Source: securityboulevard.com – Author: Devesh Patel
If you’ve worked with SCIM for any length of time, you’ve definitely been in this situation. SCIM troubleshooting can feel like detective work – you’re piecing together clues from error logs, identity provider configurations, and network traces to figure out why users who should exist don’t exist, or why they exist but with the wrong permissions.
Let me walk you through a systematic approach to SCIM troubleshooting that’ll help you identify and fix provisioning issues quickly. We’ll start with the most common problems and build up to the trickier edge cases that can really stump you.
Understanding the SCIM Provisioning Journey
Before we dive into specific problems, let’s make sure we understand what needs to happen for user provisioning to work correctly. Think of SCIM provisioning like a relay race – there are multiple handoffs, and if any runner drops the baton, the whole process fails.
The journey starts in the identity provider when someone assigns a user to your application or adds them to a group that has access. The identity provider needs to recognize that this change should trigger a provisioning event. Then it needs to construct a proper SCIM request with all the required user information. This request travels across the network to your SCIM endpoint, which needs to authenticate the request, validate the data, and actually create or update the user in your system.
Each step in this journey can fail in different ways, and the symptoms you see often don’t point directly to the root cause. A user who “isn’t provisioning” might actually be getting created successfully, but with the wrong permissions, so they can’t access anything meaningful in your application.
This is why good SCIM troubleshooting starts with understanding the entire flow and then systematically checking each piece. Let’s build that understanding step by step.
The Most Common Culprit: Configuration Mismatches
In my experience helping teams debug SCIM issues, configuration problems cause about 60% of all provisioning failures. These aren’t dramatic failures with obvious error messages – they’re subtle mismatches that cause requests to fail in confusing ways.
Let’s start with the most common configuration issue: endpoint URL problems. This sounds simple, but you’d be surprised how often the wrong URL is the culprit. Maybe the identity provider is configured to send requests to https://yourapp.com/scim/v2/Users but your endpoint actually expects https://yourapp.com/scim/v2/users (notice the lowercase ‘users’). Or maybe there’s a trailing slash issue, or the identity provider is using HTTP instead of HTTPS.
Here’s how to check this systematically. First, look at your server logs to see if you’re receiving ANY requests from the identity provider. If you see no requests at all, the problem is likely with the endpoint URL configuration. If you see requests but they’re hitting the wrong path, that’s still a URL configuration issue, just a different flavor.
Another sneaky configuration problem is authentication credential mismatches. The identity provider might be using an old API token, or maybe the token was regenerated but the identity provider wasn’t updated with the new value. Sometimes the token is correct but it’s not being sent in the right format – maybe your endpoint expects Bearer token123 but the identity provider is sending just token123.
To debug authentication issues, look for 401 Unauthorized responses in your logs. But here’s where it gets tricky – some identity providers don’t handle 401 responses gracefully. They might retry a few times and then just give up silently, so you need to check your server logs rather than relying on the identity provider to report the authentication failure.
Decoding SCIM Error Codes Like a Pro
SCIM uses standard HTTP status codes, but understanding what each code means in the context of user provisioning requires some interpretation. Let me walk you through the most common codes you’ll encounter and what they actually tell you about the underlying problem.
