Source: securityboulevard.com – Author: Bob Palmer
The Cyber Risk to the Healthcare Enterprise is Significant—and it’s Growing Due to Increased Connectivity of Medical Devices
Biomedical devices can be both a target for attack and a vector for the spread of an attack throughout the healthcare enterprise, and this is an increasingly important area of concern in both cybersecurity and healthcare leadership. Notable examples of cyberattacks on medical device networks include the WannaCry ransomware attack, which affected many hospital systems worldwide, including medical imaging equipment and networked devices. Studies have shown that MRIs and other computer-controlled imaging systems, as well as devices such as infusion pumps, smart ventilators, OR/anesthesiology devices, ICU bed devices, patient room devices, Lab environment/printers, and mobile cart devices, are susceptible to malware and unauthorized remote control when connected to insecure networks.
Potential Risks of a breach that affects the healthcare enterprise’s Internet-of-Medical-Things (IoMT) devices include:
- Patient Harm: Attackers could modify drug dosages or disable life-supporting functions.
- Data Breaches: Personal health information (PHI) can be stolen or sold on the dark web.
- Network Compromise: A compromised biomedical device can be a foothold to pivot into the hospital’s broader IT infrastructure, including the electronic medical records (EMR) systems.
Why Biomedical Devices Are Vulnerable
- Internet Connectivity and Wireless Features
Many modern biomedical devices, such as infusion pumps and cardiac telemetry devices, use wireless or Bluetooth technology for monitoring, diagnostics, and updates. These features, while convenient, also expand the attack surface. - Legacy Systems and Infrequent Updates
Many hospitals rely on older systems and equipment with outdated software, which are seldom patched for vulnerabilities. Once connected to the hospital network, these devices can become entry points for attackers. - Insufficient Security by Design
Biomedical devices often prioritize functionality and safety over cybersecurity. As a result, encryption, authentication, and access controls may be weak or absent. - Regulatory Gaps and Supply Chain Risks
Cybersecurity requirements for medical devices are evolving but often lag behind the pace of threats. Supply chain vulnerabilities in third-party components can also introduce hidden backdoors or flaws.
These vulnerabilities can lead to the successful breach of the enterprise network and the subsequent spread of the attack throughout the enterprise.
An Integrated Approach to Cyber Resilience for the Large Healthcare Enterprise
Large healthcare enterprises should address these risks by implementing device segmentation, network isolation, and vulnerability management for the medical devices in their enterprise landscape. These measures increase the cyber resilience of the enterprise by strictly controlling network traffic to prevent the spread of an attack, and by performing proactive vulnerability management on all devices to monitor and remediate misconfigurations and known vulnerabilities of devices. These measures prevent any breach of the healthcare network from spreading laterally throughout the environment, triggering a catastrophic interruption of clinical operations or malicious system encryption, leading to a ransomware demand.
ColorTokens and Claroty, two leading companies in the cybersecurity realm, have partnered to provide an integrated technological approach to achieving the goal of resilience in the medical enterprise. Claroty xDomeTM and ColorTokens XshieldTM work together to make the Internet of Medical Things (IoMT) and the larger healthcare IT infrastructure resilient to cyberattacks.
