Source: securityboulevard.com – Author: Devesh Patel
Introduction: The Identity Crisis You Don’t Know You’re Having
Imagine this scenario: Your company just acquired a promising startup, adding 200 new employees overnight. Your CIO announces they need access to 15 different systems by Monday. Your security team is simultaneously tracking three former employees whose accounts were never properly deactivated—across dozens of applications—creating significant security vulnerabilities. Meanwhile, your compliance officer is demanding documentation of all access permissions for next week’s audit.
Welcome to the modern identity crisis.
In today’s hyper-connected enterprise environments, managing identities has become the digital equivalent of herding cats—chaotic, frustrating, and seemingly impossible. Studies show the average enterprise now manages over 950 distinct applications, with a typical employee requiring access to 15-25 systems. Each manual provisioning action takes 30+ minutes and costs organizations approximately $70 per user action.
The problem is so pervasive that Gartner estimates 70% of all security breaches now originate from mismanaged identities and access permissions.
What if there was a standardized, elegant solution to this chaos—a universal “identity language” that could seamlessly synchronize user information across your entire technology ecosystem?
Enter SCIM—the System for Cross-domain Identity Management—the protocol silently revolutionizing how forward-thinking organizations handle identity. In this comprehensive guide, we’ll peel back the layers of this powerful standard to reveal how it works, why it matters, and how it’s transforming enterprise identity management.
What is SCIM?
SCIM is an open standard protocol (RFC 7643 and RFC 7644) designed to simplify user identity management tasks across different domains and systems. At its core, SCIM provides a defined schema and API for managing identities, with these key characteristics:
- REST-based: Built on REST architecture principles using JSON as its primary data format
- Schema-driven: Uses a standardized schema for consistent representation of users and groups
- Cross-domain: Designed specifically for managing identities across organizational boundaries
- Automation-focused: Enables automated provisioning and deprovisioning workflows
SCIM addresses the fundamental question: “How can we efficiently move identity data between systems that might have different data models and capabilities?”
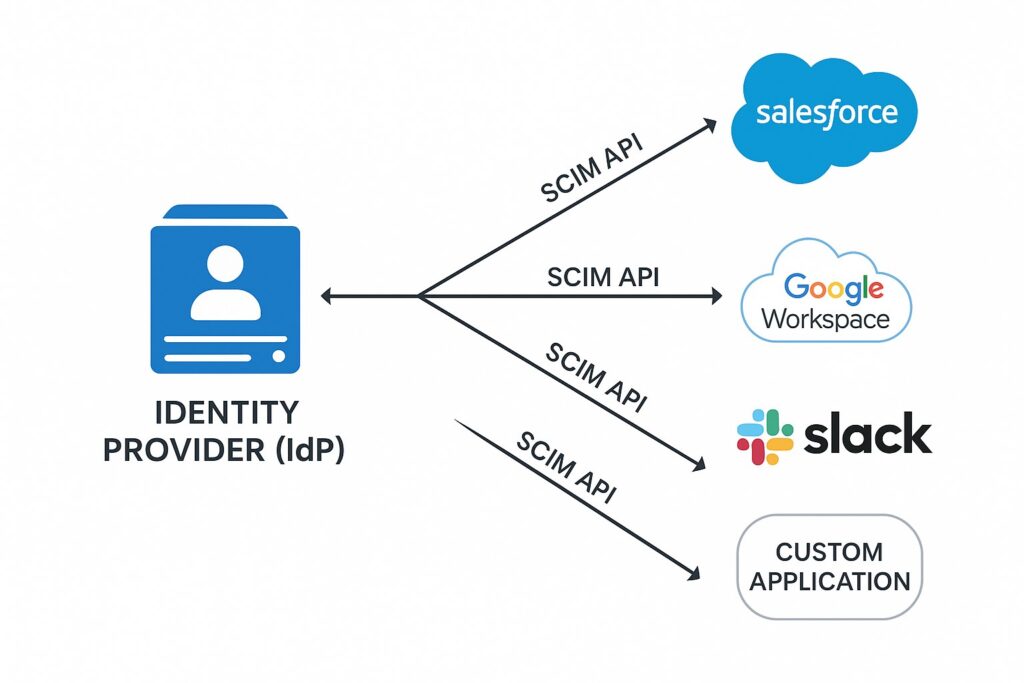
The SCIM Architecture: Building Blocks
To understand how SCIM works, let’s examine its key architectural components:
1. SCIM Service Provider
This is the system that stores identity data and responds to SCIM requests. Examples include cloud applications like Salesforce, Microsoft 365, or Google Workspace that implement the SCIM endpoint to receive identity data.
