Source: securityboulevard.com – Author: Laura Bruck
As the 2024 U.S. presidential election takes place, cybersecurity analysts are on high alert, warning of voter database leaks. They are warning of an increasingly complex landscape that could jeopardize voter data security and election integrity due to voter database leaks. The face-off between Kamala Harris and Donald Trump has intensified the focus on ensuring that electoral systems remain secure and resilient against potential cyberattacks.
It is crucial to protect against breaches, leaks, and disinformation campaigns that could influence public trust and democratic outcomes. Drawing insights from Constella Intelligence, this analysis examines the specific risks and incidents shaping the current election season.
U.S. Voter Data Leaks: A Persistent Threat
The United States has become a major target for voter data leaks, experiencing significant breaches that expose a wide range of personal information. Moreover, voter data from these breaches is being actively traded on deep and dark web forums, posing an ongoing risk to voter privacy and security.
Constella Intelligence’s findings show that U.S. voter data leaks account for approximately 78% of all voter data circulating on the dark web, underscoring the nation’s unique vulnerabilities stemming from its decentralized electoral system and vast voter data infrastructure. In the U.S. alone, 23 states have suffered data breaches, impacting regions nationwide and exposing significant weaknesses in the protection of sensitive voter information.
Key examples include Florida, Texas, Michigan, and Wisconsin. Given that there are 50 states in the United States, this means that approximately 46% of states have been affected by voter data breaches, reflecting the widespread and systemic nature of these vulnerabilities.
Notable incidents since 2020 illustrate the scope of these breaches:
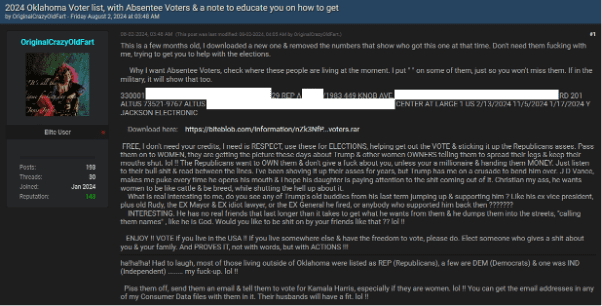
- Oklahoma: As shown in the previous image, a dark web forum post offered the 2024 Oklahoma voter list, including absentee voters, with instructions for accessing sensitive information for political purposes.
- Florida: Multiple significant leaks have affected Florida, including incidents in April 2020 and March 2022. These repeated exposures highlight the challenges in securing voter information in large states with complex voter registration systems and higher volumes of data, which increase their vulnerability to breaches.
- Wisconsin: A 2020 data leak compromised millions of voters, including such personal information as emails, names, phone numbers, and full addresses, showing how even isolated breaches can undermine public trust and voter security.
- Other States: States like Oklahoma, North Carolina, Pennsylvania, Michigan, Delaware, Texas, and Alaska have also reported leaks, some of which date back as far as 2013. These incidents highlight the systemic difficulties in securing voter data across state lines.
Of the 23 affected states, voter data breaches have impacted both Democratic and Republican strongholds, as well as crucial swing states, highlighting the widespread nature of the threat regardless of political affiliation or regional importance.
- Approximately 45% of Democratic-leaning states and 50% of Republican-leaning states have experienced data breaches.
- Key swing states (5%) such as Florida, Georgia, or Pennsylvania have also been impacted. Swing states are particularly important because they often decide the overall outcome of elections, making any breach in these regions potentially more impactful.
This broad geographic spread means that voters from both parties, along with undecided voters, could be affected, potentially impacting voter turnout and election trust.
Emerging Cyber Threats and Manipulation Risks in the 2024 Election
In addition to voter data leaks, other cybersecurity threats could impact the 2024 U.S. election, such as disinformation campaigns, targeted voter suppression, and foreign interference. Constella Intelligence has identified several notable cases:
- Campaign-Related Data Breaches (2024): A potential breach linked to Donald Trump’s campaign emails, allegedly involving foreign entities, exposed sensitive data. This underscores the risks posed by foreign influence operations.
