Source: securityboulevard.com – Author: Devasmita Das
The Growing Cybersecurity Threat in OT Environments
As industries undergo digital transformation, the convergence of Information Technology (IT) and Operational Technology (OT) is fundamentally reshaping the landscape of critical infrastructure. This convergence brings notable benefits, including improved productivity, cost savings, and operational efficiencies. However, it also expands the attack surface of OT environments, making them more susceptible to cyber threats. The growing integration of Cyber-Physical Systems (CPS), Industrial Internet of Things (IIoT), and smart technologies has amplified security challenges, creating more opportunities for cybercriminals to exploit vulnerabilities.
A concerning trend in recent months has been the increased targeting of poorly secured, internet-exposed OT devices. According to Microsoft, since late 2023, there has been a significant uptick in attacks focusing on OT systems, particularly those that are poorly protected and exposed to the internet. These attacks have targeted critical infrastructure systems, such as water and wastewater facilities in the United States. Nation-backed actors, including groups such as IRGC-affiliated “CyberAv3ngers,” a suspected Iranian Government Islamic Revolutionary Guard Corps (IRGC)-affiliated APT group, and pro-Russian hacktivists, have been linked to these attacks. These breaches highlight the critical need for enhanced security practices within OT environments, especially as they become more interconnected with IT networks and exposed to external threats.
Diagram 1: Sample images of victim systems as posted by actors on their Telegram channels
(Source)
One of the most alarming threats to OT systems is ransomware. The Claroty 2023 Global State of Industrial Cybersecurity Report revealed a 10% increase in ransomware attacks on both IT and OT systems from 2021 to 2023. As OT systems become increasingly interconnected with IT, they are more frequently targeted by cybercriminals.
To address these growing risks, it’s clear that a paradigm shift in cybersecurity is needed. Traditional perimeter-based security measures are no longer enough to protect OT systems against the increasingly sophisticated threats targeting them. The answer lies in adopting a Zero Trust model, which operates under the principle of “never trust, always verify.”
Zero Trust in OT: An Evolving Approach
Zero Trust security has long been a core principle in OT environments, although it wasn’t always labeled as such. Initially, air gapping offered a basic form of Zero Trust by physically isolating OT systems from wider IT networks, preventing unauthorized access. As technology advanced, microsegmentation, a concept formalized in the IEC 62443 standard, became the key approach for ensuring Zero Trust within OT. By dividing networks into smaller, isolated segments, microsegmentation limits the movement of any attacker within the network.
However, as OT networks become more connected and integrated with IT infrastructure, implementing Zero Trust needs to be both effective and low impact.
The Claroty–ColorTokens joint solution simplifies this implementation, providing a cost-effective, minimal-disruption approach to Zero Trust security.
Claroty: Advanced Industrial Cybersecurity with xDome
Claroty provides a comprehensive industrial cybersecurity platform designed to protect critical infrastructure environments. The Claroty xDome is a SaaS-powered, scalable solution that offers advanced cybersecurity controls across a wide range of use cases. Seamlessly integrating with your existing tech stack, xDome is designed for flexibility and ease of use. The core of the platform is the Essentials module, which provides powerful tools for in-depth network discovery, vulnerability and risk management, threat detection, and asset management.
In addition to these foundational features, xDome can be expanded with advanced modules, including Vulnerability and Risk Management, Network Security, and Threat Detection, to enhance protection further. By offering comprehensive visibility and control over OT environments, Claroty helps organizations identify, prioritize, and remediate vulnerabilities, enabling them to stay ahead of potential cyber threats.
