Source: securityboulevard.com – Author: Max Aulakh
FedRAMP is the Federal Risk and Authorization Management Program, and it’s one of the most widely used governmental cybersecurity frameworks across the United States. It’s meant to serve as the gatekeeper for any contractor looking to work with the federal government to ensure that everyone across the board has a minimum level of cybersecurity in place to protect themselves, the government, and each other from risks and threats.
FedRAMP is not alone. There is a whole range of other cybersecurity frameworks, from NIST’s CSF, to narrower frameworks like HIPAA, PCI-DSS, and SOC 2, to other top-level frameworks like CMMC and ISO 27001.
The question is, does FedRAMP have reciprocity with any of these? Or, if your business is looking to win contracts that function under other frameworks, will you have to go through the whole compliance process again for each?
What is Reciprocity?
The idea of reciprocity is a good one. The concept is simple: two entities who maintain frameworks agree that those frameworks are similar enough in substance or end result that they can accept the results of each other’s compliance and auditing.
The DoD defines it specifically as:
“…the agreement among participating organizations to accept each other’s security assessments, to reuse system resources, and/or to accept each other’s assessed security posture to share information.”
Reciprocity requires work, especially on the part of the organizations participating in that reciprocity. The goal is for, say, the DoD and the ISO/IEC to work together to evaluate the security standards and postures instead of forcing every organization that wants to comply with both to repeat the work.

Overall, the goal of reciprocity is to allow individual businesses to comply with one framework and be able to work within the context of other reciprocal frameworks without having to repeat the whole auditing process again to comply and win contracts.
Does FedRAMP have Reciprocity?
FedRAMP actually has a sort of reciprocity built into it at its core.
The way FedRAMP works is that a business finds a governmental agency to sponsor it. The business determines what impact level they have and what security they need to implement and puts it into practice. They apply for an Authority to Operate, undergo an audit, and, if validated, can start to work on the contract with their sponsoring agency.
If the company wants to pick up another contract with a different governmental agency, they have to go through this process again with the new agency. It’s faster and easier because all of the security is already in place, so it’s almost a formality, but it’s still repetition.

FedRAMP’s Joint Authorization Board is able to sponsor businesses that are broad enough to be viable with many different agencies throughout the government. For those businesses, the JAB can be the sponsoring agency and issue a Provisional Authority to Operate, or P-ATO. This is sort of like a reciprocal version of an ATO, valid with all federal agencies that would want to work with the business. It’s still not fully an automatic, reciprocal approval, but it’s similar in concept.
That’s for internal FedRAMP reciprocity, but what about reciprocity with other frameworks?
FedRAMP and CMMC
CMMC is one of the most important current frameworks because it’s the cybersecurity framework used by the Department of Defense for handling controlled unclassified information.
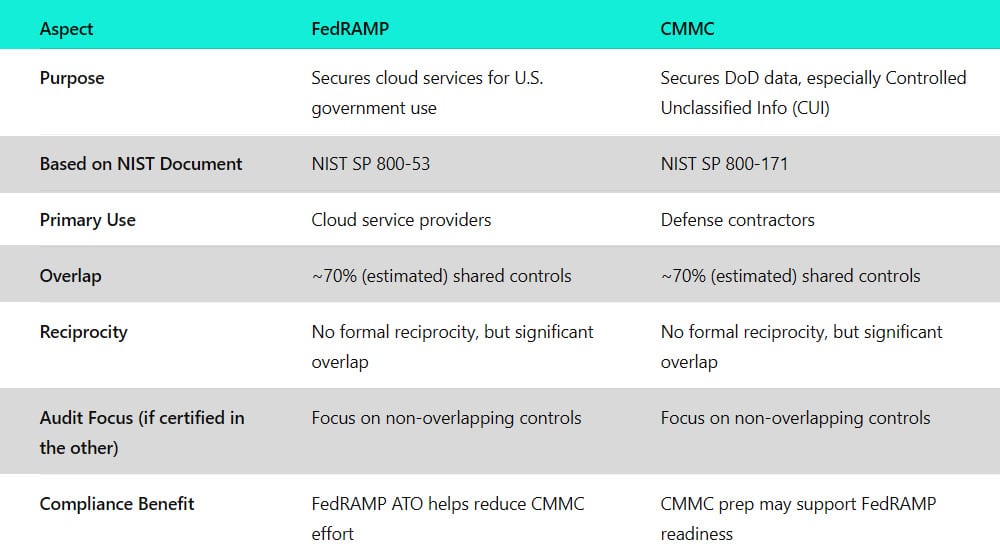
While both are US government frameworks meant to help secure information, and both are based on NIST documents, they aren’t fully similar. FedRAMP is based on NIST SP 800-53, while CMMC is based on NIST SP 800-171. While the two share a lot of DNA, they aren’t identical, which means that the frameworks derived from them are also not identical.