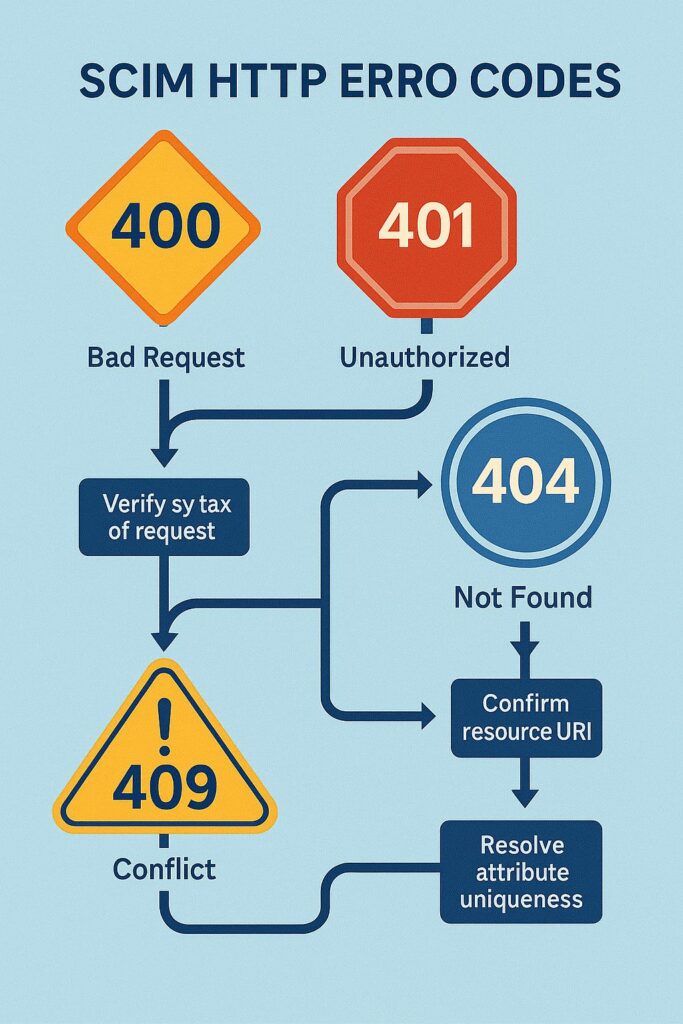
A 400 Bad Request is probably the most common error code you’ll see, but it’s also the least helpful by itself. A 400 just means “something about this request is wrong,” but it doesn’t tell you what. The real information is in the response body, which should contain a more detailed error message.
Here’s what a good 400 error response looks like:
{ "schemas": ["urn:ietf:params:scim:api:messages:2.0:Error"], "status": "400", "detail": "Required attribute 'userName' is missing", "scimType": "invalidValue" } When you see a 400 error, your first step should be to examine the request that caused it. Look at the JSON payload – is it valid JSON? Are all the required fields present? Do the field values match what your endpoint expects?
A common cause of 400 errors is schema mismatches. Maybe the identity provider is sending a userName field but your endpoint expects username (different capitalization). Or maybe they’re sending a phone number as a string but your endpoint expects a structured object with country code and number separated.
The 404 Not Found error is usually easier to diagnose. In SCIM context, this typically means one of two things: either the endpoint path is wrong (which we covered in the configuration section), or the identity provider is trying to update or delete a user that doesn’t exist in your system.
The second case is actually pretty common and usually indicates a synchronization problem. Maybe the user was created outside of SCIM (directly in your application), so when the identity provider tries to update them via SCIM, your endpoint can’t find them. Or maybe the user was deleted in your system but the identity provider still thinks they exist.
Here’s a debugging tip for 404 errors: check whether the identity provider is using the correct user identifier. SCIM uses the id field as the primary identifier for update and delete operations, but different systems sometimes generate IDs differently. If your endpoint uses email addresses as IDs but the identity provider is sending database record IDs, you’ll get 404 errors even though the user exists.
The Sneaky 409 Conflict Scenarios
The 409 Conflict error is one that trips up a lot of developers because it often indicates more complex business logic problems rather than simple configuration issues. A 409 means “I understand your request, but I can’t fulfill it because it conflicts with the current state of the system.”
The most common 409 scenario is duplicate users. Maybe the identity provider is trying to create a user with an email address that already exists in your system. This can happen if someone signed up for your application directly before SCIM provisioning was set up, or if there are multiple identity providers trying to manage the same user.
But here’s where 409 errors get tricky – the “conflict” might not be obvious. Maybe the identity provider is trying to create a user with a username that’s already taken, even though the email addresses are different. Or maybe there’s a business rule in your application that prevents creating users with certain attributes, and the SCIM request violates that rule.
When you encounter 409 errors, you need to think about your application’s uniqueness constraints and business rules. What fields need to be unique? What validation rules might prevent user creation? Are there any dependencies between fields that might cause conflicts?
