Source: securityaffairs.com – Author: Pierluigi Paganini
Researchers warn of a new ransomware family called CACTUS that exploits known vulnerabilities in VPN appliances to gain initial access to victims’ networks.
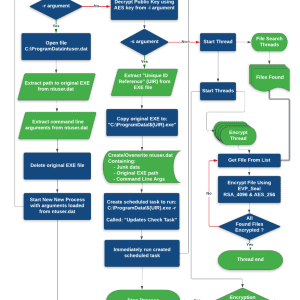
Researchers from cybersecurity firm Kroll have analyzed on a new ransomware family called CACTUS that has been spotted exploiting known flaws in VPN appliances to achieve initial access to targeted networks.
The new ransomware operation has been active since March 2023, despite the threat actors use a double-extortion model, their data leak site has yet to be discovered.
The new ransomware strain outstands for the use of encryption to protect the ransomware binary. BleepingComputer, which received a copy of the report from Kroll, said that the threat actor uses a batch script to obtain the encryptor binary using 7-Zip.
The binary is deployed using a specific flag that allows its execution, while the ZIP archive is removed. This technique allows the encryptor to avoid detection.
“CACTUS essentially encrypts itself, making it harder to detect and helping it evade antivirus and network monitoring tools,” Laurie Iacono, Associate Managing Director for Cyber Risk at Kroll, told Bleeping Computer. “This new ransomware variant under the name CACTUS leverages a vulnerability in a popular VPN appliance, showing threat actors continue to target remote access services and unpatched vulnerabilities for initial access.”
Once gained access to the network, the ransomware operators used a scheduled task to maintain persistence via an SSH backdoor.
Cactus ransomware uses the SoftPerfect Network Scanner (netscan) to look for other targets on the network along with PowerShell commands to enumerate endpoints. The ransomware identifies user accounts by viewing successful logins in Windows Event Viewer, it also uses a modified variant of the open-source PSnmap Tool.
The Cactus ransomware relies on multiple legitimate tools (e.g. Splashtop, AnyDesk, SuperOps RMM) to achieve remote access and uses Cobalt Strike and the proxy tool Chisel in post-exploitation activities.
Once escalated the privileges on a machine, the threat actors use a batch script to uninstall popular antivirus solutions installed on the machine.
Cactus uses the Rclone tool for data exfiltration and used a PowerShell script called TotalExec, which was used in the past by BlackBasta ransomware operators, to automate the deployment of the encryption process.
At this time is still unclear if the decryptor provided by the ransomware operators to the victims that have paid the ransom is reliable.
We are in the final!
Please vote for Security Affairs (https://securityaffairs.com/) as the best European Cybersecurity Blogger Awards 2022 – VOTE FOR YOUR WINNERS
Vote for me in the sections where is reported Securityaffairs or my name Pierluigi Paganini
Please nominate Security Affairs as your favorite blog.
Nominate Pierluigi Paganini and Security Affairs here here: https://docs.google.com/forms/d/e/1FAIpQLSepvnj8b7QzMdLh7vWEDQDqohjBUsHyn3x3xRdYGCetwVy2DA/viewform
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, CACTUS Ransomware)
Original Post URL: https://securityaffairs.com/145960/malware/new-cactus-ransomware.html
Category & Tags: Breaking News,Cyber Crime,Malware,Security,CACTUS,Cybercrime,Hacking,hacking news,information security news,IT Information Security,malware,Pierluigi Paganini,ransomware,Security Affairs,Security News – Breaking News,Cyber Crime,Malware,Security,CACTUS,Cybercrime,Hacking,hacking news,information security news,IT Information Security,malware,Pierluigi Paganini,ransomware,Security Affairs,Security News