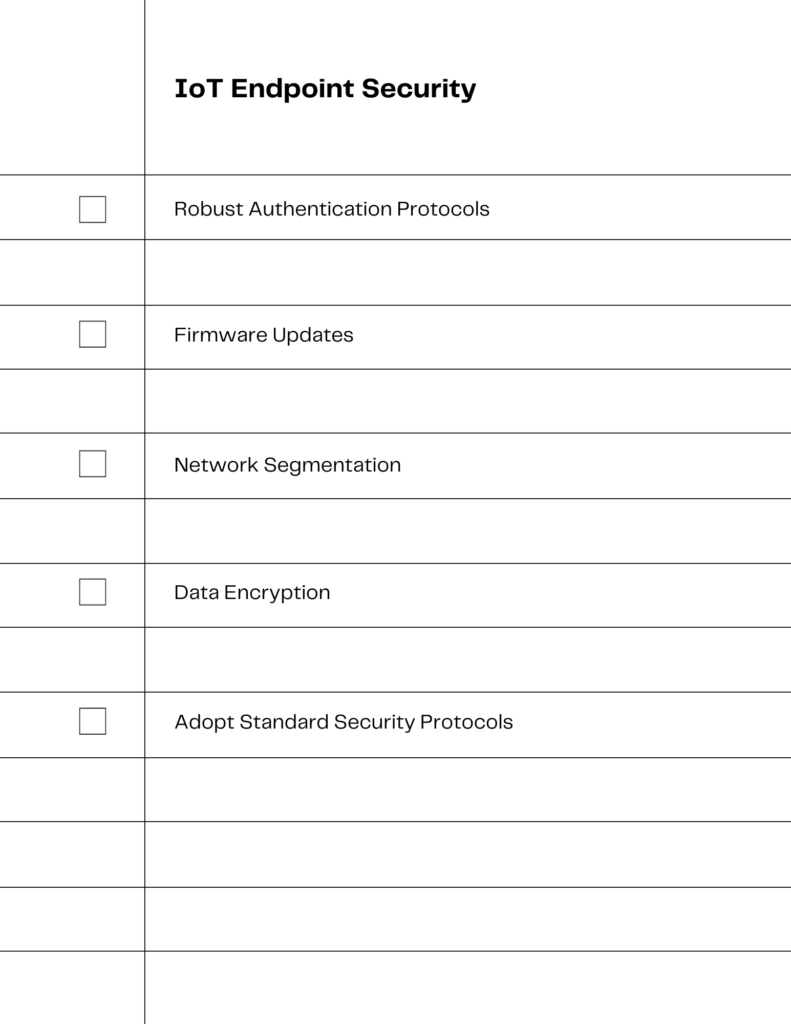
Security Best Practices: Enhancing IoT Endpoint Security
Securing the interconnected realm of IoT devices and endpoints necessitates a holistic approach, one that amalgamates the best practices from both domains to construct a resilient defense mechanism. While our articles on Best Practices for IoT Security and Unlocking Endpoint Security offer in-depth guidance on securing each domain, the intersection of IoT and endpoint security demands specialized attention and tailored strategies.
Here are some best practices to enhance IoT endpoint security:
- Unified Security Protocols: Develop cohesive security protocols that encompass both IoT devices and endpoints, ensuring seamless integration and mutual reinforcement.
- Enhanced Authentication: Implement multi-factor authentication and robust credential management to secure access to IoT devices and associated endpoints.
- Regular Security Audits: Conduct periodic assessments of IoT devices and endpoints to identify and address vulnerabilities proactively.
- Data Encryption: Employ advanced encryption techniques to protect the data transmitted between IoT devices and endpoints, safeguarding against unauthorized access and breaches.
- Network Segmentation: Isolate IoT devices within dedicated network segments to contain potential security issues or breaches and prevent lateral movement of threats within the network.
We encourage you to delve deeper into the aforementioned articles for a comprehensive understanding of the best practices in each domain and to integrate these insights to fortify your IoT endpoint security framework.
This visual representation can serve as a quick reference guide, aiding small businesses in implementing a synergistic approach to secure the convergence of IoT and endpoint security effectively.
In the following sections, we will explore advanced solutions and technologies that can further enhance the security posture of small businesses in this interconnected digital era.
Next-Gen Solutions: The Future of IoT Endpoint Security

In the ever-evolving realm of technology, the future of IoT endpoint security is shaping up to be revolutionary. Advanced and emerging solutions are paving the way. These next-gen solutions are not mere upgrades. The solutions are transformative approaches. Next-Gen solutions are leveraging cutting-edge technologies such as machine learning and artificial intelligence to redefine the paradigms of security.
Machine learning is a subset of artificial intelligence. It empowers security solutions to learn and adapt. Machine Learning identifies patterns and anomalies that could signify potential threats. This adaptability is crucial in managing the dynamic landscape of modern threats. Doing so allows for proactive and predictive security measures, a significant leap from the reactive models of the past.
Next-gen endpoint security solutions are designed to be more comprehensive and intelligent. They offer a holistic approach, providing visibility, control, and protection across all endpoints, including the myriad of IoT devices integrated into business operations. These solutions are equipped with advanced threat intelligence, enabling them to detect, analyze, and respond to threats more efficiently and effectively.