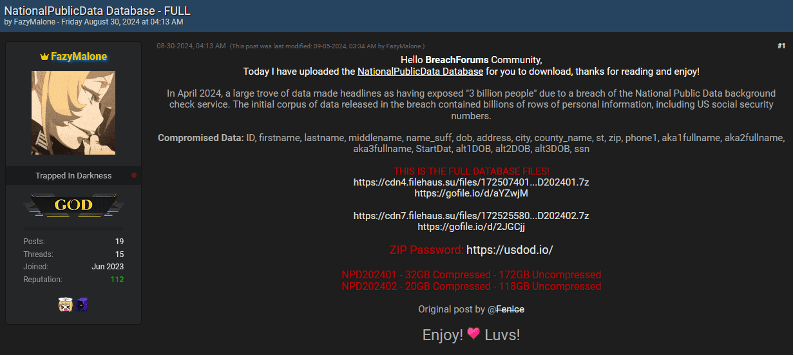
- National Public Data Leak (2024): A 2024 incident exposed million records, including sensitive information of million U.S. voters, highlighting ongoing vulnerabilities in protecting voter data.
- RNC Leak (2017): This breach affected millions of voters, exposing personal details like birth dates and political affiliations. The data was used in predictive models, suggesting a risk of similar information being exploited to manipulate voter perceptions in the 2024 race.
These breaches illustrate the persistent risks of data misuse, identity theft, and election manipulation, each capable of eroding public trust in the democratic process.
Global Perspective: Voter Data Leaks Beyond the United States
Although U.S. voter data leaks are the most prevalent, other nations have also experienced significant breaches, especially during election cycles. Notable examples include:
- Mexico: High-profile breaches occurred in 2017 and 2021, including targeted attacks on political organizations like the Partido Acción Nacional (PAN).
- Israel: The 2020 elections saw a significant voter data breach, illustrating vulnerabilities even in nations with advanced cybersecurity frameworks.
- The Philippines and India: The Philippines experienced a leak in 2016, and India faced a breach in 2024, demonstrating that populous democracies remain attractive targets for cybercriminals.
- Other Nations: Countries like Iraq, Honduras, and Ukraine have also reported voter data breaches, underscoring the global nature of these threats.
Impact and Risks: Manipulating Election Outcomes Through Exposed Voter Databases
Beyond data leaks, the risks extend to manipulation tactics that leverage this exposed information. When voter databases are exposed, the personal and political information they contain can be weaponized to manipulate election outcomes in various ways:
- Targeted Disinformation: Threat actors can use leaked data to send misleading messages, such as false voting locations or procedures, potentially causing voters to miss their opportunity to vote.
- Voter Suppression Tactics: Leaked data allows cyber actors to discourage specific voters from participating by sending intimidating or misleading messages.
- Identity Manipulation for Fraudulent Voting: Using personal details from leaked databases, malicious actors could impersonate registered voters to submit fraudulent ballots or alter voter rolls, causing confusion at polling stations.
- Amplifying Polarization: By leveraging insights into voter preferences, cyber actors can create messages that heighten political divisions, influencing voters through emotional manipulation rather than factual discourse.
These tactics threaten not only individual privacy but also the integrity of the election process. When personal information is exposed, it can be used to manipulate voters, distort their perceptions, and ultimately undermine the fairness of the election. This direct impact on voter behavior erodes confidence in democratic institutions and the legitimacy of the results.
Threat Narratives: Misinformation and Disinformation Linked to Voter Data Leaks
Disinformation narratives pose significant threats because they can manipulate public perceptions and erode trust in democratic institutions. Constella Intelligence has identified several such narratives that could shape public opinion on the Dark Web:
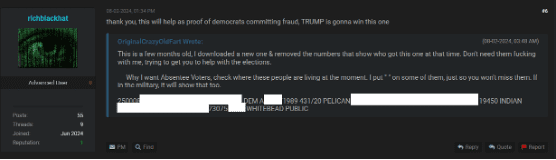
- Electoral Fraud: We have uncovered several threads discussing how leaked voter data could be used to manipulate voter intentions. Some threat actors allege the presence of ‘fake election officials’ in Pennsylvania, the removal of mailboxes in Luzerne County, and reports of ‘a box full of ballots’ discovered in Dade County, Florida. Additionally, claims about the purging of ineligible voters in Oklahoma, including deceased individuals, coupled with a previous voter list leak in the state, raise concerns about potential manipulation of the electoral system. These posts reflect the growing polarization among citizens and contribute to speculation around voter manipulation. However, we have not conducted further investigation into these claims.
- Political Corruption: False narratives also target political figures, especially Kamala Harris and the Obamas. Harris is accused of plagiarism in her criminal justice book and collaborating with foreign countries to spy on Trump.