Here’s a real-world example that stumped me for a while: an application had a business rule that users could only be assigned to projects that existed and had available capacity. The SCIM request was trying to create a user with a project assignment, but the project was full, so the request failed with a 409. The error message said “project assignment conflict” but it wasn’t obvious that this meant “project is full” rather than “user is already assigned to a different project.”
Authentication and Authorization Debugging
Authentication problems can be particularly frustrating because they often fail silently from the identity provider’s perspective. The identity provider sends a request, gets a 401 response, and might just… stop trying, without giving you any indication of what went wrong.
The first step in debugging authentication issues is to verify that requests are actually reaching your endpoint. If you’re not seeing any requests in your server logs, the problem might be network-related rather than authentication-related. Maybe there’s a firewall blocking the requests, or the identity provider is configured with the wrong endpoint URL.
If requests are reaching your endpoint but failing authentication, you need to examine exactly what authentication information is being sent. Look at the Authorization header in the request logs. Is the token present? Is it in the expected format? Is it the current, valid token?
Here’s a common gotcha: some identity providers cache authentication tokens and don’t handle token refresh gracefully. If you rotate your API tokens regularly (which you should for security), you might see authentication failures because the identity provider is still using an old, expired token. The solution is usually to update the token in the identity provider configuration and possibly restart the provisioning job.
Authorization failures are a different beast. These happen when the request is properly authenticated, but the authenticated party doesn’t have permission to perform the requested operation. Maybe the API token has read-only permissions but the identity provider is trying to create users. Or maybe the token is scoped to only manage certain types of users, and the request is trying to create a user outside that scope.
The key to debugging authorization issues is understanding your permission model. What permissions does the current API token have? What permissions are required for the operation being attempted? Are there any business logic restrictions that might prevent the operation even if the token has the right permissions?
Network and Timing Issues
Sometimes SCIM provisioning issues aren’t really SCIM issues at all – they’re network problems masquerading as application problems. These can be some of the trickiest to diagnose because the symptoms are often intermittent and hard to reproduce.
Network timeouts are a classic example. Maybe your SCIM endpoint is working correctly, but it’s slow, and the identity provider is timing out before the request completes. From the identity provider’s perspective, the request failed. From your perspective, the request succeeded (eventually). The result is that the identity provider thinks the user wasn’t created, but the user actually exists in your system.
To debug timeout issues, look at your response times in the server logs. How long are SCIM requests taking to complete? Are there any requests that take significantly longer than others? If you’re seeing timeouts, you might need to optimize your SCIM endpoint performance or work with the identity provider to increase their timeout settings.
SSL certificate problems are another common network issue. Maybe your SSL certificate expired, or there’s a problem with the certificate chain, and the identity provider can’t establish a secure connection to your endpoint. These issues often show up as connection failures rather than specific SCIM errors.
Rate limiting can also cause confusing symptoms. If your SCIM endpoint is rate-limiting requests from the identity provider, you might see some users getting provisioned successfully while others fail. The pattern often looks random from the identity provider’s perspective, but it actually corresponds to the rate limit thresholds you’ve configured.
Data Validation and Schema Issues
Data validation problems are some of the most common causes of SCIM provisioning failures, and they’re often the result of mismatches between what the identity provider sends and what your application expects.
Let’s walk through a systematic approach to debugging data validation issues. Start by examining the actual request payload that’s causing the failure. Is it valid JSON? Does it conform to the SCIM schema? Are all the required fields present?
Now look at the specific field values. Are they in the expected format? For example, if your endpoint expects phone numbers in E.164 format (+1234567890) but the identity provider is sending them in a different format (123-456-7890), the validation will fail.
Email address validation is a common source of problems. Different systems have different rules for what constitutes a valid email address. Maybe your endpoint is more strict than the identity provider expects, or maybe the identity provider is sending email addresses that are technically valid but don’t conform to your business rules.