Access Forrester Wave Report | Know Why Forrester Rates us ‘Superior’ in OT, IoT, and Healthcare Security
Capabilities of the Integrated Solution
Claroty xDome for HealthcareTM is a leading technology that provides:
- Asset Inventory of all devices present in the diverse healthcare enterprise network
- Vulnerability Management for biomedical devices—identifying known configuration issues for devices from many different manufacturers
- Network Policy Recommendations to apply the right network security zone policies that incorporate clinical context and integrate with ColorTokens Xshield for enforcement of traffic policies
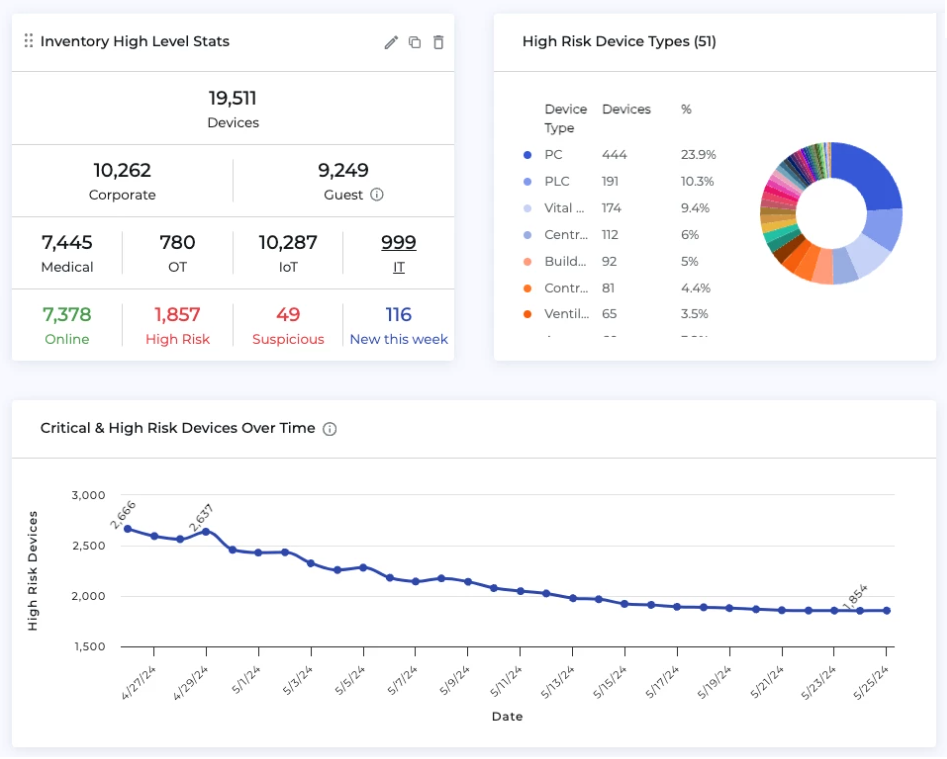
Fig. 1. The Claroty xDome for Healthcare Asset Inventory Dashboard
ColorTokens’ Xshield Enterprise Microsegmentation PlatformTM takes the asset inventory information, vulnerability details, and network zone recommendations from Claroty and:
- Enforces Network Microsegmentation policies that only allow in-policy traffic on the healthcare enterprise IT and IoMT networks, while stopping out-of-policy or malicious traffic. This prevents any breach of the healthcare network from spreading.
- Visualizes all Assets and Traffic for real-time monitoring of the healthcare enterprise landscape, with color-coded lines indicating in-policy and out-of-policy traffic
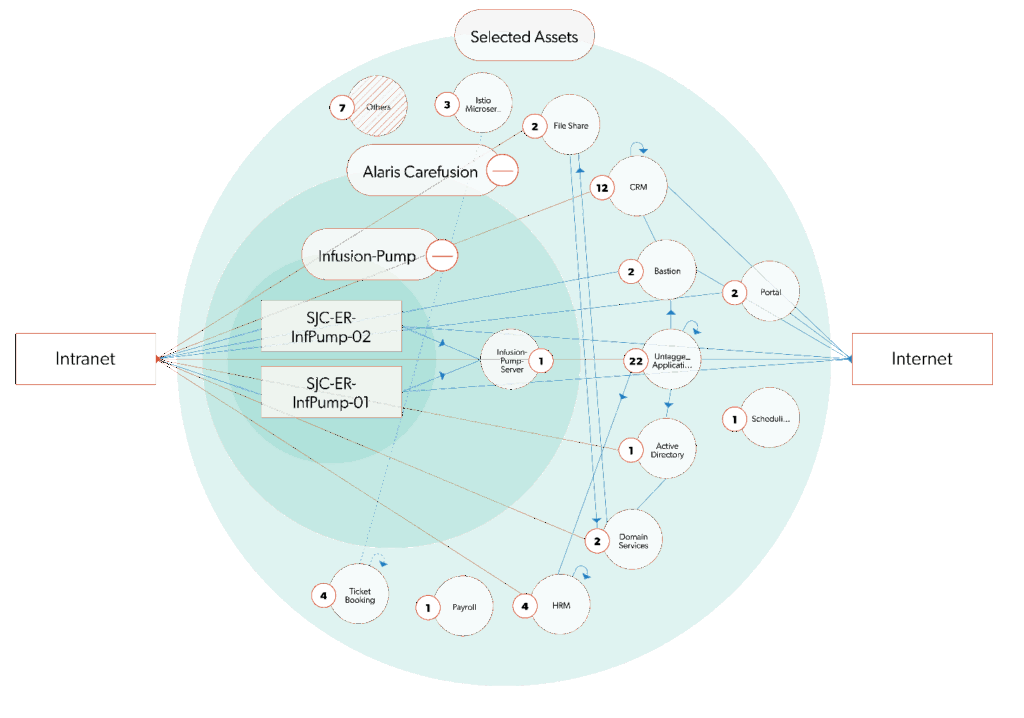
Fig. 2. The ColorTokens Xshield visualizer monitors the Enterprise Network Traffic
Together, ColorTokens Xshield and Claroty xDome provide critical capabilities to secure the large healthcare enterprise, including:
- Segmenting & isolating biomedical devices: Enforces traffic policies to and from devices to prevent the lateral spread of an attack, and isolates them in the event of a compromise
- Enabling dynamic inventories and classification of biomedical devices
- Identifying, ranking, and mitigating security vulnerabilities through agentless protection of devices
- Containing breaches to prevent the spread across devices within the isolated network and preventing lateral movement from the device network.
Features of the Integrated Approach to Cyber Resilience
Agentless Architecture: The combined solution does not require software agents to be installed on medical devices, has a minimal hardware requirement, and does not handicap network reliability or performance.
Device Monitoring: The integrated technology enables persistent monitoring of all devices within the “span of view” without any blind spots.