2. SCIM Client
The client initiates SCIM requests to manage identities. This is typically an Identity Provider (IdP) or Identity Management (IdM) system that serves as the authoritative source of identity information. Examples include Okta, Azure AD, or OneLogin.
3. SCIM Resource
A resource is an object with a defined schema, most commonly users and groups. Each resource has a unique identifier and a set of attributes according to the SCIM schema.
4. SCIM Endpoint
A RESTful API endpoint that processes SCIM requests, following standard HTTP methods:
- GET: Retrieve resources
- POST: Create new resources
- PUT: Replace resources
- PATCH: Update resources
- DELETE: Remove resources
This architecture establishes a standardized communication channel for identity data exchange, illustrated by this typical flow:
- An identity provider (SCIM Client) has user data that needs to be synchronized to a service (SCIM Service Provider)
- The client makes standardized SCIM API calls to the service provider
- The service provider processes these calls and updates its identity store accordingly
- Both systems maintain synchronized identity information
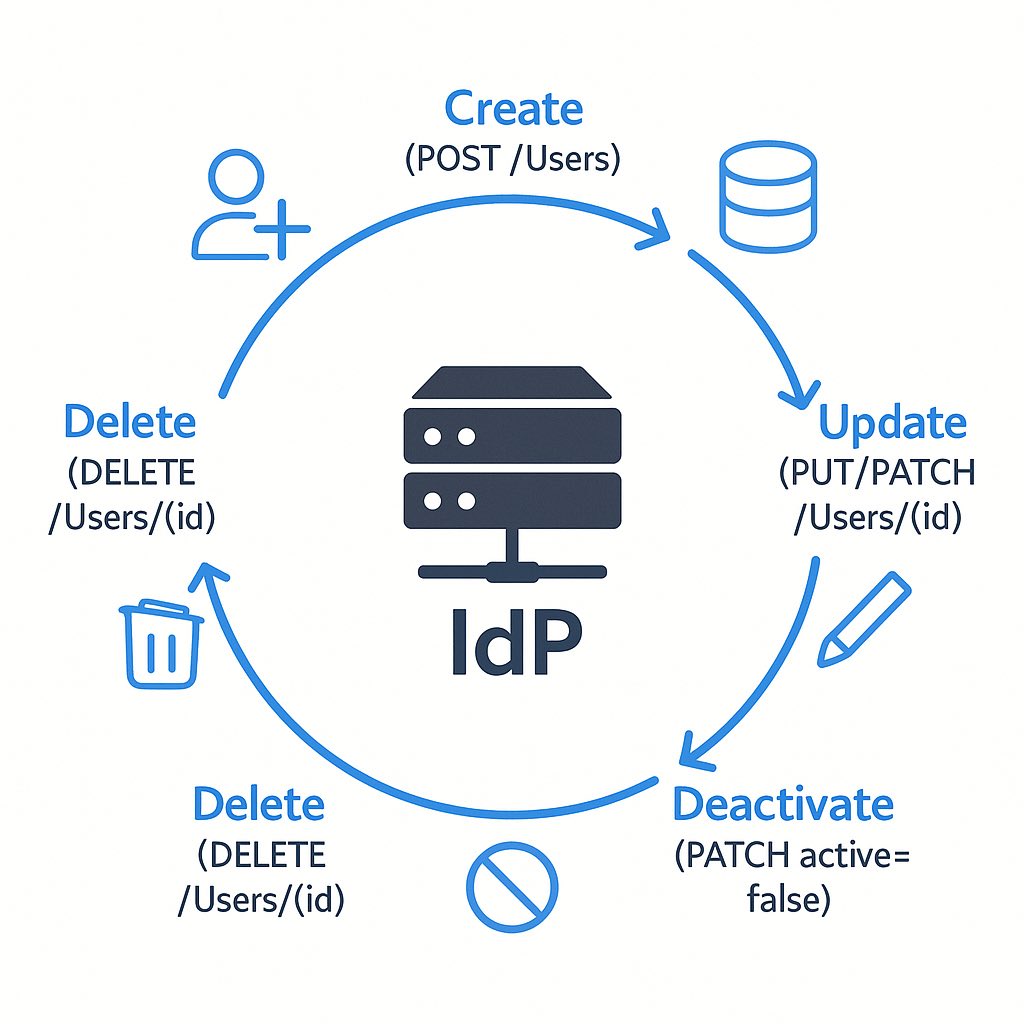
How SCIM Provisions Users: The Practical Flow
Now let’s look at how SCIM actually provisions users through its REST API. This process involves several standardized operations that enable the complete lifecycle management of identities.