Date and time fields are another frequent source of validation errors. Is the identity provider sending dates in the format your endpoint expects? Are timezone offsets handled correctly? If your endpoint expects UTC timestamps but the identity provider is sending local times, you’ll get validation errors.
Here’s a debugging technique that works well for data validation issues: create a test endpoint that logs the complete request payload without performing any validation. This lets you see exactly what data the identity provider is sending, which you can then compare against your validation rules to identify the mismatch.
Advanced Debugging Techniques
When the basic troubleshooting steps don’t reveal the problem, you need more advanced techniques to track down the issue. Let me share some approaches that have saved me hours of debugging time.
Request tracing is incredibly valuable for understanding complex provisioning flows. Set up logging that tracks each SCIM request from start to finish, including all the internal operations your endpoint performs. When a provisioning failure occurs, you can trace through the logs to see exactly where the process broke down.
Here’s what good request tracing looks like:
[2025-06-15 10:30:15] SCIM Request received: POST /scim/v2/Users [2025-06-15 10:30:15] Authentication successful for org: acme-corp [2025-06-15 10:30:15] Request validation started [2025-06-15 10:30:15] Schema validation passed [2025-06-15 10:30:15] Business rule validation started [2025-06-15 10:30:15] ERROR: User email already exists in system [2025-06-15 10:30:15] Returning 409 Conflict response This level of detail makes it easy to see that the request failed because of a duplicate email address, not because of authentication or schema validation issues.
Correlation IDs are another powerful debugging tool. Generate a unique ID for each SCIM request and include it in all log messages related to that request. This makes it easy to trace a single request through all your application’s systems, even if the request triggers multiple internal operations.
Differential debugging can help with intermittent issues. Set up parallel logging for successful and failed requests, then compare the patterns to identify what’s different about the failures. Maybe failed requests all come from a specific IP address, or they all include a particular field value that successful requests don’t have.
Building Better Error Messages
One of the best investments you can make in SCIM troubleshooting is building really good error messages. When something goes wrong, a clear, detailed error message can save hours of debugging time.
Good SCIM error messages include three key pieces of information: what went wrong, why it went wrong, and what can be done to fix it. Instead of returning a generic “Bad Request” error, return something like “Required field ‘userName’ is missing. Please ensure all user creation requests include a valid userName field.”
Here’s an example of how to structure helpful error responses:
{ "schemas": ["urn:ietf:params:scim:api:messages:2.0:Error"], "status": "400", "detail": "Email address 'invalid-email' is not in valid format. Expected format: [email protected]", "scimType": "invalidValue", "debugInfo": { "field": "emails[0].value", "providedValue": "invalid-email", "expectedFormat": "RFC 5322 compliant email address" } } The debugInfo section isn’t part of the standard SCIM error format, but including extra debugging information can be incredibly helpful for troubleshooting. Just make sure you don’t include sensitive information that could be logged or cached by intermediate systems.
Consider implementing different levels of error detail based on configuration settings. In development environments, you might want very verbose error messages with full stack traces. In production, you want helpful error messages without exposing internal system details that could be useful to attackers.
Monitoring and Alerting for Proactive Troubleshooting
The best SCIM troubleshooting is the kind you don’t have to do because you caught the problem before it affected users. Good monitoring and alerting can help you identify and fix issues before they escalate into customer-facing problems.
Set up alerts for error rate thresholds. If your SCIM endpoint typically has a 99% success rate, an alert when the success rate drops below 95% can give you early warning of problems. Different types of errors might warrant different alert thresholds – authentication failures might be more urgent than validation errors.
Monitor response time trends as well as error rates. A gradual increase in response times might indicate performance problems that could eventually lead to timeout failures. Catching these trends early lets you optimize performance before timeouts start occurring.
Track provisioning volumes and patterns. If you normally see 50 user creation requests per day but suddenly see 500, that might indicate a bulk provisioning operation that could overwhelm your system. Or if you see a sudden drop in provisioning volume, that might indicate a configuration problem with the identity provider.
