Source: securityboulevard.com – Author: Devesh Patel
Let’s dive into the practical side of building SCIM implementations that won’t keep you up at night worrying about security breaches or schema conflicts. If you’ve been working with SCIM for a while, you’ve probably discovered that the basic specification gets you started, but real-world enterprise requirements quickly push you into more advanced territory.
Think of this as your field guide to the two areas where most SCIM implementations either shine or completely fall apart: extending the schema to handle your application’s unique data needs, and securing your endpoints so they can handle the wild west of enterprise network environments.
Understanding SCIM Schema: Your Data Foundation
Before we jump into extending schemas, let’s make sure we’re all on the same page about what SCIM schema actually does. If you’re coming from a database background, think of SCIM schema like table definitions – it tells everyone involved what fields exist, what types of data they can hold, and which ones are required.
The beauty of SCIM is that it comes with a solid foundation schema that covers the basics every application needs: user names, email addresses, phone numbers, and group memberships. But here’s where it gets interesting – almost every real application needs more than just the basics.
Let me walk you through a concrete example that’ll make this crystal clear. Imagine you’re building a project management tool, and your enterprise customers need to provision users with specific project assignments, billing rates, and skill tags. The standard SCIM schema doesn’t know anything about projects or billing rates, so you need to extend it to handle your application’s specific requirements.
The SCIM specification was designed with this exact scenario in mind. Rather than trying to anticipate every possible use case (which would be impossible), the authors created a flexible extension mechanism that lets you add your own attributes while keeping everything compatible with standard SCIM clients.
The Art of Schema Extension
Let’s start with the simplest type of schema extension – adding custom attributes to the standard User resource. This is usually where most people begin, and it’s a great way to get comfortable with how SCIM handles extensibility.
Here’s how you’d extend the User schema to include a project assignment field:
{ "schemas": [ "urn:ietf:params:scim:schemas:core:2.0:User", "urn:yourcompany:params:scim:schemas:extension:projectmanagement:2.0:User" ], "userName": "[email protected]", "name": { "givenName": "John", "familyName": "Doe" }, "emails": [{ "value": "[email protected]", "primary": true }], "urn:yourcompany:params:scim:schemas:extension:projectmanagement:2.0:User": { "defaultProject": "mobile-app-redesign", "billingRate": 125.00, "skillTags": ["javascript", "react", "mobile-design"] } } Notice how the extension lives in its own namespace (that long URN starting with your company name) and gets included as a separate schema in the schemas array. This approach keeps your custom fields clearly separated from the standard ones, which makes debugging much easier and prevents conflicts if the SCIM specification ever adds fields with similar names.
The schema URN might look intimidating, but it’s just a way to uniquely identify your extension. Think of it like a package name in programming – it needs to be unique across the entire internet, so using your company domain in reverse (like Java packages) is a common approach.
Designing Schema Extensions That Scale
Here’s where most people make their first big mistake with schema extensions – they add fields one at a time as they need them, without thinking about the bigger picture. This leads to sprawling, inconsistent schemas that become nightmare to maintain as your application grows.
Instead, think about your schema extensions like you’d think about database design. Group related fields together logically, use consistent naming conventions, and plan for future growth. Let me show you what I mean with a more comprehensive example:
{ "urn:yourcompany:params:scim:schemas:extension:projectmanagement:2.0:User": { "projectAssignments": [{ "projectId": "mobile-app-redesign", "role": "lead-developer", "startDate": "2025-01-15", "endDate": "2025-06-30", "billableHours": 40 }], "skills": { "technical": ["javascript", "react", "mobile-design"], "languages": ["english", "spanish"], "certifications": ["aws-certified-developer"] }, "preferences": { "timezone": "America/Los_Angeles", "workingHours": { "start": "09:00", "end": "17:00" }, "notifications": { "email": true, "slack": false } } } } This approach groups related information together and uses consistent data structures. The projectAssignments array can handle multiple projects, the skills object organizes different types of skills logically, and the preferences section gives you room to grow as you add new user preference features.
