Source: securityaffairs.com – Author: Pierluigi Paganini

PumaBot targets Linux IoT devices, using SSH brute-force attacks to steal credentials, spread malware, and mine crypto.
Darktrace researchers discovered a new botnet called PumaBot targets Linux-based IoT devices, using SSH brute-force attacks to steal credentials, spread malware, and mine cryptocurrency.
PumaBot skips broad internet scans and instead pulls a list of targets from its C2 server to brute-force SSH logins. Once in, it runs remote commands and sets up persistence by creating system service files. Researchers analyzed its core features and related binaries to better understand the campaign.
PumaBot is a Go-based botnet that brute-forces SSH credentials from IPs fetched via its C2 server to spread and maintain access. After login, it deploys itself, collects system info, and sends it back in JSON format with a unique header. It hides in /lib/redis, creates a fake systemd service, and adds SSH keys to maintain persistence. The malware runs cryptominers like xmrig, and related binaries, like ddaemon and networkxm, support its campaign by enabling updates and further brute-force activity.
“The malware begins by retrieving a list of IP addresses of likely devices with open SSH ports from the C2 server (ssh.ddos-cc[.]org) via the getIPs() function. It then performs brute-force login attempts on port 22 using credential pairs also obtained from the C2 through the readLinesFromURL(), brute(), and trySSHLogin() functions.” reads the report published by Darktrace. “Within trySSHLogin(), the malware performs several environment fingerprinting checks. These are used to avoid honeypots and unsuitable execution environments, such as restricted shells.”
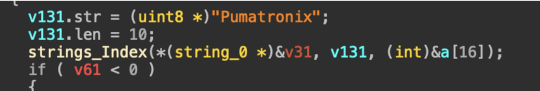
The malware uses smart evasion tactics during its SSH brute-force process. It checks the environment to avoid honeypots or restricted systems and looks specifically for the term “Pumatronix,” a maker of surveillance and traffic cameras, hinting at IoT targeting or an attempt to bypass certain devices.
“Notably, the malware checks for the presence of the string “Pumatronix”, a manufacturer of surveillance and traffic camera systems, suggesting potential IoT targeting or an effort to evade specific devices.” states the report.

If the system passes these checks, PumaBot collects system info, sends it to its C2 server, and hides itself as a fake Redis file with a persistent systemd service.
The researchers also discovered additional related binaries, suggesting the bot is part of a larger, coordinated campaign targeting Linux systems.
Concluding, the botnet poses a persistent SSH threat by brute-forcing credentials, mimicking legit tools like Redis, and using systemd for stealthy persistence. Its fingerprinting helps evade honeypots, and while not fully self-propagating, its worm-like behavior reveals a semi-automated campaign aimed at compromising devices and maintaining long-term access.
“The botnet represents a persistent Go-based SSH threat that leverages automation, credential brute-forcing, and native Linux tools to gain and maintain control over compromised systems.”concludes the report. “While it does not appear to propagate automatically like a traditional worm, it does maintain worm-like behavior by brute-forcing targets, suggesting a semi-automated botnet campaign focused on device compromise and long-term access.”
To protect against threats like this botnet, monitor for unusual SSH login patterns, especially many failed attempts from different IPs. Regularly audit systemd services for suspicious entries, like oddly named ones (e.g., mysqI.service) or binaries stored in strange locations such as /lib/redis. Check for unknown SSH keys in authorized_keys files, and watch for outbound HTTP requests with odd headers (like X-API-KEY: jieruidashabi), which may signal botnet activity. Finally, secure SSH access by limiting exposure of port 22 with strict firewall rules.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, malware)
Original Post URL: https://securityaffairs.com/178386/malware/pumabot-targets-linux-iot-devices.html
Category & Tags: Breaking News,Cyber Crime,Internet of Things,Malware,botnet,Cybercrime,Hacking,hacking news,information security news,IoT,IT Information Security,malware,Pierluigi Paganini,PumaBot,Security Affairs – Breaking News,Cyber Crime,Internet of Things,Malware,botnet,Cybercrime,Hacking,hacking news,information security news,IoT,IT Information Security,malware,Pierluigi Paganini,PumaBot,Security Affairs
Views: 2