Consider implementing health check endpoints that identity providers can use to verify that your SCIM service is functioning correctly. These endpoints can perform basic connectivity and authentication tests without affecting real user data.
Prevention Strategies
While good troubleshooting skills are essential, preventing problems in the first place is even better. Let me share some strategies that can help you avoid common SCIM provisioning issues.
Comprehensive testing is your first line of defense. Don’t just test the happy path where everything works perfectly – test error conditions, edge cases, and failure scenarios. What happens when the identity provider sends malformed data? How does your endpoint handle authentication failures? What if the database is temporarily unavailable?
Build idempotency into your SCIM operations. If the identity provider sends the same user creation request twice, your endpoint should handle it gracefully rather than failing with a duplicate user error. This prevents problems when identity providers retry failed requests.
Implement graceful degradation for non-critical operations. If your SCIM endpoint needs to perform multiple operations to fully provision a user (create the user account, assign permissions, send welcome email), consider making some of these operations optional. It’s better to create a user with basic permissions than to fail the entire provisioning operation because the welcome email couldn’t be sent.
Document your SCIM implementation thoroughly, including any custom extensions or business rules that might affect provisioning. When troubleshooting issues with enterprise customers, having clear documentation of how your SCIM endpoint behaves can save significant time.
Working with Enterprise Customers on SCIM Issues
When SCIM provisioning problems occur in production, you’re often working with enterprise customer IT teams to diagnose and resolve the issues. Having a good process for this collaboration can make the difference between a quick resolution and days of back-and-forth debugging.
Establish clear communication channels for SCIM issues. Make sure enterprise customers know how to report provisioning problems and what information you need to investigate effectively. A good SCIM issue report includes the timestamp of the failed operation, the user information that should have been provisioned, any error messages from the identity provider, and the identity provider configuration details.
Create diagnostic tools that customers can use to test their SCIM configuration. A simple endpoint that validates authentication and returns basic system status can help customers verify their setup independently. This reduces the number of support tickets caused by basic configuration errors.
When working with customers to resolve SCIM issues, be transparent about what you’re seeing in your logs while being careful not to expose sensitive information. Saying “I can see the request reaching our system, but it’s failing authentication” gives the customer useful information to check their configuration without revealing the actual authentication tokens or request details.
Consider providing customers with access to filtered logs for their organization’s SCIM activity. This transparency builds trust and enables customers to troubleshoot many issues independently.
The key to successful SCIM troubleshooting is systematic thinking and good tooling. When you understand the complete provisioning flow and have the right monitoring and debugging tools in place, most SCIM issues can be diagnosed and resolved quickly. The investment in building good error messages, logging, and monitoring infrastructure pays dividends every time you need to troubleshoot a problem.
Remember that SCIM issues often have cascading effects – a single configuration problem can cause multiple symptoms that seem unrelated. By starting with the basics (connectivity, authentication, configuration) and working systematically through the more complex possibilities (data validation, business rules, performance), you can efficiently narrow down the root cause and implement a fix.
*** This is a Security Bloggers Network syndicated blog from SSOJet authored by Devesh Patel. Read the original post at: https://ssojet.com/blog/troubleshooting-scim-provisioning-issues-your-complete-debug-guide/
Original Post URL: https://securityboulevard.com/2025/06/troubleshooting-scim-provisioning-issues-your-complete-debug-guide/?utm_source=rss&utm_medium=rss&utm_campaign=troubleshooting-scim-provisioning-issues-your-complete-debug-guide
Category & Tags: Identity & Access,Security Bloggers Network,Authentication,b2b,B2B SaaS,CIAM,enterprise security,Enterprise SSO,Identity & Access Management (IAM),SAML,SCIM,security,single sign on,sso – Identity & Access,Security Bloggers Network,Authentication,b2b,B2B SaaS,CIAM,enterprise security,Enterprise SSO,Identity & Access Management (IAM),SAML,SCIM,security,single sign on,sso
Views: 9






















































