Source: hackread.com – Author: Deeba Ahmed.
Russian APT group Storm-2372 employs device code phishing to bypass Multi-Factor Authentication (MFA). Targets include government, technology, finance, defense, healthcare.
Cybersecurity researchers at SOCRadar have discovered a new attack tactic used by the notorious Russian state-backed advanced persistent threat (APT), Storm-2372. According to SOCRadar’s research, shared with Hackread.com, Storm-2372 can now break into online accounts of major organizations without trying to guess passwords.
This is achieved through a method called “device code phishing,” which helps them get around even strong security measures like Multi-Factor Authentication (MFA).
Device Code Phishing takes advantage of the way some devices, like smart TVs, connect to online services. Usually, these devices give you a special code that you type into a website on your computer or phone to log in (OAuth device authorization flow). Hackers are using this same process to fool people into giving them access to their work accounts.
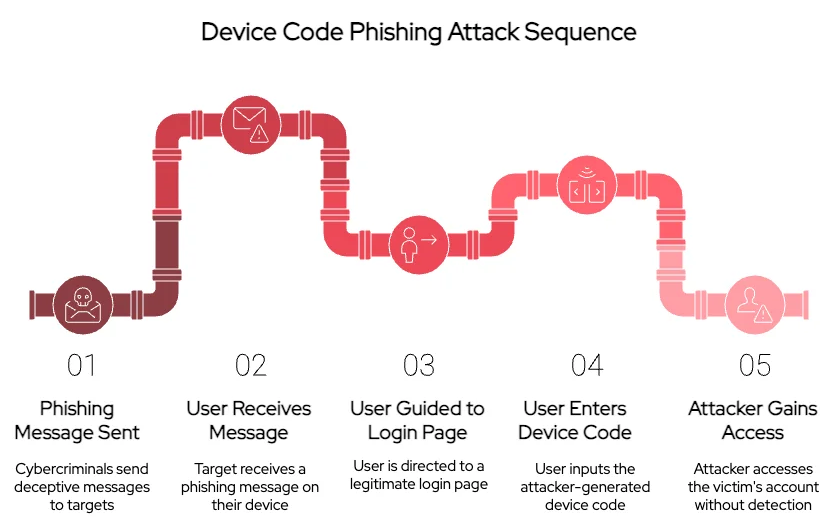
Here’s how it works
The hackers send fake messages, often through email or text, telling people they need to use a device code to log in. These messages direct them to real-looking login pages, like the ones from Microsoft. The victims then unknowingly type in a code that the hackers have created. Once the person enters the code, the hackers can get into their account without needing a password or triggering the usual security checks. This makes it much harder to spot the attack as the victims don’t realize they have been compromised until it is too late.
Previously, the method OG Device Code Phishing was used by hackers to create a device code using special tools and sent it via message. However, these codes only lasted about 15 minutes, making it difficult for hackers to log in if the person didn’t see the message.
Storm-2372 employs the more advanced Dynamic Device Code Phishing technique, previously documented by Black Hills in 2023, to create fake websites resembling real login pages using services like Azure Web Apps. When a user visits these fake sites, they generate a new device code, allowing hackers to log in. They sometimes use CORS-Anywhere to display the code correctly in the user’s browser. When the user enters the fake code, they receive access tokens and refresh tokens, allowing hackers to access Microsoft email for up to three months.
Storm-2372 is, reportedly, targeting organizations that hold valuable information and make important decisions. This includes government agencies, technology companies, banks, defence contractors, healthcare providers, and media companies. They’ve been seen attacking organizations in countries like the United States, Ukraine, the United Kingdom, Germany, Canada, and Australia.
This new trick shows that these hackers are getting better at fooling people to get past even good security systems, and companies need to find smarter ways to protect themselves from such sneaky attacks.
“The campaign underlines the critical need for modern organizations to embrace adaptive, context-aware defense mechanisms to counter identity-based threats that are increasingly evading conventional protections,” researchers concluded.
Original Post url: https://hackread.com/russia-storm-2372-hit-mfa-bypass-device-code-phishing/
Category & Tags: Security,Cyber Attacks,Phishing Scam,Cyber Attack,Cybersecurity,MFA,Phishing,Russia,Scam,SOCRadar,Storm-2372 – Security,Cyber Attacks,Phishing Scam,Cyber Attack,Cybersecurity,MFA,Phishing,Russia,Scam,SOCRadar,Storm-2372
Views: 8