Source: heimdalsecurity.com – Author: Livia Gyongyoși
Meet Linda, the CFO of a multinational company. She is currently on her way to a business conference on the other side of the world.
Linda makes many more trips like this these days. Once upon a time, jet-setting across the world meant no access to files, emails, or messages for the whole time she was away.
Today, she can simply take her laptop or work phone and log into Slack, Outlook, or Teams, wherever she is. As a CFO, the last thing she wants is to be kept out of the loop for the best part of a week. Mobile devices and Wi-Fi make her life a lot easier.
This is all well and good until Linda realizes she’s left her work laptop in the taxi on the way to the conference center.
On that laptop, there are realms of sensitive information about the company’s finances and confidential details about the employees in Linda’s finance team. And it’s fair to say that her approach to password security is not something the IT team would endorse.
Even a rudimentary hacker wouldn’t have to try that hard to get into the device. If they did, Linda and the wider company would be in serious trouble.
So, what do they do now?
What is Unified Endpoint Management?
Situations like Linda’s are a common challenge of using remote and mobile devices. When desktop computers were wired up to a corporate network in a physical office, they were pretty difficult to misplace. Now we need a whole new approach to security.
Luckily, Linda’s IT team uses an endpoint management tool. This means the System Admin can remotely wipe clean the device at the click of a button. Now, if a hacker gets hold of the device, it’ll be next to useless. They won’t find any sensitive information on it.
Over the last decade, a range of endpoint management tools have evolved to help IT teams complete remote device enrollment, manage, and wipe devices like Linda’s. Unified Endpoint Management (UEM) is the latest and widest of these tools.
UEM’s popularity grew during the last few years. As the name suggests, the products feature a range of tools to help manage various user devices:
- smartphones
- laptops
- tablets
- smartwatches, etc.
In fact, the goal of these tools is to manage the broadest possible range of devices in one consolidated window.
Endpoint management vs. endpoint security
Unified Endpoint Management belongs to a broader family of cybersecurity tools known as endpoint management. UEM is the most recent tool in this family, which includes several different tools (see next section for details).
Before we dig into the details, let’s see how endpoint management tools differ from endpoint security tools.
Given the similarity of the names, you’d expect these tools to have plenty in common. But while there is some crossover, they in fact refer to two different branches of cybersecurity.
- Endpoint management: Including tools like MDM, MAM, UEM, and EMM. These focus on giving IT teams visibility and control over endpoint devices and the apps they’re accessing. Common features might include managing access, remotely locking or wiping the device, controlling access to apps, location tracking, and password management.
- Endpoint security: This includes tools like SIEM, EDR, XDR, EPP, MDR, and MXDR. These focus more on specific data security challenges like phishing, software vulnerabilities, network connections, and malware. They include features to manage vulnerabilities, monitor user activity, as well as detecting and isolating real-time security threats.
As you can expect, there is some crossover between these two ‘families’ of security tools. But they have distinctly different approaches and specialties. Features like vulnerability management are often available in both sets of tools. But that isn’t the case for everything.
Generally, these still remain separate branches of cybersecurity. Many organizations will find themselves needing some combination of both. Some providers, like Heimdal, offer platforms that combine functionality from both sets of tools. More on this below.
UEM vs. EMM and more: Which endpoint management tools do you need?
Now, let’s focus on how UEM differs from other endpoint management tools.
Luckily, the situation here is more clear-cut. You could sum it up like this: Previous endpoint management tools specialized in managing one particular type of remote device. UEM changed this approach by creating a single platform to manage all your devices.
Here’s a bit more detail on the various endpoint management tools:
Traditional tools
Before remote devices became the norm, there was less need to manage endpoints in the same way we do today. Nonetheless, traditional security tools allowed IT teams to maintain an inventory of devices. They could also create rudimentary protection policies, like password security, largely for desktop computers and laptops.
Mobile device management (MDM)
MDM first became popular after companies started to use smartphones. It allowed IT teams to remotely manage, provision, and wipe data from company-owned mobile devices. These tools give IT teams full and remote control over such devices:
- install/remove apps
- govern access
Mobile application management (MAM)
MDM gives IT teams complete control over the endpoint. So, even if it’s useful, you can’t rely on MDM if work apps are installed on employee-owned devices. You should then choose MAM. Mobile application management extends MDM policies only to specific apps.
This is generally done via ‘containerization’, a sandbox that prevents visibility and data transfer between personal and corporate apps.
Enterprise mobility management (EMM)
EMM tools are effectively the predecessor to UEM. They merge MDM and MAM functionalities and also add support for managing additional endpoints:
- IoT devices
- rugged devices
- wireless access points
Unified endpoint management (UEM)
UEM is the most comprehensive endpoint management tool. These products include all the functionality from the others in this list. Besides, they remotely track and manage company desktops and laptops. In effect, this allows IT teams to provision and manage everything from one window. UEM reduces the need for excessive licenses, costs, and confusion.