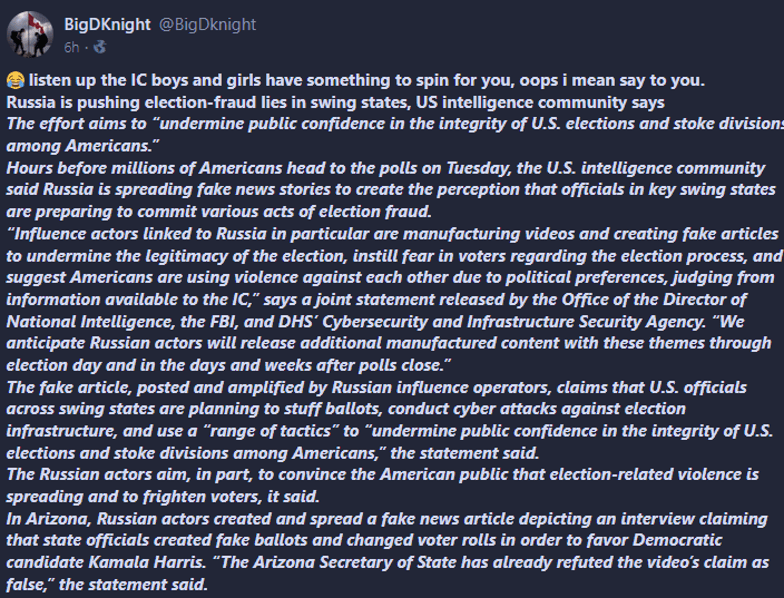
- Russian Disinformation Campaign: The U.S. intelligence community has reported that Russian actors could be actively spreading false information to undermine public confidence in the integrity of U.S. elections, especially in key swing states. This includes creating fake videos and articles suggesting election fraud, ballot stuffing, and cyber attacks in places like Arizona, targeting specific candidates such as Kamala Harris.
- Deep State: The idea of a ‘deep state’ aiming to control the country and silence opposition is frequently repeated. Steve Bannon, for example, is portrayed as a ‘political prisoner.’ Claims also suggest that this ‘deep state’ controls the media and censors information that could expose its actions.
- QAnon Conspiracy Theories: Some narratives align with QAnon conspiracy theories, such as mentions of ‘Agenda 47’ and references to Q. These theories, which speak of a satanic cabal controlling the world, are popular among some right-wing groups in the U.S. and often intersect with narratives about electoral fraud and political corruption.
These narratives significantly threaten democratic stability by promoting misinformation, eroding public trust, and influencing voter behavior. Data from voter databases could further be used to create targeted misinformation campaigns, aimed at voters who are already inclined to believe these narratives, thus deepening their impact on democratic processes.
Recommendations for Securing Voter Data and Upholding Electoral Integrity
In response to the rise in voter database breaches, Constella Intelligence recommends proactive measures for citizens to safeguard their data:
- Understand Your Digital Footprint: Stay informed about the personal information that is publicly accessible, including voter data and details from breaches like the NPD leak. By being aware of what information is exposed, you can take steps to protect yourself from threat actors who may attempt to exploit this data, especially during sensitive periods like Election Day.
- Enable Two-Factor Authentication (2FA): Strengthen account security by using 2FA, which makes unauthorized access more difficult.
- Be Mindful of Social Media Posts: Exercise caution with what you share or read on social media, as AI tools now make it easier than ever to create convincing fake content. Threat actors can exploit personal information or posts to manipulate narratives, spread disinformation, or target individuals during critical times like Election Day.
- Be Cautious of Phishing Attempts: On Election Day, be especially wary of unsolicited messages claiming to provide election updates or voter information. Avoid clicking on links or downloading attachments, as scammers frequently use these tactics to steal personal data or spread disinformation during critical events like elections.
Stay vigilant against potential threats, from voter data breaches to disinformation, and take steps to protect your personal information. As you head to the polls, remember the importance of safeguarding our democratic process. Enjoy your Election Day, and best wishes to you all, America!
*** This is a Security Bloggers Network syndicated blog from Constella Intelligence authored by Laura Bruck. Read the original post at: https://constella.ai/2024-u-s-election-voter-database-leaks/
Original Post URL: https://securityboulevard.com/2024/11/potential-cybersecurity-threats-to-the-2024-u-s-election-voter-database-leaks/
Category & Tags: Security Bloggers Network,Threats & Breaches,Blog,breaches,US election,voter database leaks – Security Bloggers Network,Threats & Breaches,Blog,breaches,US election,voter database leaks
Views: 4





















