User Provisioning Step-by-Step
1. User Creation
When a new user needs to be provisioned to a service, the SCIM client sends a POST request to the /Users endpoint:
POST /Users HTTP/1.1 Host: example.com/scim/v2 Content-Type: application/scim+json Authorization: Bearer token123 { "schemas": ["urn:ietf:params:scim:schemas:core:2.0:User"], "userName": "jsmith", "name": { "familyName": "Smith", "givenName": "John" }, "emails": [ { "type": "work", "value": "[email protected]", "primary": true } ], "active": true } The service provider processes this request and responds with a 201 Created status and the newly created user resource, including the assigned unique identifier:
HTTP/1.1 201 Created Content-Type: application/scim+json Location: https://example.com/scim/v2/Users/738492929 { "schemas": ["urn:ietf:params:scim:schemas:core:2.0:User"], "id": "738492929", "userName": "jsmith", "name": { "familyName": "Smith", "givenName": "John" }, "emails": [ { "type": "work", "value": "[email protected]", "primary": true } ], "active": true, "meta": { "resourceType": "User", "created": "2023-05-13T16:39:18Z", "lastModified": "2023-05-13T16:39:18Z", "location": "https://example.com/scim/v2/Users/738492929" } } This example demonstrates several important aspects of SCIM:
- Use of the standard SCIM schema URI in the
schemasarray - Core attributes structured according to the SCIM User schema
- Response providing additional metadata and the critical unique identifier
2. Retrieving Users
The SCIM client can retrieve users individually or perform searches with filtering:
Individual user retrieval:
GET /Users/738492929 HTTP/1.1 Host: example.com/scim/v2 Authorization: Bearer token123 Filtered search (finding all active users in the Engineering department):
GET /Users?filter=active%20eq%20true%20and%20department%20eq%20%22Engineering%22 HTTP/1.1 Host: example.com/scim/v2 Authorization: Bearer token123 The response contains the matching user resources with all their attributes, allowing the client to synchronize its data with the service provider.
3. Updating Users
When user information changes (such as a promotion, email change, or department transfer), the SCIM client updates the user with a PUT or PATCH request:
Complete replacement with PUT:
PUT /Users/738492929 HTTP/1.1 Host: example.com/scim/v2 Content-Type: application/scim+json Authorization: Bearer token123 { "schemas": ["urn:ietf:params:scim:schemas:core:2.0:User"], "id": "738492929", "userName": "jsmith", "name": { "familyName": "Smith", "givenName": "John" }, "emails": [ { "type": "work", "value": "[email protected]", "primary": true } ], "title": "Senior Engineer", "department": "R&D", "active": true } Partial update with PATCH:
PATCH /Users/738492929 HTTP/1.1 Host: example.com/scim/v2 Content-Type: application/scim+json Authorization: Bearer token123 { "schemas": ["urn:ietf:params:scim:api:messages:2.0:PatchOp"], "Operations": [ { "op": "replace", "path": "title", "value": "Principal Engineer" }, { "op": "add", "path": "phoneNumbers", "value": [ { "type": "work", "value": "+1-555-123-4567" } ] } ] } The PATCH operation is particularly powerful as it allows for targeted updates to specific attributes without needing to send the entire user object.
