Source: heimdalsecurity.com – Author: Livia Gyongyoși
Researchers revealed that the UNC3944 threat actors use phishing and SIM-swapping attacks to get control over Microsoft Azure admin accounts. Hackers maliciously used the Azure Serial Console on Azure Virtual Machines (VM) to deploy remote management software within client environments.
The method succeeded to avoid the usual detection methods that Azure uses and enabled threat actors with admin access to the VM.
According to researchers, UNC3944 aims to steal data from target companies by using Microsoft’s cloud computing service. The threat group was first spotted in May 2022.
UNC3944 was previously attributed to creating the STONESTOP (loader) and POORTRY (kernel-mode driver) toolkit to terminate security software.
The threat actors utilized stolen Microsoft hardware developer accounts to sign their kernel drivers.
Gaining Access Method Explained
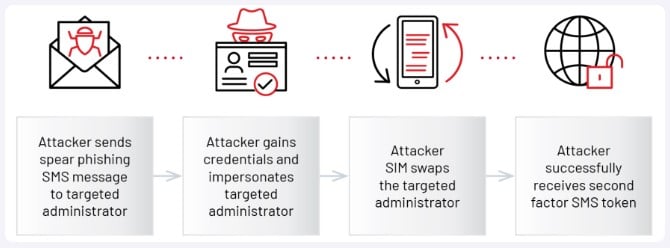
Hackers rely on SMS phishing to get credentials that will allow access to the Azure administrator’s account. Then they contact help desk agents and convince them to send a multi-factor reset code via SMS to the victim`s mobile.
Before doing that, threat actors SIM-swap the victim’s number and port it to their device. While the 2FA token will get to them, the real admin will not be able to suspect anything.
The method threat actors use for SIM swapping is yet unknown. However, knowing a victim`s phone number and collaborating with malicious telecom employees makes illicit number ports possible.
After they obtain a foothold in the target’s Azure environment, hackers can use their admin privileges to:
- Collect data about the users.
- Get information about the Azure environment configuration and VMs.
- Modify or create new accounts.
Researchers claim UNC3944 also uses Azure Extensions to disguise their malicious activities as day-to-day tasks that mock inoffensive activity.
How They Use Breached VMs to Steal Data
The next step for UNC3944 threat actors is to use Azure Serial Console to gain administrative console access to VMs. Then they execute commands on a command prompt over the serial port.
According to researchers, the first command they run is ”whoami”. Thus, they identify currently logged-in users and collect the data they need to move further.
After that, hackers use PowerShell to obtain persistence on the VM and deploy remote administrator tools. These tools are legitimately signed software that usually doesn`t trigger alerts in endpoint detection platforms. So, they`ll go through unnoticed.
UNC3944`s next move is to establish a connection to their C2 server, employing a reverse SSH tunnel. That ensures them persistent access, network restrictions, and security controls evading.
According to BleepingComputer:
The attacker configures the reverse tunnel with port forwarding, facilitating a direct connection to Azure VM via Remote Desktop. For example, any inbound connection to remote machine port 12345 would be forwarded to the local host port 3389 (Remote Desktop Protocol Service Port).
At last, threat actors use the credentials of a compromised account to get into the compromised Azure VM via the reverse shell. That`s when they safely begin to expand control over the compromised environment.
Two of the security measures that could help mitigate this kind of activity are proper cloud privilege access management measures and DNS filtering that can block malicious communication with C2s.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.
If you liked this post, you will enjoy our newsletter.
Get cybersecurity updates you’ll actually want to read directly in your inbox.
Original Post URL: https://heimdalsecurity.com/blog/unc3944-microsoft-azure-access-to-virtual-machines/
Category & Tags: Cybersecurity News – Cybersecurity News
Views: 17




















































