The Round-robin DNS is a load-balancing technique that helps manage traffic and avoid overloading servers. Multiple IP addresses are assigned to a single domain name; each time the domain name is resolved, the returned IP address is picked in a circular order.
The method aims to distribute the traffic load evenly between the servers associated with the IP addresses, so the service should be always fast and available.
How Does Round-Robin DNS Work?
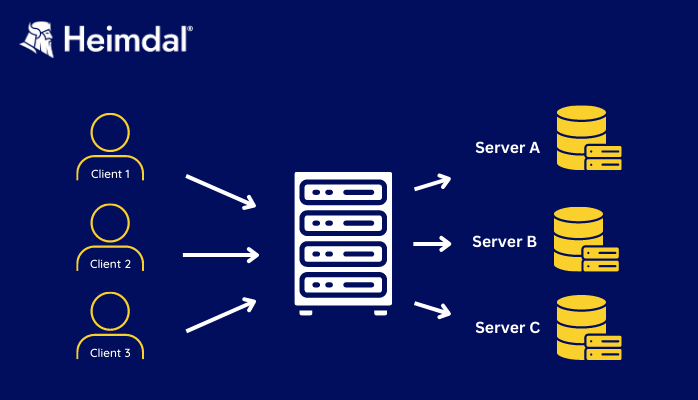
Instead of using a specific load-balancing item of hardware to distribute traffic, when using a Round-robin DNS, the balancing is done by an authoritative nameserver. This works if the website`s or the service`s content is hosted on several redundant web servers. A redundant server is a replica of a system that incorporates lines of communication and network devices. If the primary server goes down, it can act as the main operating system.
When repeatedly queried for an IP address, the DNS authoritative nameserver returns each time a different address. It picks those addresses in a rotational order:
- User no 1 makes a query for the example.com page and is pointed to the first IP address.
- User no 2 requests to access the example.com page and is taken to the second IP address.
- No 3 user asks to access example.com and is pointed to the third IP address.
- When user no 4 also makes a query for the example.com page he is sent to the first IP address. That is how the Round-robin algorithm goes.
A DNS server with a round-robin configuration has multiple different A records that point to the same domain name while displaying a different IP address. It operates in a loop. Each time it is queried, the DNS server sends the IP address it most recently answered with to the back of the line.
This way, the IP addresses in a round-robin DNS server work like the wheel spikes of a bike: each one gets to fall perpendicularly on the ground one after the other.
Why Use Round-Robin DNS?
Using round-robin DNS as a load-balancing technique is both simple to understand and configure. However, it is not an ideal one. This is because the round-robin algorithm doesn`t consider the server load or capacity. As a consequence, some of the clients might be directed to a server that is already overloaded.
Further on, let`s see which are the benefits and disadvantages of using Round-robin DNS to distribute requests across a group of servers.
Benefits:
- It`s easy to set up.
- It`s cost-effective, as there is no need for extra hardware or software.
- Each request is treated equally, according to the „first come, first served” principle, no matter whom the queries come from.
- It offers increased availability. If one of the servers goes down, it will automatically direct traffic to the other servers.
Disadvantages:
Unfortunately, Round-robin DNS also comes with a series of drawbacks.
- Uneven traffic distribution – Because of DNS caching and client-side caching, it doesn`t always succeed to evenly-distribute traffic. When a user makes a query to a high-traffic recursive resolver for a certain site, the resolver will cache the website’s IP and could continue to send a great amount of traffic to that one IP.
- No failure detection – If one of the servers goes offline, the algorithm continues to use it and direct queries to it. Usually, its A record has to be removed manually from the loop. Otherwise, each time traffic is directed to the fallen server, the unlucky user will be denied service.
- Equal priority – Each request being treated equally can also have its downsides. With the round-robin DNS technique, processes can’t be prioritized, no matter how important they are.
How Is Round-Robin DNS Used for Cyberattacks
Hackers leverage the Round-robin DNS load-balancing method for their fast flux evasion technique. Fast flux is a DNS-based avoidance technique that threat actors use to cover up their phishing and malware delivery sites.
Round-robin DNS enables them to associate multiple redundant web servers, that have distinct IP addresses, with a domain. To set up their fast flux obfuscation technique, attackers also set a very short TTL for these IP addresses. This way, once the TTL expires, the IP address in the cause will no longer be associated with that domain name. This gives the security team a harder time when trying to bring down malicious sites.
So, although it was not intended as a malicious tool, Round-robin DNS could also be used as one.


Antivirus is no longer enough to keep an organization’s systems secure.
Heimdal® Threat Prevention
– Endpoint
Is our next gen proactive shield that stops unknown
threats before they reach your system.
- Machine learning powered scans for all incoming online traffic;
- Stops data breaches before sensitive info can be exposed to the outside;
- Advanced DNS, HTTP and HTTPS filtering for all your endpoints;
- Protection against data leakage, APTs, ransomware and exploits;
Antivirus is no longer enough to keep an organization’s systems secure.
Heimdal® Threat Prevention
– Endpoint
Is our next gen proactive shield that stops unknown
threats before they reach your system.
- Machine learning powered scans for all incoming online traffic;
- Stops data breaches before sensitive info can be exposed to the outside;
- Advanced DNS, HTTP and HTTPS filtering for all your endpoints;
- Protection against data leakage, APTs, ransomware and exploits;
How Can Heimdal® Help?
91% of online threats are conducted through DNS. Threat actors use DNS attacks to spread malware or launch phishing campaigns. When their activities succeed, money and reputation losses are the results. Neglecting to keep up with modern methods always comes with a price. To be specific, in 2022, according to the IDC report, the average cost of a DNS attack was estimated to be $942,000.
Although hackers do their best to come up with new threats and obfuscation methods, the fight against cyber criminality is not lost, if you choose the right partner in cybersecurity. Heimdal`s Threat Prevention – Endpoint module is currently the best solution in the world to secure your machines without having to stop or slow down the workflow.
As part of this module, the DarkLayer Guard engine protects endpoints against malware, social engineering scams, and drive-by attacks. The product automatically filters all network packages based on DNS requests. DarkLayer Guard`s unique 2-way traffic filtering engine supports fully customizable white/black listing. When a malicious domain is found, the solution swiftly blocks network communication to mitigate Zero Hour exploits, Ransomware C&Cs, next-gen attacks, and data leakages.
Wrap Up
Round-robin DNS is one more example that hackers can leverage a totally legitimate tool or feature in harmful ways. While hackers use domain generation algorithms to enhance their chances to succeed and hide their footprints, security teams should also upgrade their prevention measures.
And if you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.
If you liked this post, you will enjoy our newsletter.
Get cybersecurity updates you’ll actually want to read directly in your inbox.





















