When you’re designing schema extensions, think about these key principles:
Start by mapping out all the user-related data your application manages, even if you’re not planning to provision all of it via SCIM initially. This helps you design a schema that can grow without breaking changes.
Use consistent naming conventions throughout your extensions. If you use camelCase for one field, use it everywhere. If you use ISO date formats in one place, use them everywhere.
Group related fields into objects rather than flattening everything to the top level. This makes your schema more readable and easier to evolve over time.
Plan for arrays where it makes sense. Even if users only have one project assignment today, they might have multiple tomorrow. It’s much easier to design for arrays from the beginning than to change the schema later.
Advanced Schema Patterns
Once you’re comfortable with basic extensions, there are some advanced patterns that can make your SCIM implementation much more powerful. Let me walk you through a few that I’ve seen work well in production environments.
The first pattern is conditional schema extensions. Not every user in your system needs the same extended attributes. Maybe only managers need budget approval limits, or only developers need repository access permissions. You can design your schema to handle these cases gracefully:
{ "urn:yourcompany:params:scim:schemas:extension:projectmanagement:2.0:User": { "userType": "manager", "managerAttributes": { "budgetLimit": 50000, "approvalLevel": "department", "directReports": ["john.doe", "jane.smith"] } } } Another powerful pattern is hierarchical extensions. If your application has complex organizational structures, you can model these in your SCIM schema:
{ "urn:yourcompany:params:scim:schemas:extension:projectmanagement:2.0:User": { "organizationalHierarchy": { "company": "acme-corp", "division": "engineering", "department": "mobile-development", "team": "ios-team", "role": "senior-developer" } } } This pattern is particularly useful for applications that need to make authorization decisions based on organizational structure, or for reporting and analytics features that aggregate data by department or team.
Schema Validation and Error Handling
Here’s something that doesn’t get talked about enough – how to handle schema validation errors gracefully. When identity providers send you SCIM requests with invalid or missing data in your extensions, your endpoint needs to respond in a way that’s helpful for debugging but doesn’t break the provisioning process.
Let’s think through this step by step. When you receive a SCIM request, you need to validate both the standard SCIM fields and your custom extension fields. But here’s the key insight – you should be more flexible with extension fields than with core SCIM fields.
If someone sends you a user with an invalid email address, that’s a hard error – you can’t create a user without a valid email. But if they send you a user with an invalid project assignment in your extension, you might want to create the user anyway and just skip the invalid project assignment.
Here’s how you might structure your validation response:
{ "schemas": ["urn:ietf:params:scim:api:messages:2.0:Error"], "status": "400", "detail": "Invalid extension data", "scimType": "invalidValue", "errors": [ { "field": "urn:yourcompany:params:scim:schemas:extension:projectmanagement:2.0:User.projectAssignments[0].projectId", "error": "Project 'invalid-project' does not exist", "severity": "warning" } ] } This approach gives identity provider administrators enough information to fix the problem without completely blocking user provisioning for non-critical extension data.
Securing Your SCIM Endpoints: Beyond Basic Authentication
Now let’s shift gears and talk about security, which is where a lot of SCIM implementations have serious weaknesses. The basic SCIM specification mentions authentication but doesn’t provide detailed guidance on how to implement it securely in production environments.
Think about what your SCIM endpoints are doing – they’re accepting requests to create, modify, and delete user accounts in your system. From an attacker’s perspective, these endpoints are incredibly valuable targets. If someone can compromise your SCIM endpoint, they can potentially create admin accounts, modify existing user permissions, or delete users to cause service disruptions.
The first line of defense is strong authentication, but “strong authentication” means different things in different contexts. Let’s walk through the most common approaches and when to use each one.
Bearer Token Authentication: The Most Common Approach
Most SCIM implementations start with bearer token authentication because it’s simple and well-supported by identity providers. Here’s how it works – you generate a long, random token for each customer organization, and they include this token in the Authorization header of every SCIM request.