4. Deprovisioning Users
When a user leaves the organization, the SCIM client can either deactivate or completely remove the user:
Deactivation (preferred in many cases for audit purposes):
PATCH /Users/738492929 HTTP/1.1 Host: example.com/scim/v2 Content-Type: application/scim+json Authorization: Bearer token123 { "schemas": ["urn:ietf:params:scim:api:messages:2.0:PatchOp"], "Operations": [ { "op": "replace", "path": "active", "value": false } ] } Complete removal:
DELETE /Users/738492929 HTTP/1.1 Host: example.com/scim/v2 Authorization: Bearer token123 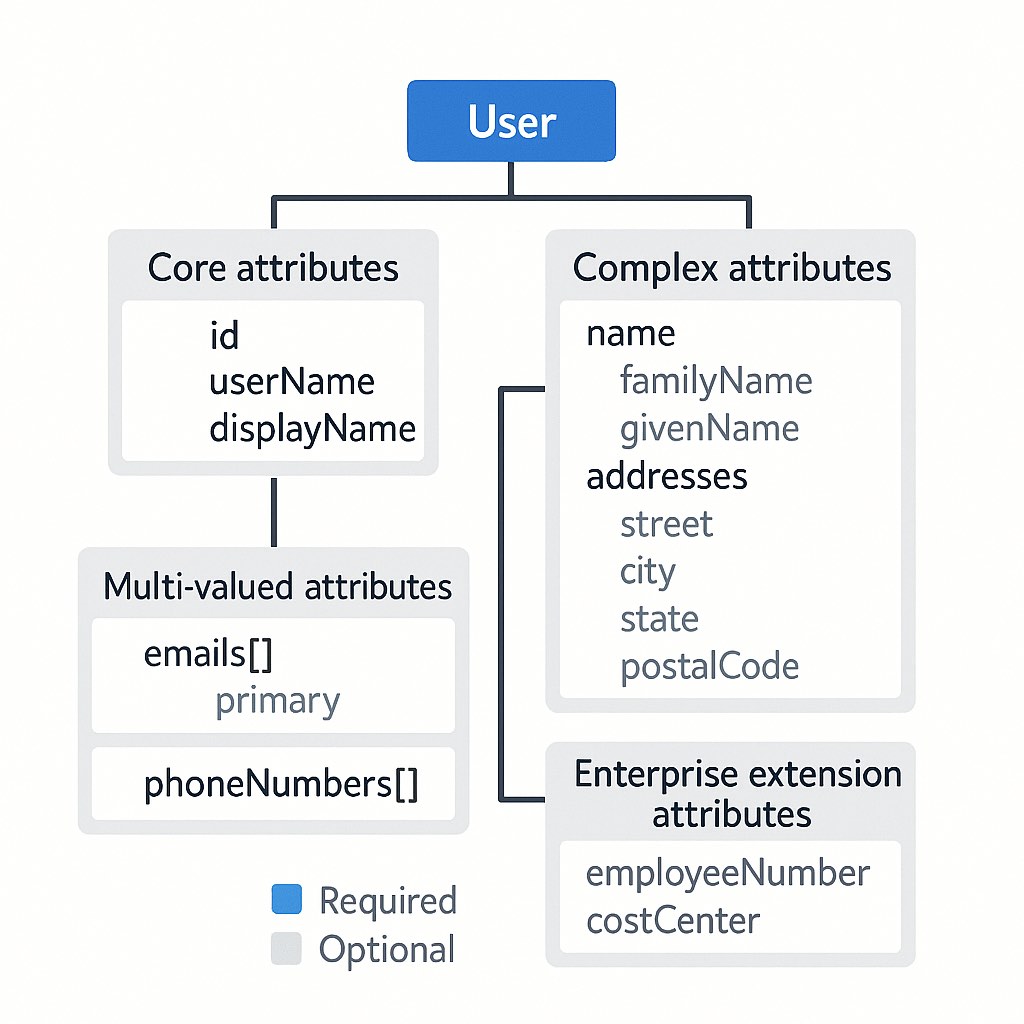
Group Management
SCIM also handles group provisioning and membership management:
Creating a group:
POST /Groups HTTP/1.1 Host: example.com/scim/v2 Content-Type: application/scim+json Authorization: Bearer token123 { "schemas": ["urn:ietf:params:scim:schemas:core:2.0:Group"], "displayName": "Engineering", "members": [ { "value": "738492929", "$ref": "https://example.com/scim/v2/Users/738492929", "display": "John Smith" } ] } Adding a member to a group:
PATCH /Groups/64528429 HTTP/1.1 Host: example.com/scim/v2 Content-Type: application/scim+json Authorization: Bearer token123 { "schemas": ["urn:ietf:params:scim:api:messages:2.0:PatchOp"], "Operations": [ { "op": "add", "path": "members", "value": [ { "value": "875693219", "$ref": "https://example.com/scim/v2/Users/875693219", "display": "Jane Doe" } ] } ] } The SCIM Schema: Anatomy of Identity Data
The SCIM schema is the foundation that enables standardized identity exchange. It defines how user and group data should be structured, providing a common language for identity attributes.