Consider Adopting NGFW Technologies
For small businesses, the adoption of these advanced solutions is not just about mitigating risks; it’s about enabling growth and innovation. Small businesses can benefit immensely from the enhanced security posture provided by next-gen solutions, allowing them to leverage IoT technologies with confidence. These solutions facilitate the secure integration of IoT devices, ensuring the integrity and confidentiality of business data and operations.
By managing modern threats more effectively, small businesses can focus on their core objectives, driving productivity and competitiveness in the market. The enhanced security also fosters a sense of trust among customers and partners, a valuable asset in building and maintaining business relationships.
The future of IoT endpoint security is promising, with next-gen solutions offering advanced and intelligent protection against modern threats. Small businesses stand to gain significantly from embracing these solutions, securing their journey in the digital age while unlocking the full potential of IoT innovations.
How to Choose the Right IoT Endpoint Security Solution
Selecting the right IoT endpoint security solution is a pivotal decision that requires careful consideration of various factors. It’s not just about choosing the most advanced solution; it’s about finding the one that aligns best with your business needs and IT capabilities.
When evaluating different solutions, consider the following key factors:
- Scalability: Can the solution adapt to the growing number of IoT devices in your network?
- User-friendliness: Is the solution easy to use and manage, especially for those with limited cybersecurity expertise?
- Support: Does the provider offer reliable and timely support to assist you in addressing any issues or concerns?
Here’s a comparison chart of five IoT endpoint security solutions, focusing on features specific to IoT devices, to aid in your selection process:
| Solution | Features Specific to IoT Devices | Suitability |
|---|---|---|
| Symantec Endpoint Security | – IoT Device Discovery – IoT Risk Assessment – IoT Threat Defense |
Suitable for businesses looking for comprehensive IoT device visibility and advanced threat protection. |
| McAfee Endpoint Security | – IoT Device Protection – Machine Learning Analysis for IoT – Integrated Firewall for IoT Devices |
Ideal for businesses requiring robust IoT protection with integrated firewall and machine learning analysis. |
| Trend Micro IoT Security | – IoT Device Reputation – Vulnerability Shielding for IoT – Custom Defense for IoT |
Best suited for businesses seeking custom defense and vulnerability shielding for IoT devices. |
| Kaspersky Endpoint Security | – IoT Threat Prevention – Adaptive Anomaly Control for IoT – Exploit Prevention for IoT Devices |
Suitable for businesses looking for adaptive control and exploit prevention for IoT devices. |
| Bitdefender GravityZone | – Risk Management for IoT – IoT Anomaly Detection – Network Attack Defense for IoT |
Ideal for enterprises needing advanced risk management and network attack defense for IoT devices. |
By considering these factors and evaluating the specific features and suitability of each solution, you can make an informed decision that will empower your small business to leverage the benefits of IoT technologies securely and efficiently. Keep in mind the importance of choosing a solution that is not only advanced but also aligns well with your individual business needs and IT capabilities.
Conclusion
In the intricate tapestry of today’s digital landscape, the significance of IoT endpoint security cannot be overstated. As we delve deeper into the era of connectivity, where the Internet of Things (IoT) becomes increasingly ingrained in our daily business operations, the need for robust security measures becomes paramount. Small businesses, with their unique challenges and opportunities, find themselves at the crossroads. They are navigating the potentials and pitfalls of IoT innovations.
The convergence of IoT and endpoint security is a journey of continuous learning and adaptation. It’s about striking the right balance between innovation and protection. This ensures that the myriad of connected devices operate cohesively and securely within the business ecosystem. For small businesses, this balance is crucial. It enables them to harness the transformative power of IoT while safeguarding their assets, data, and reputation.
The journey towards a secure and resilient IoT environment is laden with choices. The selection of suitable IoT endpoint security solutions is a pivotal step, requiring a thoughtful consideration of business needs, IT capabilities, and the evolving threat landscape. It’s about making informed decisions, choosing solutions that align with business objectives, and fostering a culture of security and vigilance.
In conclusion, as we stand on the brink of a new digital frontier, let’s embrace the future with knowledge, vigilance, and a proactive approach to IoT endpoint security. Let’s empower our small businesses to thrive in this connected world, unlocking the full potential of IoT innovations while maintaining a steadfast guard against the shadows of cyber threats.
So, let’s stay informed, stay proactive, and secure our digital future. Let’s make IoT endpoint security a priority, building a safer, smarter, and more connected world for us all. Keep learning, keep questioning, and keep securing your business in this ever-evolving digital age.
Additional Resources
We have additional resources for you to explore on these to interconnected subjects:
- OWASP Top 10 IoT Vulnerabilities
- Guide to IoT
- IoT Security Risks
- IoT Security Best Practices
- Host Endpoint Security
The post Unlocking IoT Endpoint Security in 2023: What You Need to Know appeared first on Endpoint Security.
*** This is a Security Bloggers Network syndicated blog from Endpoint Security authored by Michael Toback. Read the original post at: https://smallbizepp.com/iot-endpoint-security/?utm_source=rss&utm_medium=rss&utm_campaign=iot-endpoint-security
Original Post URL: https://securityboulevard.com/2023/09/unlocking-iot-endpoint-security-in-2023-what-you-need-to-know/
Category & Tags: Endpoint,IoT & ICS Security,Security Bloggers Network,Endpoint security,iot – Endpoint,IoT & ICS Security,Security Bloggers Network,Endpoint security,iot
Views: 0