ColorTokens: Zero Trust Security with Xshield
ColorTokens delivers a cutting-edge approach to securing OT environments through its Xshield platform, leveraging Zero Trust security principles. Using a combination of agent-based and agentless options, Xshield
platform, leveraging Zero Trust security principles. Using a combination of agent-based and agentless options, Xshield enables organizations to visualize their OT devices and applications, providing real-time insights into how these components communicate. This contextual visualization allows for a more robust, enterprise-wide security posture. The platform uses Zero Trust microsegmentation to prevent the lateral movement of malware or ransomware, ensuring that even if a breach occurs, it cannot easily spread across the network. Xshield
enables organizations to visualize their OT devices and applications, providing real-time insights into how these components communicate. This contextual visualization allows for a more robust, enterprise-wide security posture. The platform uses Zero Trust microsegmentation to prevent the lateral movement of malware or ransomware, ensuring that even if a breach occurs, it cannot easily spread across the network. Xshield supports segmentation for all asset types, including ICS systems, data center servers, cloud workloads, Kubernetes containers, IoT devices, and even legacy systems. With a unified administration console, Xshield
supports segmentation for all asset types, including ICS systems, data center servers, cloud workloads, Kubernetes containers, IoT devices, and even legacy systems. With a unified administration console, Xshield streamlines the management of security policies across diverse environments, providing a comprehensive, layered defense across the network.
streamlines the management of security policies across diverse environments, providing a comprehensive, layered defense across the network.
The Claroty-ColorTokens Joint Solution: A Unified Approach to OT Security
The Claroty–ColorTokens joint solution provides comprehensive protection for Cyber-Physical Systems (CPS) environments, addressing key cybersecurity challenges such as:
- Asset Inventory and Continuous Monitoring: Claroty xDome ensures complete visibility of every asset in the OT environment, continuously discovering and profiling devices across the network. This ongoing monitoring provides real-time insights, enabling organizations to track every device and identify potential risks proactively.
- Exposure Management and Threat Detection: Leveraging Claroty’s advanced vulnerability management capabilities, the integration prioritizes remediation based on asset criticality. Continuous monitoring from Claroty’s detection systems, including deep packet inspection and anomaly detection, enables early identification of both known and unknown threats.
- Network Protection via Microsegmentation: ColorTokens Xshield
 enforces Zero Trust principles by applying microsegmentation across the OT environment, segmenting the network into smaller, controlled zones. This approach limits the attack surface and prevents lateral movement, ensuring that even if one segment is compromised, the threat cannot spread across the network.
enforces Zero Trust principles by applying microsegmentation across the OT environment, segmenting the network into smaller, controlled zones. This approach limits the attack surface and prevents lateral movement, ensuring that even if one segment is compromised, the threat cannot spread across the network. - Least Privilege: ColorTokens Xshield
 enforces strict access policies, ensuring that only authorized devices and users can interact with the network and its assets. By maintaining a unified security posture across both IT and OT environments, ColorTokens reinforces the Zero Trust framework, preventing unauthorized access and reducing the overall attack surface.
enforces strict access policies, ensuring that only authorized devices and users can interact with the network and its assets. By maintaining a unified security posture across both IT and OT environments, ColorTokens reinforces the Zero Trust framework, preventing unauthorized access and reducing the overall attack surface. - Comprehensive Protection Across IT and OT Environments: The integration of Claroty and ColorTokens delivers robust, unified security across both IT and OT systems by applying consistent Zero Trust policies throughout. This seamless integration ensures that all assets, regardless of their environment, are continuously monitored, properly segmented, and protected, minimizing vulnerabilities and reducing the risk of potential breaches between the IT and OT networks.
