Source: heimdalsecurity.com – Author: Vladimir Unterfingher
A recent Microsoft update has unexpectedly forced several organizations to upgrade from Windows Server 2022 to Windows Server 2025, resulting in unexpected licensing demands and operational setbacks.
First reported on November 5, 2024, this incident has affected organizations worldwide and sparked frustration across industry forums as customers grapple with disrupted systems and unexpected costs.
What Caused the Forced Upgrades?
The issue stems from Microsoft update KB5044284, released on October 8, 2024, as a standard patch for Windows Server 2022 users.
For users who had opted into a specific update category, this patch unexpectedly triggered a full upgrade to Windows Server 2025.
Critically, Microsoft failed to conduct a prior licensing check, which has left users unexpectedly needing to purchase new Server 2025 licenses to keep their systems operational.
In plain terms, it shouldn’t be possible to upgrade a server, without having the appropriate licensing first, to ensure that operations are smoothly transitioning.
Microsoft has since halted these forced upgrade prompts through Windows Update, but many organizations are already experiencing disruptions in system stability and compatibility with applications designed for Windows Server 2022.
Microsoft pushing the upgrade
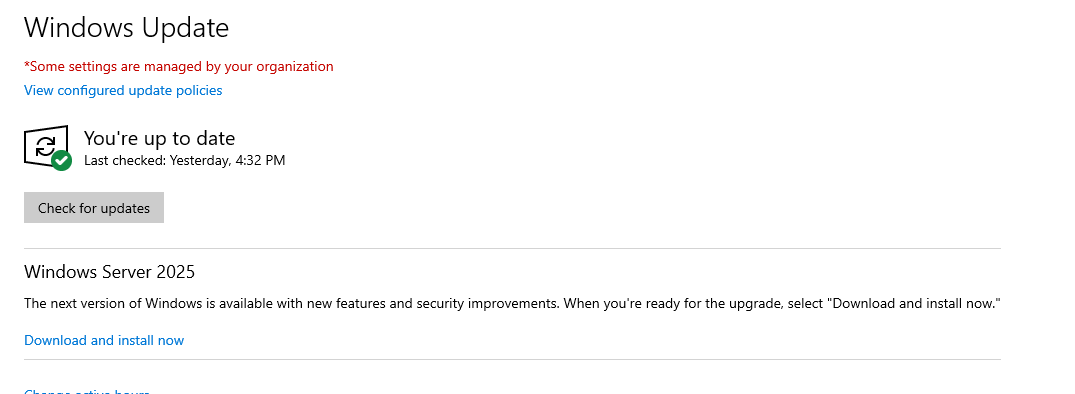
Heimdal smoke-testing the Windows Server 2022 versioning.
Microsoft rescinding the upgrade
Heimdal second smoke-test of Windows Server 2022 versioning.
Operational and Licensing Challenges
This unplanned upgrade has left IT teams facing several issues. Many systems upgraded to Windows Server 2025 are now incompatible with applications built for Windows Server 2022, resulting in operational downtime and added maintenance burdens.
On top of this, organizations now need Server 2025 licenses to continue operations on the new system, an unexpected cost that wasn’t accounted for in their budgets.
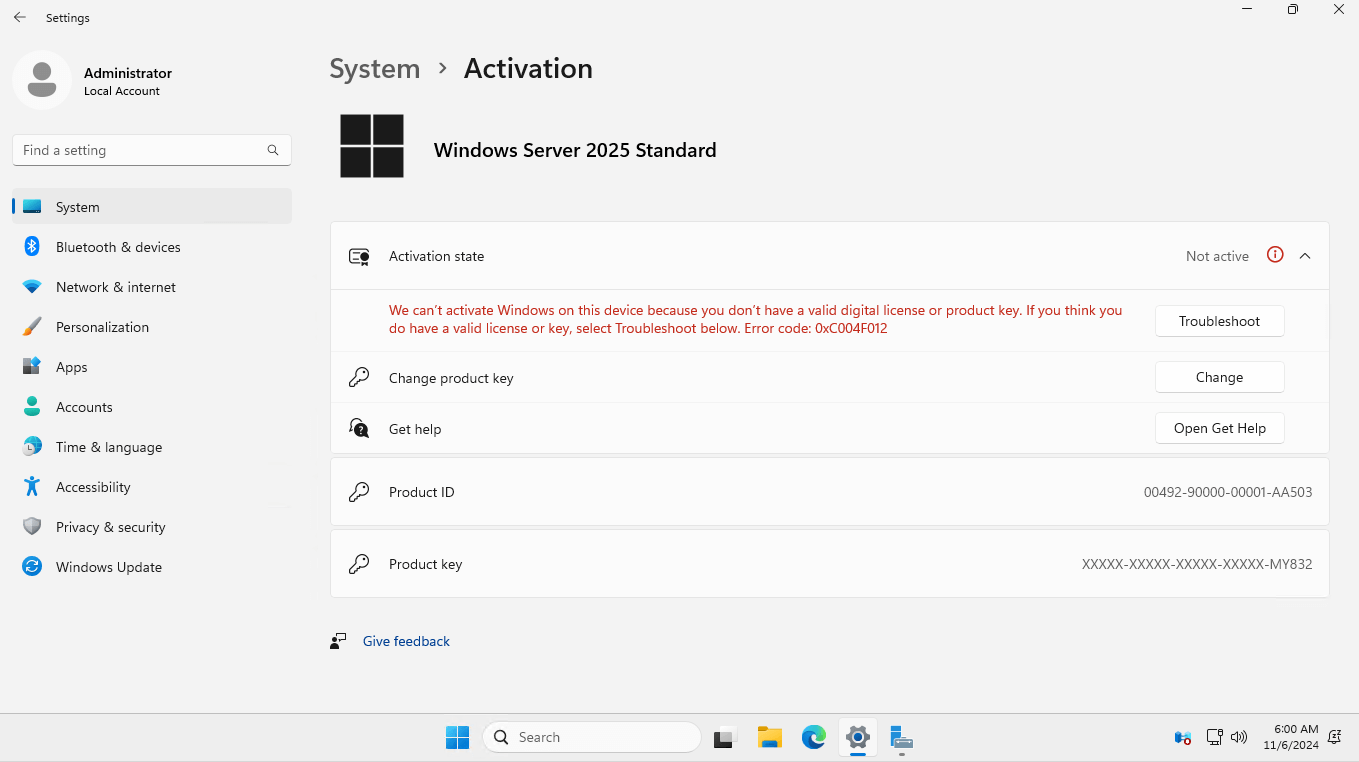
Post-upgrade screen for license updating.
Heimdal’s Founder and Chairman, Morten Kjaersgaard, explained the disruptive nature of these forced upgrades:
The Microsoft Server 2025 migration was automatic, before retracting the update, which is risky, considering the impact on customers, especially from potential downtime. On top of that, the licensing check for Server 2025 only happens after the upgrade, adding further risk for end users. In essence, you’re compelled to pay for a new license after the upgrade, with little chance to roll back.