FedRAMP and CMMC have a sort of partial reciprocity. They share enough DNA that, say, 70% of them are functionally identical to one another. (That’s not a real figure, just one pulled out for an example.)
That means a business that is already awarded a FedRAMP ATO could assume that around 70% of the work is already done; the remaining 30% still needs to be done, and it all needs to be properly documented and pass a CMMC audit. However, the simple fact that the business passed the FedRAMP audit means they’re a good portion of the way there.
There’s no formal or official reciprocity between FedRAMP and CMMC; there is just equivalency for a good chunk of the security controls present in both. Audits for either will primarily focus on the areas not equivalent to the other when the business in question already has compliance certification for one.
FedRAMP and ISO 27001
ISO 27001 is very likely the most-used cybersecurity framework in the world. Unlike FedRAMP and CMMC, ISO 27001 is international. It’s developed and managed by the ISO/IEC and is available to any business anywhere in the world willing to buy the package, implement the security, and pay for the audit.
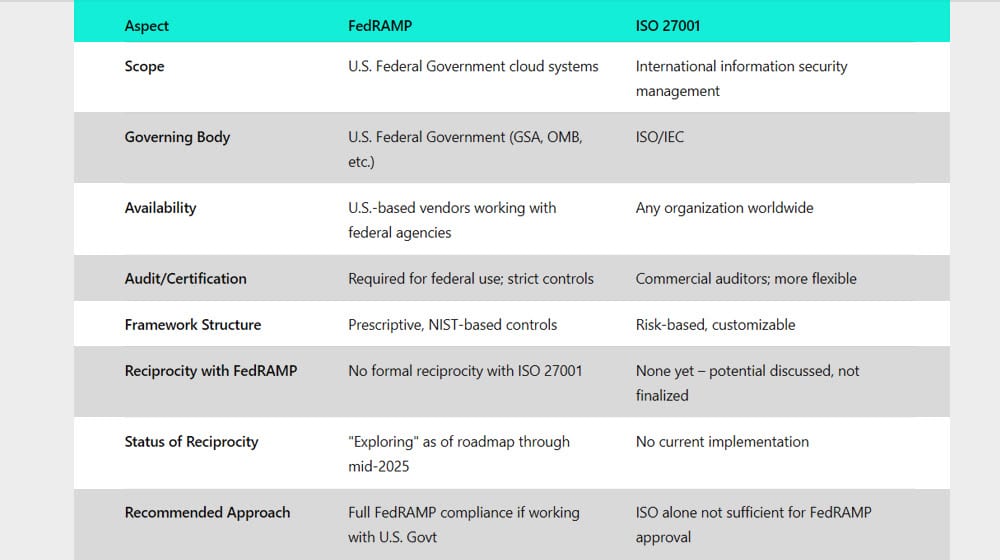
If a business is certified as secure at an international level, is that enough to be worth reciprocity with FedRAMP and enable the business to work with the US Federal Government?
This is also a tricky situation to untangle. Years ago, the intent was to issue reciprocal certifications across FedRAMP and ISO 27001. The three – FedRAMP, CMMC, and ISO 27001 – formed a kind of reciprocal triangle, with CMMC potentially bridging the gap. It might not have necessarily meant FedRAMP and ISO 27001 had reciprocity, but they could both use CMMC to bridge to the other.
While the speech at the time claimed that there were memos “ready to be signed” to implement this, the reality is that those memos seem to have never materialized. Since then, “exploring reciprocity with external frameworks” has been on roadmaps as recently as the end of last year, further indicating that such reciprocity does not yet exist. In fact, on the high-level roadmap, “Define initial approach for reciprocity between external frameworks and low baseline” is slated for the first half of 2025.
Will it happen? That remains to be seen, but given how delayed this reciprocity has been over the years, don’t hold your breath. Work on full compliance if you need it. If reciprocity comes along later and makes some of your efforts redundant, that’s a pain, but it’s better than waiting for something that has already been delayed numerous years in the hopes that this time it will really happen.
Like the crossover between FedRAMP and CMMC, FedRAMP also shares a lot of goals with ISO 27001. However, ISO 27001 is also a much more free-form certification meant to be more intensely customized to the business being certified, so there’s a lot less direct, 1:1 overlap between ISO 27001 goals and FedRAMP security controls. This means a direct and easy reciprocity is not readily available, and equivalency is harder to achieve.