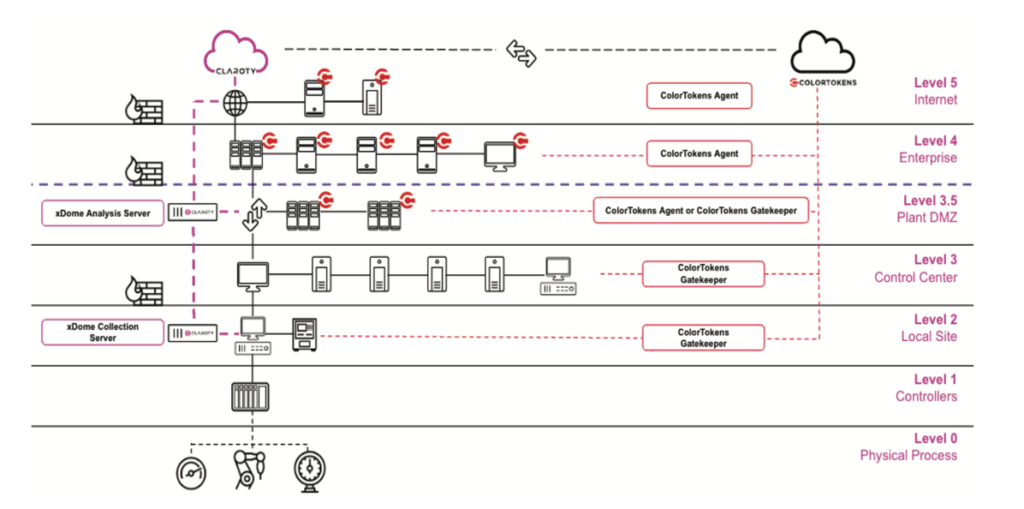
Diagram 2: Combined Deployment Architecture of Claroty and ColorTokens Solution
As illustrated in Diagram 2, Claroty provides rich asset data from the OT environment to the ColorTokens policy engine via a seamless connection between their SaaS instances. This data includes critical asset attributes such as device types, communication patterns, and security vulnerabilities. Leveraging this data, Claroty suggests optimal segmentation strategies for the OT network, which are then used to create Zero Trust traffic policies in the ColorTokens Xshield policy engine. These policies ensure that only trusted traffic is allowed both within microsegment zones and across zone boundaries, preventing unauthorized access and lateral movement.
policy engine. These policies ensure that only trusted traffic is allowed both within microsegment zones and across zone boundaries, preventing unauthorized access and lateral movement.
By integrating Claroty’s asset visibility with ColorTokens’ microsegmentation, this joint solution delivers a proactive, breach-ready defense against cyber threats. Real-time asset monitoring, Zero Trust segmentation, and comprehensive exposure management work together to create a resilient enterprise architecture. This integrated solution ensures that if a breach occurs—whether from the IT or OT network—it is swiftly contained and mitigated, preserving operational continuity and reinforcing the overall security posture.
Benefits of the Integration:
- Enhanced Asset Visibility: Claroty xDome provides a comprehensive view of the OT environment, while ColorTokens Xshield
 ensures that only trusted devices can communicate, minimizing the attack surface.
ensures that only trusted devices can communicate, minimizing the attack surface. - Reduced Attack Surface: Through microsegmentation, ColorTokens significantly limits the entry points for attackers. Even if one network segment is compromised, the rest remain protected.
- Proactive Threat Detection: Claroty’s real-time monitoring, combined with ColorTokens’ Zero Trust policies, enables early detection of threats and rapid remediation to minimize damage.
- Regulatory Compliance: The joint solution helps organizations meet essential cybersecurity regulations, such as EU NIS2, US NIST, and Australia’s SOCI, ensuring both security and compliance.
The Claroty–ColorTokens joint solution offers a powerful, integrated approach to securing OT environments. By combining Claroty’s visibility and threat detection with ColorTokens’ microsegmentation, organizations can significantly reduce their exposure to cyberattacks, ensure compliance, and maintain continuous operations.
As OT systems increasingly integrate with IT, the need for Zero Trust has never been greater. Adopting Zero Trust is no longer just a best practice—it is essential to protect the backbone of critical infrastructure and ensure the resilience of OT networks in the face of evolving cyber threats.
Ready to strengthen your OT security with Zero Trust? Connect with our experts.
Original Post URL: https://securityboulevard.com/2025/04/securing-ot-environments-with-zero-trust-a-joint-approach-by-colortokens-and-claroty/?utm_source=rss&utm_medium=rss&utm_campaign=securing-ot-environments-with-zero-trust-a-joint-approach-by-colortokens-and-claroty
Category & Tags: Security Bloggers Network,integrations,Manufacturing Technology,OT security,Zero Trust Architecture – Security Bloggers Network,integrations,Manufacturing Technology,OT security,Zero Trust Architecture
Views: 3





















































