Source: heimdalsecurity.com – Author: Cristian Neagu
Microsoft believes that Microsoft Teams chats were used into coaxing users to share their credentials with threat actors. The available evidence leads to a Russian government-linked hacking group known as Midnight Blizzard being responsible, after taking aim at dozens of global organizations with a campaign to steal login credentials by engaging users in Teams chats, pretending to be from technical support.
Since late May, “fewer than 40 unique global organizations” have been impacted by these “highly targeted” social engineering attacks, according to Microsoft researchers, who also stated that the company was looking into the matter.
The organizations targeted in this activity likely indicate specific espionage objectives by Midnight Blizzard directed at government, non-government organizations (NGOs), IT services, technology, discrete manufacturing, and media sectors.
Microsoft (Source)
The Midnight Blizzard Microsoft Teams Attack Explained
According to the researchers, the hackers created identities and domains that appeared to be technical support departments in an effort to speak with Teams users and convince them to accept multifactor authentication (MFA) prompts.
Using infected Microsoft 365 tenants, the attackers built new domains with a technical help theme. These new domains were a component of the ‘onmicrosoft.com’ domain, a valid Microsoft domain that Microsoft 365 uses automatically as a fallback in the event that a custom domain is not generated.
Step 1: Teams Request to Chat
A Microsoft Teams message request from a third-party user posing as a technical support or security team may be sent to the target user.
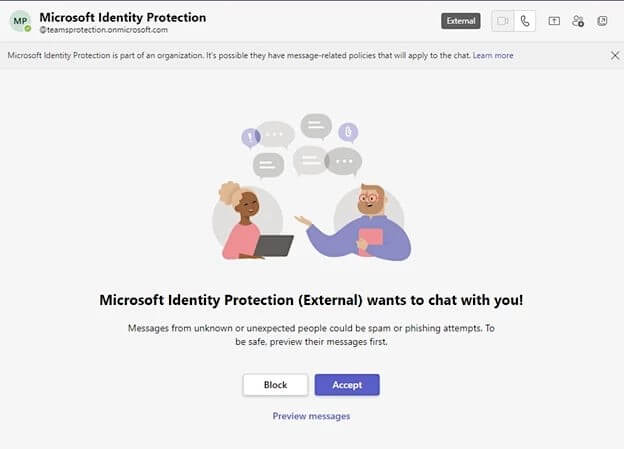
Midnight Blizzard’s Phishing Message on Teams (Source)
Step 2: Request Authentication App Action
The attacker then sends the target user a Microsoft Teams message in an effort to persuade them to enter a code into the Microsoft Authenticator app on their mobile device if they agree to the message request.
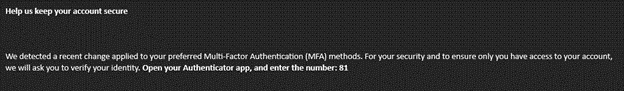
Microsoft Teams Prompt With a Code and Instructions (Source)
Step 3: Successful MFA Authentication
The threat actor is given a token to authenticate as the targeted user if the targeted user accepts the message request and enters the code into the Microsoft Authenticator app. After completing the authentication process, the actor is granted access to the user’s Microsoft 365 account.
Following the compromise, the attacker carries out post-compromise activities, which frequently entail information theft from the affected Microsoft 365 tenant. In some instances, the actor tries to add a device to the organization as a managed device using Microsoft Entra ID (formerly Azure Active Directory), probably in an effort to get around conditional access controls set up to only allow managed devices to access certain services.
Microsoft’s Recommendations on How to Reduce The Risks
To help Teams users reduce the risk of this threat, Microsoft posted a series of recommendations to follow:
- Pilot and start deploying phishing-resistant authentication methods for users;
- Implement Conditional Access authentication strength to require phishing-resistant authentication for employees and external users for critical apps;
- Specify trusted Microsoft 365 organizations to define which external domains are allowed or blocked to chat and meet;
- Keep enabled the Microsoft 365 auditing so that audit records could be investigated if required;
- Select and understand what are the best access settings for external collaboration for your organization;
- Allow access only to known devices that adhere to Microsoft’s recommended security baselines;
- Educate your employees about social engineering and credential phishing attacks, including refraining from entering MFA codes sent via any form of unsolicited messages;
- Users of Microsoft Teams should be instructed not to provide their account details or consent to sign-in requests over chat and to always check the ‘External’ tag on communications from other sources;
- Educate users to review sign-in activity and mark suspicious sign-in attempts as “This wasn’t me”.
Not a First for Midnight Blizzard or APT29
This is not the first time the Russian-sponsored threat group entered the public light. Three years ago, the SolarWinds supply-chain attack that resulted in the hacking of numerous U.S. federal agencies was planned and carried out by Midnight Blizzard (also known as APT29), the hacking unit of the Russian Foreign Intelligence Service (SVR).
Since that incident, this group has also gained access to the networks of other businesses employing covert malware, such as TrailBlazer and a GoldMax Linux backdoor variant, which allowed them to go unnoticed for years.
Additionally, the group was also behind a series of phishing campaigns, explicitly targeting governments, embassies, and high-ranking officials throughout Europe.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube for more cybersecurity news and topics.
Original Post URL: https://heimdalsecurity.com/blog/microsoft-teams-users-targeted-by-russian-threat-group/
Category & Tags: Cybersecurity News – Cybersecurity News




















































