Source: www.infosecurity-magazine.com – Author:
Public-facing instances of ProjectSend, an open-source file-sharing web application, have been exploited by attackers, according to vulnerability intelligence provider VulnCheck.
ProjectSend was created by software developer Ignacio Nelson and is maintained by a group of over 50 people. It has received support from 1500 people on GitHub.
The web application has been affected by an improper authentication vulnerability since at least January 2024, when cybersecurity firm Synactiv reported it to the project maintainers.
Exploiting this vulnerability allows attackers to enable unauthorized modification of the application’s configuration by remotely sending crafted HTTP requests to options.php. This can enable them to create accounts, upload webshells and embed malicious JavaScript.
The flaw was patched in May and ProjectSend released an official patch version in August.
However, no CVE was allocated to the vulnerability, meaning that users did not know how critical it was.
Since the patch release, multiple exploits have been published by Synactiv, Project Discovery (using Nuclei), and Rapid7 (using Metasploit).
In November, VulnCheck noticed that many public-facing ProjectSend instance servers had started changing their landing page titles to long, suspicious-looking strings.
Upon investigating where this abnormal behavior came from, VulnCheck concluded that attackers actively intended to exploit the vulnerability.
VulnCheck, a CVE numbering authority, allocated a CVE number to the vulnerability, CVE-2024-11680.
It also assigned a CVSS score of 9.8, meaning the vulnerability is highly critical.
The VulnCheck Initial Access team developed a scanner to fingerprint the versions of ProjectSend internet-facing systems. It found that only 1% of users were using the patched version (r1750).
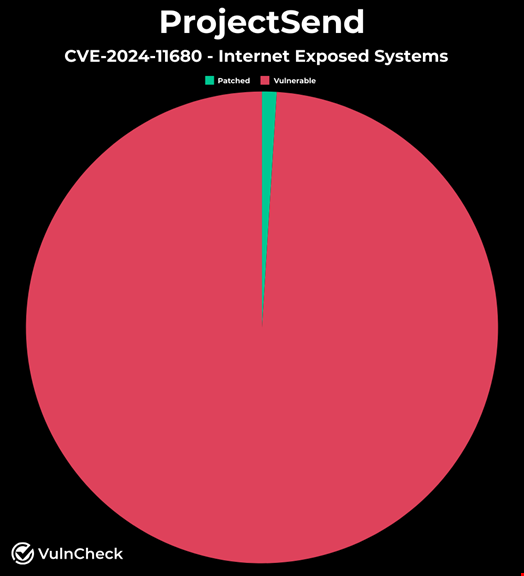
“Given the timeline, evidence of exploitation and lack of patch adoption, we assume that exploitation is likely widespread. And if not now, then in the near future considering the abysmal patching rates,” the VulnCheck researchers added in a blog post.
Read now: Navigating the Vulnerability Maze – Understanding CVE, CWE, and CVSS
Original Post URL: https://www.infosecurity-magazine.com/news/exploit-projectsend-critical/
Category & Tags: –
Views: 2




















