The key to making bearer tokens secure is in the details of how you generate, store, and validate them. Let me show you what a robust bearer token implementation looks like:
// Generate a cryptographically secure token const crypto = require('crypto'); const token = crypto.randomBytes(32).toString('hex'); // 64-character hex string // Store the token with metadata const tokenRecord = { token: hashToken(token), // Never store plain tokens organizationId: 'acme-corp', createdAt: new Date(), lastUsed: null, permissions: ['users:read', 'users:write', 'groups:read'], ipAllowList: ['203.0.113.0/24'], // Optional IP restrictions active: true }; Notice that we’re hashing the token before storing it, just like you would with user passwords. This means that even if someone gains access to your database, they can’t use the stored token values to make SCIM requests.
The permissions array lets you implement fine-grained access control. Maybe some customers only need read access to user data, or maybe they should only be able to manage users but not groups. Having this flexibility built into your authentication system from the beginning will save you headaches later.
OAuth 2.0: The Enterprise-Grade Approach
Bearer tokens work well for getting started, but many enterprise customers prefer OAuth 2.0 for SCIM authentication because it provides better token lifecycle management and more sophisticated security features.
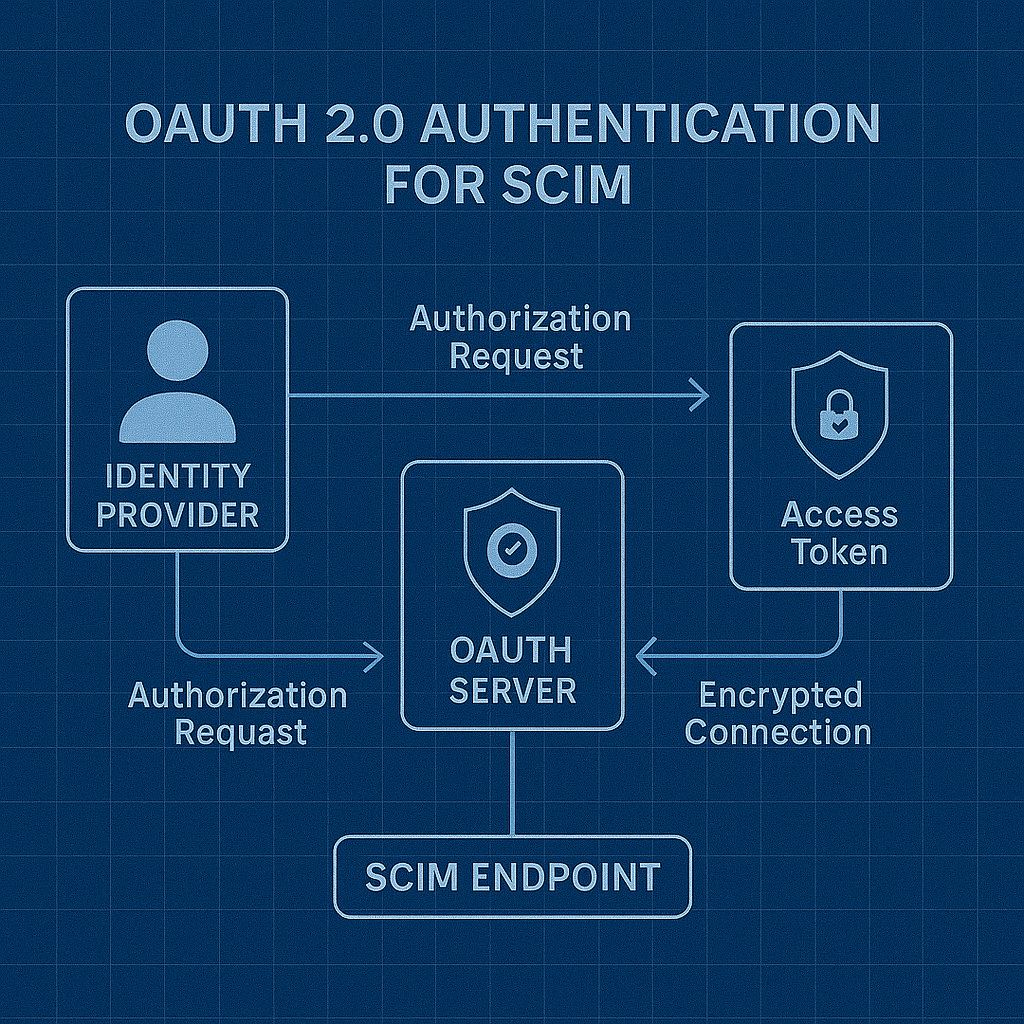
With OAuth 2.0, the identity provider obtains an access token from your OAuth server and includes that token in SCIM requests. The main advantage is that tokens can have expiration times and can be refreshed automatically, which reduces the security risk if a token gets compromised.