Today’s organizations increasingly need to manage and monitor a wide range of endpoints, including laptops, smartphones, tablets, IoT devices, and more. If this sounds like you, UEM is almost certainly the right choice.
Read more: The Top 7 Unified Endpoint Management Tools in 2024
Nine essential features of Unified Endpoint Management
While no two UEM products offer the exact same functionality, there are some essential features to look for:
A single interface
Using a single interface increases visibility and eases management over laptops, smartphones, rugged devices, IoTs, etc. Unified dashboards make it a lot easier for IT teams to understand, provision, and manage the whole range of endpoints.
Remote patch deployment
IT teams can close known vulnerabilities faster by remotely installing updates and patches. Timely patching of third-party apps and various operating systems bolsters the security posture.
Access management
IT teams need access management tools to govern permissions to sensitive files, apps, and endpoints. This includes some level of both identity and access management (IAM) and privileged access management (PAM) functionality. However, these tools are generally more limited than specialized privileged access management (PAM) products.
Remote device management
Using remote device management tools enables IT teams to lock, unlock, or wipe data on registered devices outside the office. This helps maintain security on lost or stolen devices – like in the example at the top of this blog. IT teams can also remotely deprovision and/or wipe devices when employees leave.
App containerization
App containerization replicates MAM functionality. You can use it to separate and track corporate apps on employee-owned devices. It supports BYOD work policies.
Application allowlisting
IT teams use app management policies to govern which apps an end user has access to. This works in two ways:
- blacklisting – banning specific apps
- whitelisting – only allowing apps on a pre-defined list, which is more restrictive.
Password policies
Password policies allow you to establish password changing frequency and strength. You can also enforce multi-factor authentication (MFA) or track sign-in attempts.
Location tracking
Location tracking helps security teams to track and recover lost or stolen devices.
The word ‘remote’ comes up a lot in this list of features. It is the reason why UEM tools have become increasingly important in recent years. This feature is what keeps going the world of remote working. Previously, the IT team needed to enter each office and log in as an admin on each device to perform their tasks. Now, a more sophisticated range of tools enables them save time and budget while maintaining infrastructures worldwide.
Consolidating UEM, EDR, and more
In the last few years, a lot of solution providers have released new products that solve single problems. Now, the number of security solutions is becoming a risk itself, because they need to be maintained and updated, they have license costs, and it all increases the complexity of your IT environment.
The unified approach therefore tries to connect these disparate elements so you can switch out solutions and replace them with fewer licenses that solve more problems.
Source – Thomas Engli Baasnes, Cybersecurity Director, Verdane
In the last few years, the cybersecurity market has reached saturation point. IT environments became more complex and distributed. So, organizations adopted more and more tools to address specific cybersecurity challenges.
But at some point, having so many different types of cybersecurity tools does more harm than good.
That’s why MSPs and MSSPs would rather go for a consolidated, unified approach, like UEM solutions. These tools simplify IT management and strengthen defense by reducing cost, complexity, and confusion.
But even unified endpoint management is far from the only cybersecurity product you’ll ever need. To have a complete suite, there are a whole range of other tools you’ll need to add to the list:
- endpoint protection
- SIEM
- vulnerability management
- in-depth privileged access management
- DNS and network security
- Email security, etc.
So, what’s the solution?