Core SCIM Schema
The SCIM Core Schema consists of:
- Common Attributes: Applied to all SCIM resource objects
id: Unique identifier for the resourceexternalId: Identifier for correlating with external systemsmeta: Metadata about the resource (creation, modification dates, etc.)schemas: URIs that indicate the resource schema versions
- User Schema: The standard attributes for user objects
- Core user information:
userName,name,displayName,nickName,profileUrl - Contact information:
emails,phoneNumbers,ims,addresses - Organizational information:
title,department,manager,roles - Security attributes:
active,password(write-only) - Custom attributes via extensions
- Core user information:
- Group Schema: The standard attributes for group objects
- Basic group information:
displayName - Membership:
membersarray with references to User resources
- Basic group information:
Example: Complete User Schema Object
Let’s examine a comprehensive SCIM user object that demonstrates the full richness of the schema:
{ "schemas": [ "urn:ietf:params:scim:schemas:core:2.0:User", "urn:ietf:params:scim:schemas:extension:enterprise:2.0:User" ], "id": "738492929", "externalId": "EMP00123", "userName": "jsmith", "name": { "formatted": "Mr. John G Smith, III", "familyName": "Smith", "givenName": "John", "middleName": "George", "honorificPrefix": "Mr.", "honorificSuffix": "III" }, "displayName": "John Smith", "nickName": "Johnny", "profileUrl": "https://example.com/profiles/jsmith", "title": "Principal Engineer", "userType": "Employee", "preferredLanguage": "en-US", "locale": "en-US", "timezone": "America/Los_Angeles", "active": true, "emails": [ { "value": "[email protected]", "type": "work", "primary": true }, { "value": "[email protected]", "type": "home" } ], "phoneNumbers": [ { "value": "+1-555-123-4567", "type": "work" }, { "value": "+1-555-987-6543", "type": "mobile" } ], "addresses": [ { "type": "work", "streetAddress": "100 Corporate Way", "locality": "San Francisco", "region": "CA", "postalCode": "94123", "country": "USA", "formatted": "100 Corporate WaynSan Francisco, CA 94123nUSA", "primary": true } ], "groups": [ { "value": "64528429", "$ref": "https://example.com/scim/v2/Groups/64528429", "display": "Engineering" }, { "value": "71836390", "$ref": "https://example.com/scim/v2/Groups/71836390", "display": "US Employees" } ], "urn:ietf:params:scim:schemas:extension:enterprise:2.0:User": { "employeeNumber": "EMP00123", "costCenter": "CC-123", "organization": "Technology", "division": "R&D", "department": "Backend Engineering", "manager": { "value": "459348307", "$ref": "https://example.com/scim/v2/Users/459348307", "displayName": "Sarah Johnson" } }, "meta": { "resourceType": "User", "created": "2023-01-15T08:30:00Z", "lastModified": "2023-05-13T16:45:22Z", "location": "https://example.com/scim/v2/Users/738492929", "version": "W/"a330bc54f0671c9"" } } This example illustrates several important aspects of the SCIM user schema:
- Multiple schemas: The core User schema is supplemented with the Enterprise User extension
- Complex attributes: Attributes like
nameandaddressescontain sub-attributes - Multi-valued attributes: Fields like
emailsandphoneNumberscan have multiple values with types - References: The
groupsfield contains references to other SCIM resources (Groups) - Extensions: The Enterprise User extension provides additional organizational attributes
Group Schema Example
A complete SCIM group object might look like this:
{ "schemas": ["urn:ietf:params:scim:schemas:core:2.0:Group"], "id": "64528429", "displayName": "Engineering", "members": [ { "value": "738492929", "$ref": "https://example.com/scim/v2/Users/738492929", "display": "John Smith" }, { "value": "875693219", "$ref": "https://example.com/scim/v2/Users/875693219", "display": "Jane Doe" } ], "meta": { "resourceType": "Group", "created": "2023-01-02T10:12:00Z", "lastModified": "2023-05-14T09:30:15Z", "location": "https://example.com/scim/v2/Groups/64528429", "version": "W/"e9c9b0c7d1e8f2a"" } } The group schema is simpler than the user schema but plays a crucial role in representing organizational structures and access control.
SCIM Implementation Considerations
While understanding the SCIM protocol is important, successful implementation requires attention to several practical considerations:
1. Attribute Mapping
One of the most challenging aspects of SCIM implementation is mapping attributes between systems. The source system (identity provider) and target system (service provider) often have different data models, requiring careful mapping of:
- Core attributes (name, email, etc.)
- Custom attributes specific to your organization
- Required versus optional attributes
- Data type conversions and validations
2. Error Handling
SCIM operations can fail for various reasons, including:
- Invalid data formats
- Missing required attributes
- Resource conflicts
- Authentication failures
- Authorization restrictions
Robust SCIM implementations include comprehensive error handling with appropriate HTTP status codes and error messages that follow the SCIM error response format.