Here’s what an OAuth 2.0 SCIM authentication flow looks like:
The identity provider authenticates with your OAuth server using client credentials (client ID and client secret). Your OAuth server validates the credentials and issues a time-limited access token. The identity provider includes this access token in the Authorization header of SCIM requests. Your SCIM endpoint validates the access token with your OAuth server before processing the request.
This approach is more complex to implement, but it provides several security benefits. Tokens automatically expire, so compromised tokens have limited lifetime. You can revoke tokens immediately if needed. You get detailed audit logs of when tokens are issued and used. You can implement more sophisticated access controls based on the OAuth scopes.
If you’re building for enterprise customers, supporting OAuth 2.0 for SCIM authentication is often a requirement for security compliance.
Rate Limiting: Protecting Against Abuse
Even with strong authentication, you need to protect your SCIM endpoints against abuse. Rate limiting serves two purposes – it prevents malicious actors from overwhelming your system, and it prevents well-intentioned identity providers from accidentally causing performance problems with overly aggressive provisioning.
The tricky part about rate limiting SCIM endpoints is that legitimate usage patterns can vary dramatically. During initial provisioning, an identity provider might need to create hundreds or thousands of users in a short time period. But during normal operation, you might only see a few SCIM requests per hour.
Here’s a rate limiting strategy that handles both scenarios gracefully:
// Different rate limits for different operation types const rateLimits = { 'POST /scim/v2/Users': { burst: 100, // Allow 100 rapid user creations sustained: 10 // Then limit to 10 per minute }, 'PUT /scim/v2/Users': { burst: 50, // Allow 50 rapid updates sustained: 20 // Then limit to 20 per minute }, 'DELETE /scim/v2/Users': { burst: 10, // Be more restrictive with deletions sustained: 5 // Only 5 deletions per minute sustained } }; This approach uses a token bucket algorithm with different parameters for different types of operations. User creation gets a larger burst allowance because that’s needed for initial provisioning, but user deletion gets a smaller allowance because mass deletions are more likely to be either mistakes or attacks.
You should also implement rate limiting at multiple levels. Per-organization limits prevent one customer from affecting others. Per-IP limits provide protection against attacks. Global limits protect your overall system capacity.
Monitoring and Alerting for SCIM Security
Here’s something that often gets overlooked – you need good monitoring and alerting to detect security issues with your SCIM endpoints. Unlike user-facing parts of your application, SCIM endpoints are typically only accessed by automated systems, so unusual activity patterns might not be noticed immediately.
Set up alerts for these security-relevant events:
Authentication failures, especially patterns that suggest credential stuffing or brute force attacks. Unusual request volumes, both high and low – a sudden spike might indicate an attack, while a sudden drop might indicate a configuration problem. Requests from unexpected IP addresses, if you’re using IP allow-listing. Error rates above normal thresholds, which might indicate either attacks or configuration problems.
For each alert, make sure you have enough context to investigate effectively. Log the organization ID, IP address, user agent, request details, and error messages. This information will be invaluable when you’re trying to figure out whether an alert represents a real security issue or just a configuration problem.
Advanced Security Patterns
Once you have the basics of authentication, rate limiting, and monitoring in place, there are some advanced security patterns that can make your SCIM implementation even more robust.