Online Asset Inventory: Claroty XDome delivers a real-time inventory of all biomedical assets within the scope of view.
Remote Policy Enforcement: ColorTokens Xshield applies security policies to devices with no lapse in enforcement, and without exposing patients to risk due to compromised capabilities of biomedical devices.
Threat Detection: Claroty detects and escalates threats based on known and unknown attack types with device vulnerability context.
Breach Detection and Containment: The combined solution provides real-time network traffic monitoring with visibility showing out-of-policy traffic, which can indicate an attack in progress.
Non-disruptive Implementation: Policy simulation and testing ensure non-disruptive implementation of cyber resilience, without “false positives” leading to interruption of patient care
Device Segmentation & Isolation: Medical devices are isolated when anomalous network behavior or a breach is detected, with programmatic alerting incorporated to enable clinical teams sufficient notice to permit the execution of contingency plans in the event of an attack.
The Value of the Combined Solution
Claroty XDome and ColorTokens Xshield’s integrated solutions assure security and clinical leaders that their healthcare enterprise landscape is resilient and can survive a cyberattack, quickly return to normal operations, comply with regulatory mandates for cybersecurity, and ensure continuity of patient care.
To speak with our expert solution team about how we can help you secure your healthcare enterprise landscape, you can schedule a meeting with us at www.ColorTokens.com/contact-us
The post Protecting Biomedical Devices in the Large Healthcare Enterprise appeared first on ColorTokens.
*** This is a Security Bloggers Network syndicated blog from ColorTokens authored by Bob Palmer. Read the original post at: https://colortokens.com/blogs/iomt-security-microsegmentation-healthcare/
Original Post URL: https://securityboulevard.com/2025/05/protecting-biomedical-devices-in-the-large-healthcare-enterprise/?utm_source=rss&utm_medium=rss&utm_campaign=protecting-biomedical-devices-in-the-large-healthcare-enterprise
Category & Tags: Security Bloggers Network,healthcare,integrations,ransomware protection,Vertical HCLS – Security Bloggers Network,healthcare,integrations,ransomware protection,Vertical HCLS
Views: 2






















































