Source: hackread.com – Author: Waqas.
February 2025 saw a record 126% surge in ransomware attacks, with Cl0p leading the charge. Hackers exploited file transfer flaws, infostealers, and AI-driven tactics, reveals Bitdefender’s latest Threat Debrief report.
Cybersecurity just reached a new milestone; and not in a good way. According to Bitdefender’s latest Threat Debrief report, February 2025 was the worst month in history for ransomware attacks, with a 126% increase in claimed victims compared to the same period last year.
This surprising jump saw the number of victims soar from 425 in February 2024 to a staggering 962 in February 2025. The massive surge in ransomware attacks occurred despite the United States-led alliance of 40 countries, announced in November 2023, aimed at dismantling ransomware gangs and their infrastructure. The initiative focused on disrupting payments, taking down infrastructure, and enhancing intelligence sharing.
Clop (Cl0p) Ransomware at Its Peak
According to Bitdefender’s report shared with Hackread.com ahead of publishing on Thursday, Cl0p ransomware group Clop was responsible for more than a third of the attacks, claiming 335 victims in just one month. This makes a 300% increase from the previous month.
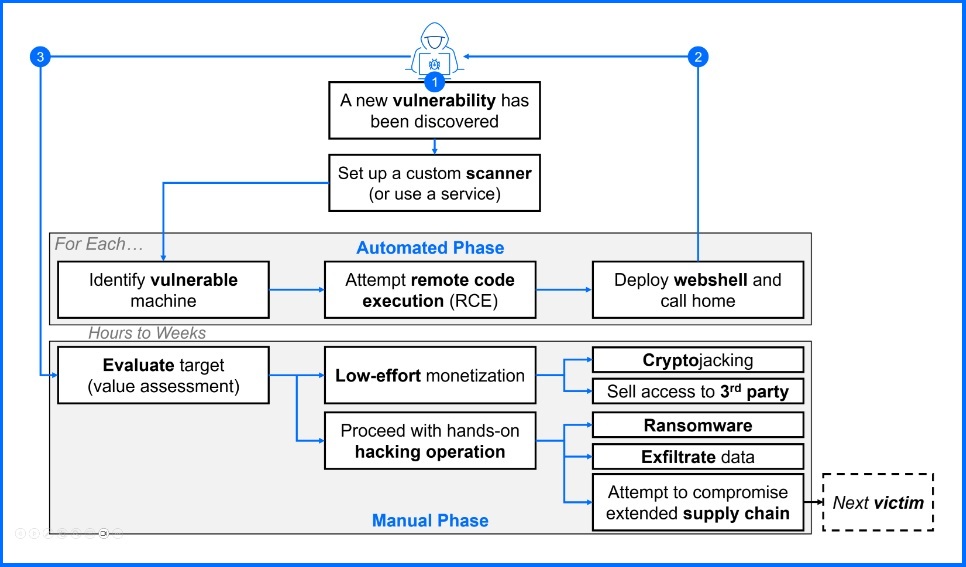
So, what’s behind this sudden rise in attacks? Cybersecurity experts point to a new trend that’s not so new: attackers are increasingly targeting vulnerabilities in edge network devices, such as file transfer systems and remote access tools.
Instead of focusing on specific industries, these opportunistic hackers are scanning the internet for easily exploitable flaws and launching automated attacks. For example, the Cl0p ransomware gang is notorious for exploiting vulnerabilities in MOVEit, a managed file transfer (MFT) software, with the highest frequency in 2023. The group stole so much data through MOVEit vulnerabilities that it launched a clearnet website to leak stolen information from victims worldwide.
In December 2024, Cl0p also announced exploiting security vulnerabilities in Cleo’s managed file transfer software, specifically targeting Cleo Harmony, VLTrader, and LexiCom products. Bitdefender’s Threat Debrief report also spotted Cl0p’s exploitation of Cleo vulnerabilities, especially CVE-2024-50623 and CVE-2024-55956 both rated 9.8 out of 10 in severity.
Both flaws allow attackers to execute commands remotely on compromised systems and were disclosed late last year. Despite patches being available, many organizations failed to update their systems in time, leaving them wide open to exploitation leading to the surge in victims seen in February 2025.
Other Notable Developments in the Ransomware World
Beyond the record-breaking numbers, Bitdefender researchers noticed several other noteworthy trends in February 2025 including:
FunkSec’s New Infostealer
FunkSec, a growing ransomware group, released Wolfer, a tool designed to extract sensitive information from infected machines. It communicates with a Telegram bot to gather system details, Wi-Fi passwords, and more.
A ransomware gang using infostealers is bad news, especially as researchers recently found that cybercriminals are successfully breaching U.S. national security with infostealers as cheap as $10. Even high-security institutions like the military and the FBI have had their systems compromised, with access being sold on the dark web.
Black Basta Gets Analyzed by AI
On February 11, 2025, the notorious Black Basta ransomware gang had its internal chats leaked. These chats contained over 200,000 Russian-language messages. Hudson Rock’s researchers created a chatbot called BlackBastaGPT to sift through the chat logs.
Insights revealed details about their profits, use of deepfake technology, and internal conflicts. The group’s leader emphasized avoiding detection by using built-in system tools, a tactic known as “living off the land.”
Ghost Ransomware Under Scrutiny
A joint advisory from CISA highlighted Ghost (also known as Cring), a China-based ransomware operation exploiting older but still unpatched vulnerabilities. Recommendations include patching affected software, segmenting networks, and backing up data regularly.
Akira’s Webcam Hack
The Akira ransomware gang found a creative way to bypass security by hijacking a victim’s webcam. Since the device ran Linux and wasn’t monitored closely, it became the perfect launchpad for encrypting files across the network undetected.
Stephen Kowski, Field CTO at Pleasanton, Calif.-based SlashNext Email Security+ commented on the latest development emphasizing the need to fix vulnerabilities by improving threat detection and response capabilities.
“We expect ransomware attacks to continue increasing this year, especially targeting healthcare, manufacturing, critical infrastructure, and supply chains. High-profile incidents in 2024 highlight the ongoing vulnerabilities,” warned Stephen. “To combat this, organizations need to focus on strengthening email security, implementing zero-trust architectures, and improving threat detection and response capabilities.”
Top 10 Companies Most Targeted by Ransomware Gangs
The United States, Canada, the UK, Germany, and other developed nations remain the biggest targets of ransomware groups. These countries are highly vulnerable due to their reliance on connected edge devices, cloud infrastructure, and critical business data.
In total, these are the top 10 companies most targeted by ransomware gangs:
- USA
- Canada
- The UK
- Germany
- France
- Australia
- Brazil
- Mexico
- Italy
- Sweden
For those looking to understand the full scope of modern ransomware operations and how to fight back, Bitdefender has published a comprehensive whitepaper detailing current attack methods and defence strategies. You can access it here.
Original Post url: https://hackread.com/ransomware-attacks-hit-record-high-in-february-2025/
Category & Tags: Cyber Crime,bitdefender,Cl0p,Cyber Attack,Cybersecurity,February,Infostealer,Ransomware – Cyber Crime,bitdefender,Cl0p,Cyber Attack,Cybersecurity,February,Infostealer,Ransomware
Views: 1




















