One pattern that works well for high-security environments is request signing. In addition to bearer token authentication, you can require identity providers to sign their SCIM requests using a shared secret or public key cryptography. This provides protection against token theft and man-in-the-middle attacks.
Another advanced pattern is request replay protection. By requiring a timestamp and nonce in each request, you can prevent attackers from capturing and replaying SCIM requests even if they manage to obtain valid authentication credentials.
For organizations with very strict security requirements, you might implement mutual TLS authentication. This requires both the client and server to present valid certificates, providing strong authentication at the transport layer in addition to your application-layer authentication.
Testing Your Security Implementation
Security implementations are notoriously difficult to test thoroughly, but there are some specific scenarios you should validate for your SCIM endpoints.
Test authentication bypass attempts by sending requests without authentication headers, with invalid tokens, and with tokens for different organizations. Make sure your endpoint correctly rejects all of these scenarios.
Test rate limiting behavior by sending requests at various rates and confirming that your limits are enforced correctly. Pay special attention to edge cases like requests that arrive exactly at the rate limit threshold.
Test error handling by sending malformed requests, requests with invalid data, and requests that should trigger various error conditions. Make sure your error responses don’t leak sensitive information that could help attackers.
Test your monitoring and alerting by triggering the conditions that should generate alerts and confirming that alerts are actually generated and contain useful information.
Consider using automated security testing tools that can help identify common vulnerabilities in your SCIM endpoints. Tools like OWASP ZAP can be configured to test API endpoints for common security issues.
Schema and Security Working Together
As we wrap up this deep dive into SCIM best practices, it’s worth thinking about how schema design and security considerations interact with each other. The decisions you make about schema extensions can have significant security implications, and your security requirements might influence how you design your schema.
For example, if you’re extending your schema to include sensitive information like salary data or performance ratings, you’ll need to think carefully about who should have access to read and modify these fields. You might implement field-level access controls where some users can be provisioned with basic information by one set of credentials, while sensitive fields require different, more restricted credentials.
Similarly, if your schema includes fields that affect user permissions in your application, you’ll want to audit changes to these fields carefully. A change to someone’s role or project assignments might need to be logged and reviewed differently than a change to their phone number.
The key insight is that SCIM schema and security aren’t separate concerns – they’re two parts of a complete identity management system that need to work together seamlessly. The best SCIM implementations are the ones where schema design, security implementation, and business requirements all align to create a system that’s both powerful and safe.
Building a robust SCIM implementation takes time and careful attention to detail, but the payoff is enormous. When done well, SCIM becomes invisible infrastructure that just works, enabling your enterprise customers to scale their identity management without thinking about it. When done poorly, it becomes a constant source of support tickets and security concerns.
The practices we’ve covered here – thoughtful schema design, robust authentication, comprehensive rate limiting, and careful monitoring – form the foundation of SCIM implementations that can handle real-world enterprise requirements. Take the time to implement them properly, and your future self (and your enterprise customers) will thank you.
*** This is a Security Bloggers Network syndicated blog from SSOJet authored by Devesh Patel. Read the original post at: https://ssojet.com/blog/scim-best-practices-building-secure-and-extensible-user-provisioning/
Original Post URL: https://securityboulevard.com/2025/06/scim-best-practices-building-secure-and-extensible-user-provisioning/?utm_source=rss&utm_medium=rss&utm_campaign=scim-best-practices-building-secure-and-extensible-user-provisioning
Category & Tags: Identity & Access,Security Bloggers Network,Authentication,b2b,B2B SaaS,CIAM,enterprise,enterprise security,Enterprise SSO,Identity & Access Management (IAM),SAML,SCIM,security,single sign on,sso – Identity & Access,Security Bloggers Network,Authentication,b2b,B2B SaaS,CIAM,enterprise,enterprise security,Enterprise SSO,Identity & Access Management (IAM),SAML,SCIM,security,single sign on,sso
Views: 7





















































