Source: securityboulevard.com – Author: mykola myroniuk
When we think about HIPAA compliance and websites, the focus often shifts to patient portals, online scheduling systems, and other secure areas requiring user authentication. However, it’s crucial to recognize that even unauthenticated webpages, those accessible to the public without logging in, can present hidden HIPAA risks. Let’s explore these often-overlooked vulnerabilities and discuss how covered entities can mitigate potential compliance pitfalls.

Understanding the Risks of Unauthenticated Webpages
Unauthenticated webpages typically house general information about a healthcare provider or organization, such as contact details, service descriptions, and blog posts. While these pages may not seem to handle sensitive patient data directly, seemingly innocuous elements like contact forms, appointment request features, and online symptom checkers can inadvertently capture PHI.
For example, an individual might provide their email address and reason for seeking an appointment through an online form, unknowingly disclosing PHI to the website operator. Additionally, tracking technologies like cookies and web beacons can capture a user’s IP address, browsing history on the site, and other data points that might be considered PHI when combined with health-related information.
HIPAA Considerations for Unauthenticated Webpages
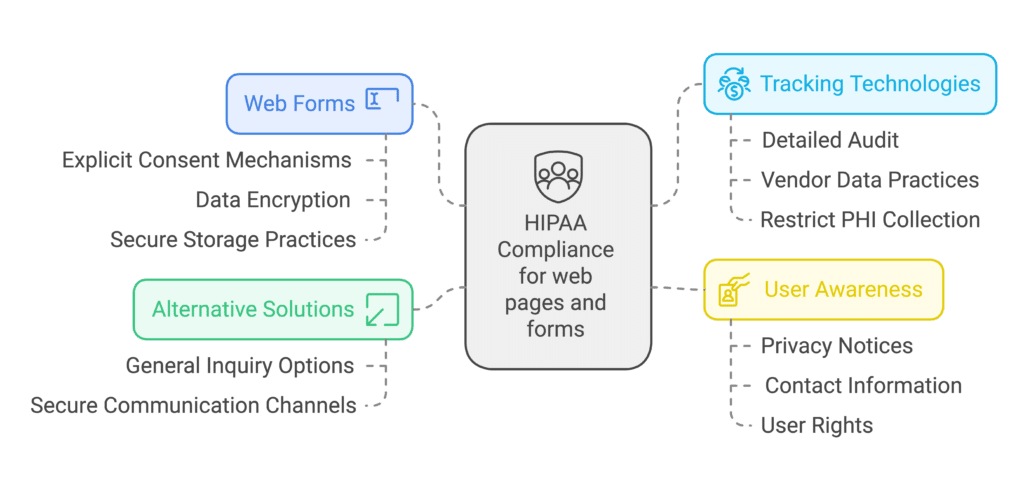
- Scrutinize Web Forms: Carefully evaluate all web forms on your unauthenticated pages, assessing the types of information collected. If a form captures PHI, ensure appropriate safeguards are in place, such as explicit consent mechanisms, data encryption, and secure storage practices.
- Evaluate Tracking Technologies: Thoroughly review the tracking technologies deployed on your unauthenticated webpages, particularly those from third-party vendors. Determine if these technologies collect any information that could be considered PHI, and if so, ensure compliance with HIPAA’s authorization and disclosure requirements.
- Consider Alternative Solutions: Explore alternative solutions that minimize the collection of PHI on unauthenticated webpages. For instance, instead of capturing detailed health information through contact forms, consider providing a general inquiry option or directing visitors to secure channels for sensitive communication.
- Enhance User Awareness: While not a substitute for compliance, providing clear and concise privacy notices on your website can help users understand how their information is collected, used, and protected. Clearly articulate your organization’s commitment to HIPAA compliance and provide readily accessible contact information for privacy-related inquiries.
Don’t Underestimate the Importance of Protecting PHI
Even seemingly harmless data points, when linked to an individual’s health or healthcare, can constitute PHI. Covered entities must exercise caution and adopt a proactive approach to ensure HIPAA compliance extends to all aspects of their online presence, including public-facing web pages.
HIPAA compliance is not merely a checkbox exercise but an ongoing commitment to safeguarding sensitive health information that requires rigor and consistency. By implementing robust safeguards and fostering a culture of privacy, healthcare organizations can harness the power of websites while upholding their legal and ethical obligations to protect patient data.
The post Unauthenticated Webpages: Hidden HIPAA Risks on Public-Facing Websites appeared first on Feroot Security.
*** This is a Security Bloggers Network syndicated blog from Feroot Security authored by mykola myroniuk. Read the original post at: https://www.feroot.com/blog/unauthenticated-webpages-hidden-hipaa-risks-on-public-facing-websites/
Original Post URL: https://securityboulevard.com/2024/12/unauthenticated-webpages-hidden-hipaa-risks-on-public-facing-websites/
Category & Tags: Security Bloggers Network,Blog – Security Bloggers Network,Blog
Views: 2



















