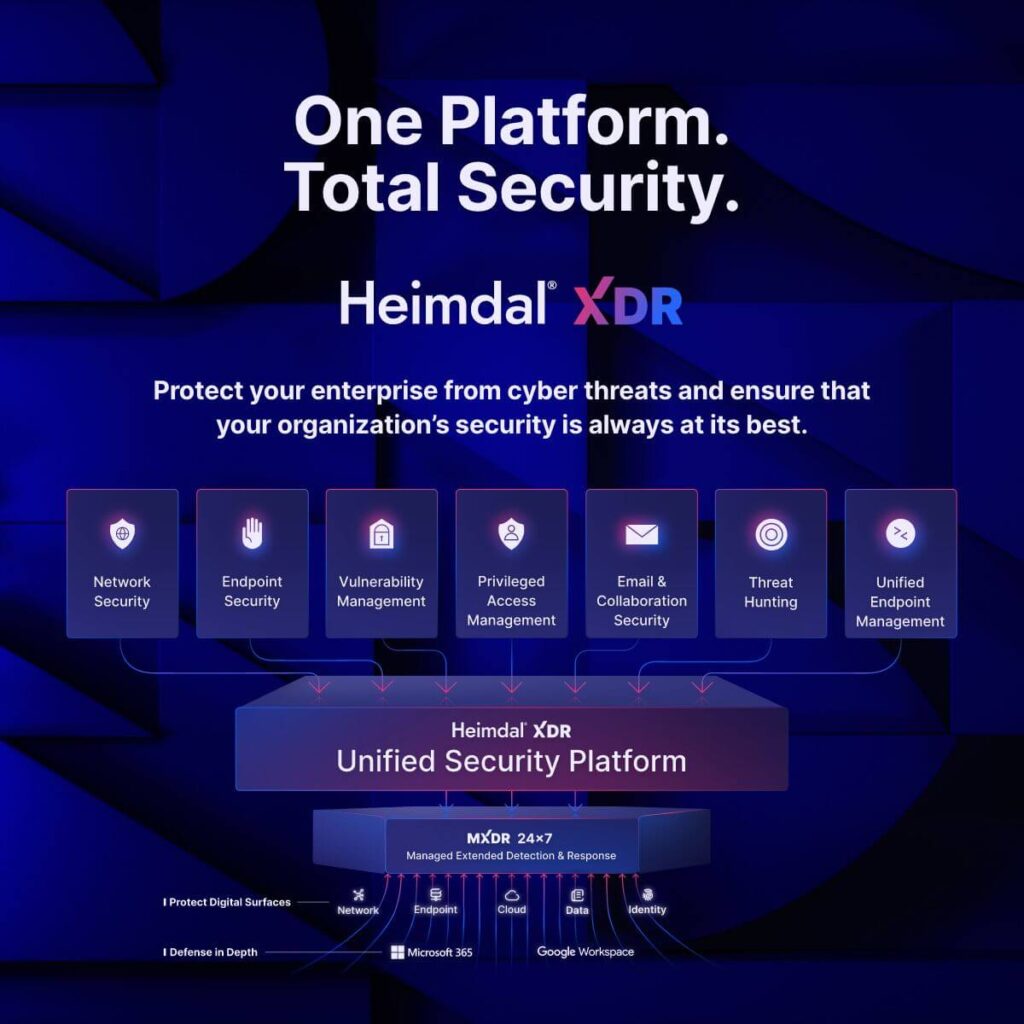
At Heimdal, we take a different approach. Instead of just consolidating endpoint management tools, we offer the broadest cybersecurity platform on the market, including:
- DNS network security and cloud ransomware protection.
- Endpoint protection with next-gen antivirus, firewalls, and ransomware encryption protection.
- Vulnerability management – install, manage, and prioritize patches across both apps and operating systems.
- Privileged access management enables you to track, manage, and secure access to sensitive assets, through privilege elevation and delegation management (PEDM), application control, and privileged account and session management (PASM).
- Email & collaboration security helps prevent issues like phishing and email-based data leakage by analyzing emails and identifying suspicious activity.
- Threat hunting combines functionality from EDR, XDR, and EPP platforms, with an optional managed service. This helps identify and protect against real-time attacks like ransomware, code injection, data exfiltration, and much more.
- Unified endpoint management includes all the features we discussed in this blog, consolidating functionality from MDM, MAM, and EMM tools.
Heimdal’s unified security platform is the absolute best way to reduce cybersecurity licenses, costs, and confusion. This creates a simpler IT suite and better overall security.
Check out our full security platform to find out more.
Unified endpoint management: FAQs
What is unified endpoint management?
UEM tools let IT teams manage the widest possible range of remote devices from one unified interface. This includes the tools to remotely manage, provision, and wipe data from devices like laptops, tablets, smartphones, IoT devices, and apps on employee-owned devices. UEM consolidates features from MDM, MAM, and EDM products, which each have a narrower focus.
What is the difference between MDM and unified endpoint management?
Mobile device management (MDM) is a cybersecurity tool specialized in managing company-owned smartphones. Unified endpoint management is a more expansive tool, enabling management of a broad range of security devices. MDMs have become increasingly redundant in recent years because they can only manage one type of device. They also struggle to effectively manage specific apps on an employee’s own device.
What are UEM and EDR tools?
Unified endpoint management (UEM) is a cybersecurity platform that helps IT teams remotely manage and secure devices. Endpoint detection and response (EDR) focuses on detecting and responding to threats like phishing and malware deployment.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.
Livia Gyongyoși is a Communications and PR Officer within Heimdal®, passionate about cybersecurity. Always interested in being up to date with the latest news regarding this domain, Livia’s goal is to keep others informed about best practices and solutions that help avoid cyberattacks.
Original Post URL: https://heimdalsecurity.com/blog/unified-endpoint-management-perks/
Category & Tags: Endpoint security,Industry trends – Endpoint security,Industry trends
Views: 2