Kjaersgaard likened the process to a troubling scenario for car owners:
Imagine if your electric car—say, a Tesla—received an automatic software update, but you couldn’t drive on the new version until you entered your credit card details to pay the full MSRP once again for the upgrade. Things could easily go south if an OS upgrade occurred while cruising on a busy highway (…)
Data and Recovery Implications
For organizations lacking regular backups or system images, this forced upgrade also poses significant data recovery risks.
Since the upgrade is irreversible without a “bare metal restore”—a complex reinstallation process involving the operating system, applications, and data—administrators are left scrambling to restore systems to previous configurations, a time-consuming and costly endeavor.
Heimdal®’s Reaction
Heimdal’s response post investigation, meant that the damage was limited to only 86 customers, by blocking the KB5044284 upgrade on servers.
Recommendations for Preventing Future Incidents
Considering this recent incident, Heimdal recommends that IT administrators adopt the following practices to safeguard their environments against similar events:
- Disable Automatic Updates: Turn off automatic updates in server environments to prevent unauthorized upgrades.
- Implement Multi-Approval Processes: Enforce strict, multi-level approval for critical updates to ensure no major system changes occur without oversight.
- Regularly Back Up Systems: Consistently perform backups or snapshots to enable a rapid rollback if issues arise with updates.
Heimdal’s Long-Term Safeguards
In response to this incident, Heimdal announced adjustments to its patch management repository to prevent similar disruptions from being injected into its ecosystem.
Going forward, Heimdal will separate upgrade patches from routine updates, allowing administrators to control whether upgrades are applied automatically or manually, despite being pushed by Microsoft.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.
Experienced blogger with a strong focus on technology, currently advancing towards a career in IT Security Analysis. I possess a keen interest in exploring and understanding the intricacies of malware, Advanced Persistent Threats (APTs), and various cybersecurity challenges. My dedication to continuous learning fuels my passion for delving into the complexities of the cyber world.
Original Post URL: https://heimdalsecurity.com/blog/microsoft-windows-server-2025-upgrade/
Category & Tags: Patch management – Patch management
Views: 0




















































