Source: hackread.com – Author: Deeba Ahmed.
KEY SUMMARY POINTS
- Targeted Attacks: Sophisticated spear phishing campaigns are increasingly targeting corporate executives via mobile devices, using social engineering tactics.
- Exploitation of Trust: Attackers mimic legitimate services like DocuSign and Google, leveraging urgency and credibility to deceive victims.
- Advanced Techniques: Campaigns use CAPTCHAs, mobile-specific fake login pages, and compromised domains to bypass detection mechanisms.
- Infrastructure Abuse: Attackers utilize platforms like Cloudflare for SSL encryption and DDoS protection, complicating detection efforts.
- Proactive Defense: Regular employee training, advanced mobile device management (MDM) solutions, and automated incident response platforms are critical to mitigating these threats.
Mobile devices have become a prime target for sophisticated phishing attacks, particularly those aimed at corporate executives. These targeted attacks, known as spear phishing, leverage social engineering tactics to steal valuable credentials and gain access to sensitive information.
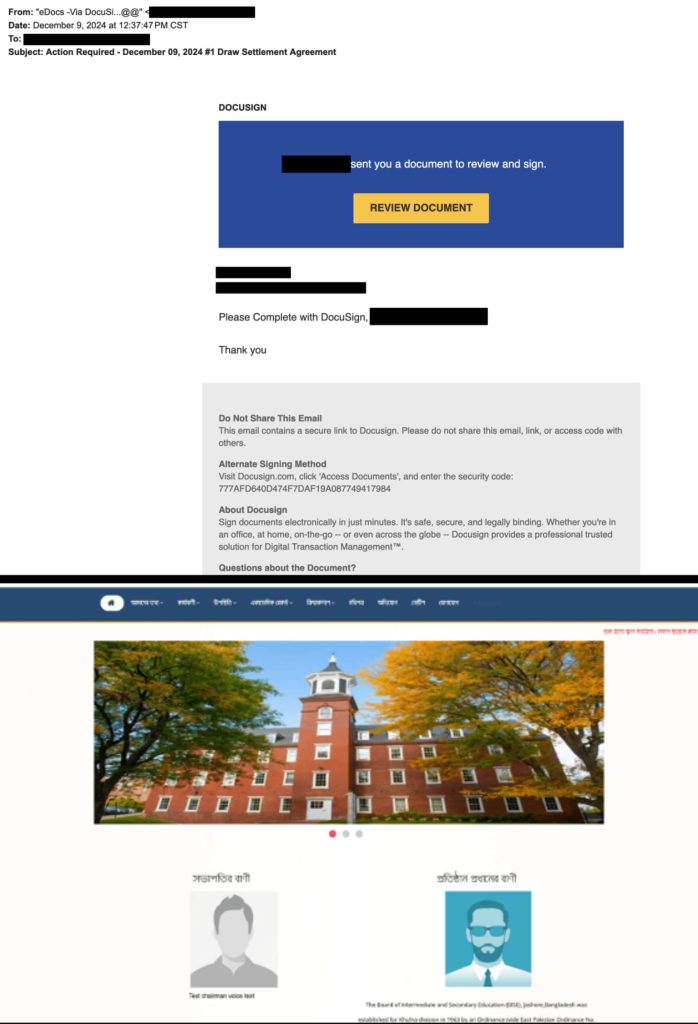
The Phishing and Data Analytics Team at Zimperium uncovered a recent spear phishing campaign targeting executives. The attack involves using a mimicked legitimate DocuSign document requiring immediate review, a common tactic that exploits urgency and authority.
Spear phishing is a popular attack vector against corporate executives, compromising high-value credentials that grant access to sensitive data and systems. The attack begins with a seemingly innocent link disguised as a DocuSign document. The link used a legitimate domain (clickmethryvcom) to mask its origin, and once clicked initiates a series of redirects. First, it redirects to a compromised university website, leveraging its credibility to bypass detection.
Researchers noted that attackers have used CAPTCHAs to prevent automated detection and implemented mobile-specific targeting. Moreover, if the link is accessed via a mobile device, the attack presents a fake Google sign-in page to steal credentials whereas desktops are redirected to legitimate Google sites. Another observation is that the phishing site (diitalwaveru) and its SSL certificate were created just days before the attack, highlighting the attackers’ focus on rapid deployment.
Further probing as per Zimperium’s blog post, revealed that the attackers had utilized Cloudflare’s infrastructure for DDoS protection, SSL encryption, and fast content delivery, making it harder to detect. And, in addition to email-based attacks, the campaign also used PDF documents containing embedded phishing URLs. These PDFs mimicked legitimate DocuSign workflows, bypassing traditional URL scanning and exploiting trust in business documents.
The incident highlights the evolving nature of mobile phishing attacks, with attackers investing heavily in infrastructure to bypass security controls, targeting mobile devices often overlooked in security strategies, and exploiting compromised domains for credibility.
Therefore, it has become essential to conduct regular security awareness training programs to educate employees about the latest phishing tactics and best practices for identifying and avoiding such attacks. Organizations must also deploy advanced Mobile Device Management (MDM) solutions to enforce security policies, such as password complexity, screen lock timeouts, and remote wipe capabilities.
Mika Aalto, Co-Founder and CEO at Hoxhunt weighed in on the situation emphasizing the importance of proactive training for employees and management to identify and report phishing attacks, as technical tools alone may not catch all threats.
“The most important thing that companies can do is to shift left and equip senior management and employees with the skills and tools to recognize and safely report a mobile phishing (mishing) attack. We can hope that technical filters and endpoint detection and response technologies quickly develop to be able to pick up these highly obfuscated, native code-based Malware attacks and pinpoint irregular signals and traffic,“ said Mika.
“Ultimately, it comes down to people. Attackers will launch a complex attack with what might just be a simple phishing message. It’s up to people to be able to listen to that little voice in their head that is telling them that something is wrong and report suspicious messages as a matter of habit. From there, you want to have a platform that will automatically categorize and escalate their reports to the SOC for accelerated response,“ he explained.
- 99% of UAE’s .ae Domains Exposed to Phishing and Spoofing
- Scammers Exploit Fake Domains in Dubai Police Phishing Scams
- Ongoing Phishing Attack Targets Employees Across 12 Industries
- Rockstar 2FA Phishing-as-a-Service Kit Hits Microsoft 365 Accounts
- Xiū gǒu Phishing Kit Hits UK, US, Japan, Australia Across Key Sectors
Original Post url: https://hackread.com/mobile-phishing-executives-fake-docusign-links/
Category & Tags: Security,Phishing Scam,Cyber Attack,Cybersecurity,DocuSign,Fraud,Phishing,Scam,SMSishing – Security,Phishing Scam,Cyber Attack,Cybersecurity,DocuSign,Fraud,Phishing,Scam,SMSishing
Views: 3