3. Bulk Operations
For efficiency when provisioning many users, SCIM supports bulk operations:
POST /Bulk HTTP/1.1 Host: example.com/scim/v2 Content-Type: application/scim+json Authorization: Bearer token123 { "schemas": ["urn:ietf:params:scim:api:messages:2.0:BulkRequest"], "Operations": [ { "method": "POST", "path": "https://securityboulevard.com/Users", "bulkId": "qwerty", "data": { "schemas": ["urn:ietf:params:scim:schemas:core:2.0:User"], "userName": "jsmith", "name": { "familyName": "Smith", "givenName": "John" }, "emails": [ { "type": "work", "value": "[email protected]", "primary": true } ] } }, { "method": "POST", "path": "https://securityboulevard.com/Groups", "bulkId": "asdfgh", "data": { "schemas": ["urn:ietf:params:scim:schemas:core:2.0:Group"], "displayName": "Engineering" } }, { "method": "PATCH", "path": "https://securityboulevard.com/Groups/asdfgh", "data": { "schemas": ["urn:ietf:params:scim:api:messages:2.0:PatchOp"], "Operations": [ { "op": "add", "path": "members", "value": [ { "bulkId": "qwerty" } ] } ] } } ] } This example creates a user, creates a group, and adds the user to the group in a single request, using bulkId references to link the operations.
4. Security Considerations
SCIM implementations must address several security concerns:
- Authentication: Typically using OAuth 2.0 bearer tokens
- Authorization: Ensuring appropriate access controls
- Transport security: Always using TLS/HTTPS
- Input validation: Preventing injection attacks
- Rate limiting: Protecting against denial of service
The Future of SCIM: AI and Advanced Automation
As identity management evolves, SCIM is positioned to integrate with emerging technologies:
AI-Enhanced Provisioning
The next frontier for SCIM involves AI-driven identity management:
- Intelligent attribute mapping: Using machine learning to automatically map attributes between systems
- Anomaly detection: Identifying unusual provisioning patterns that might indicate security risks
- Predictive access recommendations: Suggesting appropriate group memberships and access rights based on job roles and behavior patterns
- Natural language processing: Enabling administrators to use conversational interfaces for identity management tasks
SCIM and Zero Trust Architecture
SCIM is becoming a critical component in Zero Trust security models by:
- Enabling just-in-time provisioning based on real-time access needs
- Supporting fine-grained attribute-based access control
- Facilitating continuous access evaluation and re-authentication
- Providing the identity foundation for contextual security decisions
Conclusion: SCIM as the Foundation of Modern Identity Infrastructure
SCIM has established itself as the essential standard for identity provisioning across domain boundaries. Its REST-based approach, standardized schema, and comprehensive operations make it indispensable for organizations managing identities at scale.
As businesses continue digital transformation efforts, SCIM provides the critical “identity plumbing” that connects diverse systems, enables workforce mobility, and supports security requirements. Understanding SCIM’s architecture, provisioning mechanisms, and schema design is essential knowledge for identity professionals building modern enterprise systems.
By implementing SCIM, organizations can achieve:
- Reduced operational overhead for identity management
- Faster onboarding and offboarding processes
- More consistent identity data across systems
- Better security through automated provisioning controls
- Improved compliance with access management requirements
Whether you’re implementing an identity management solution, developing a service that needs to support enterprise customers, or architecting a modern Zero Trust security framework, SCIM provides the standardized identity foundation upon which you can build.
*** This is a Security Bloggers Network syndicated blog from SSOJet authored by Devesh Patel. Read the original post at: https://ssojet.com/blog/how-scim-works-the-rest-api-powering-modern-identity-provisioning/
Original Post URL: https://securityboulevard.com/2025/05/how-scim-works-the-rest-api-powering-modern-identity-provisioning/?utm_source=rss&utm_medium=rss&utm_campaign=how-scim-works-the-rest-api-powering-modern-identity-provisioning
Category & Tags: Identity & Access,Security Bloggers Network,Authentication,Authentication protocols,b2b,B2B SaaS,enterprise,Enterprise SSO,Identity & Access Management (IAM),SAML,SCIM,single sign on,sso – Identity & Access,Security Bloggers Network,Authentication,Authentication protocols,b2b,B2B SaaS,enterprise,Enterprise SSO,Identity & Access Management (IAM),SAML,SCIM,single sign on,sso
Views: 3






















































