Source: securityboulevard.com – Author: Veriti Research
As the new Snow White movie arrives in theaters with lackluster audience attendance (source), the absence of streaming options on platforms like Disney+ has nudged many users to seek pirated versions online.
From our perspective, this kind of consumer behavior isn’t new, every high-profile movie release without a digital option becomes an opportunity for attackers to exploit users eager to watch from home.
Veriti’s research team identified and analyzed a new malware campaign targeting users attempting to download the Snow White movie via torrent sites. What initially appears to be a “movie codec installer” is in fact a carefully orchestrated malware dropper, aimed at compromising user devices and distributing itself further through peer-to-peer networks.
Screenshot of poor theater attendance tweet
The Malicious Snow White Torrent
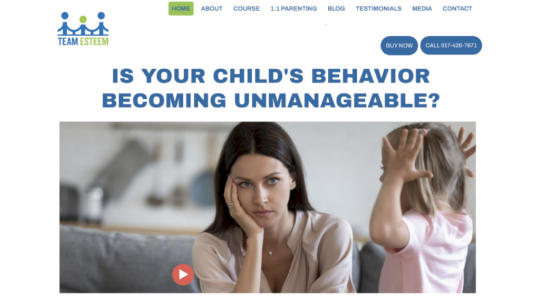
On April 20th, a blog post appeared on the website of “TeamEsteem” (teamesteemmethod.com), offering a download for a pirated version of Snow White (2025). Our research uncovered that this post was malicious, containing a magnet torrent link leading users straight into a malware trap.

Original website
The post appeared legitimate on the surface, but Veriti researchers identified it as a sophisticated lure. We believe attackers either:
- Exploited an XSS vulnerability (CVE-2023-40680) in an outdated Yoast SEO plugin, or
- Gained access via leaked admin credentials.
This blog entry redirected users to download a torrent containing an infected file package, a classic bait tactic leveraging user interest in pirated content.
The blog’s referenced link to download the movie: https://teamesteemmethod
Screenshot of compromised TeamEsteem blog post offering the fake Snow White torrent
A Dangerous Package Disguised as a Movie Download
Upon downloading the torrent, Veriti analysts discovered a three-file package. The bundle appeared typical of pirated movie releases but included a malicious executable posing as a necessary codec installer.
Interestingly, the file showed that 45 users were actively seeding the content, likely a combination of unwitting victims and attacker-controlled peers to increase legitimacy and speed up distribution.

File breakdown inside the torrent package
Among the files:
- A README file explaining the need for a “special codec” to play the video.
- A suspicious file: xmph_codec.exe — claiming to be the required video codec.
This tactic echoes older social engineering ploys, where users were tricked into installing codec packs to view pirated videos. The attackers revive this method with a modern twist: now embedding advanced malware into the “codec” installer.
The ‘Codec’ That Opens the Door to Deeper Threats
When users run the xmph_codec.exe file, they initiate a sophisticated malware deployment process. Here’s what Veriti’s analysis uncovered:
- Detected as malicious by 50 out of 73 security vendors (VirusTotal)
- Compiled on July 12, 2024, suggesting re-use from prior campaigns
- Unsigned executable, raising further red flags about origin
- Drops additional malicious files onto the system
- Silently downloads and installs the TOR browser
- Initiates communication with a Dark Web .onion domain
- Disables Windows Defender and other built-in security features
Screenshot of the README explaining codec use
VirusTotal detection of xmph_codec.exe

Screenshot of the Video Codec installation
Dark Connections: Infrastructure and Indicators
Once installed, the malware reaches out to an Onion-based C2 server:
http://cgky6bn6ux5wvlybtmm3z255igt52ljml2ngnc5qp3cnw5jlglamisad./onion
http://cgky6bn6ux5wvlybtmm3z255igt52ljml2ngnc5qp3cnw5jlglamisad./onion/route.php
The attacker leverages the anonymity of the TOR network to mask communications and evade traditional detection mechanisms.
Indicators of Compromise (IoCs)
- File hashes:
- 9c1a0608bae991af50096acaec9d979df9f9a3bb6e89d9d20972d6cfeb9582bb
- 2ec555c34f0af1514501ca5e4d999c843d5b9de7973467820fcf6034a517c4cc
- 8b81b0017c0e154c1fdea226f1ad0d3cfc0e301af05698bdbb7d0d6037d71a12
These hashes should be used for detection and blocking across enterprise EDR and firewall platforms.
Old Tricks, New Tech, Real Threats
This campaign revives an old-school tactic: using fake codec installers, but merges it with modern malware delivery methods, TOR communications, and anti security evasion techniques.
From our perspective, this highlights two key takeaways:
- Pirated content is still a potent malware delivery method, especially for trending, high-interest media.
- Attackers are exploiting outdated platforms and plugins, such as WordPress plugins, to create trustworthy lures.
Veriti Research Team Recommends:
- Avoid pirated content – it’s not worth the risk.
- Monitor for the listed IoCs in your environment.
- Patch outdated CMS platforms and plugins like Yoast SEO.
- Use layered security that includes behavioral analysis to catch unknown threats.
Stay safe, and let’s all agree that downloading pirated movies might cost more than a theater ticket.
*** This is a Security Bloggers Network syndicated blog from VERITI authored by Veriti Research. Read the original post at: https://veriti.ai/blog/beware-the-bad-apple-in-the-torrent/
Original Post URL: https://securityboulevard.com/2025/03/snow-white-beware-the-bad-apple-in-the-torrent/?utm_source=rss&utm_medium=rss&utm_campaign=snow-white-beware-the-bad-apple-in-the-torrent
Category & Tags: Security Bloggers Network,Blog,research – Security Bloggers Network,Blog,research
Views: 5