FedRAMP and GovRAMP
GovRAMP is the new name for what was formerly known as StateRAMP. GovRAMP is meant to be, effectively, the state and local government version of FedRAMP. It’s largely as 1:1 as possible between two frameworks; the only roadblock is that the federal government does some gatekeeping with data, POA&Ms, and continuous monitoring results that make it more difficult for state and local government agencies to access the validation data.
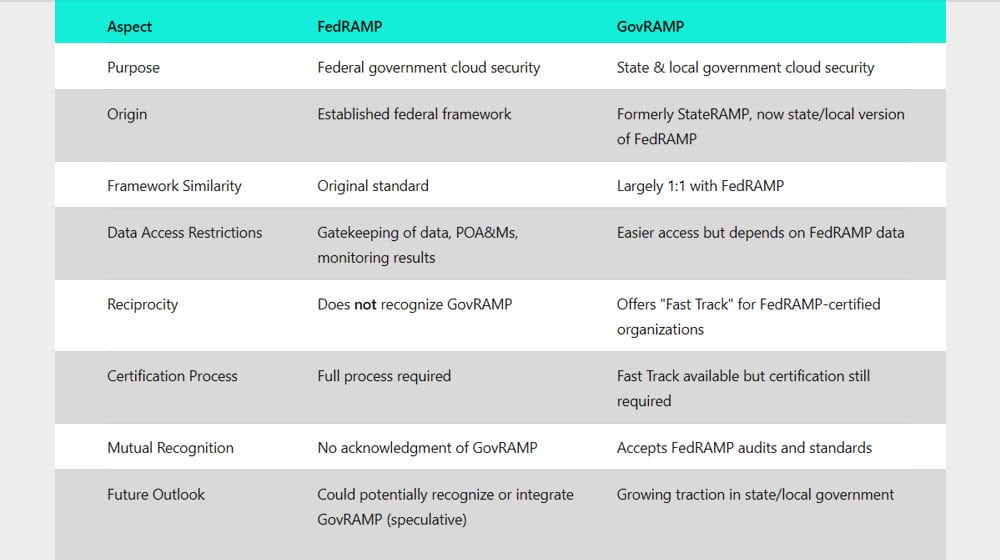
GovRAMP is gaining traction, and as such, they’re providing a “Fast Track” process for certification specifically for organizations that are FedRAMP certified. They accept reciprocity for C3PAOs that are authorized to provide FedRAMP audits, and they accept that an organization that meets FedRAMP standards also likely meets their standards.
However, this is not quite reciprocity for two reasons.
The first is that an organization applying for GovRAMP certification still needs to go through the process, even if it’s a fast-tracked version of the process. It’s not simply accepted that meeting FedRAMP meets GovRAMP and that an ATO or P-ATO can be immediately issued.
More importantly, it’s only one-way. For now, FedRAMP doesn’t even acknowledge that GovRAMP exists. The only mention of it on FedRAMP’s official site is in the descriptions of a couple of marketplace-listed agencies, which are written by those agencies and not FedRAMP itself.
This means that while GovRAMP can accept that someone meeting FedRAMP standards will meet theirs, FedRAMP doesn’t go the other way. As GovRAMP gains more and more traction, the federal government might decide to more proactively recognize GovRAMP or even take it over as a way to further centralize and protect state-level and lower-level security interests; however, that’s all just speculation and might never happen.
FedRAMP and Other Frameworks
There are a lot of other security frameworks out there that may be relevant, and you’d wonder if there’s reciprocity with FedRAMP.
- HIPAA
- HITRUST
- SOC 2
- PCI-DSS
For the most part, these frameworks are either too narrow or focused on different kinds of security, so there’s no real reciprocity with FedRAMP.
HIPAA is all about securing information, but it’s about both security and access of health information, which is a subset of CUI but does not encompass all of CUI. Similarly, SOC2 protects consumer financial information, and PCI-DSS protects credit card and payment information. All of these are much narrower than FedRAMP.

If there was reciprocity between these, it would be one-way; FedRAMP is much larger and more all-encompassing, and compliance with it could potentially mean complying with the rules in PCI-DSS or SOC2; however, that’s not necessarily guaranteed. Meanwhile, complying with basic HIPAA, PCI-DSS, SOC2, or similar frameworks falls far short of what is necessary to reach even a low baseline FedRAMP ATO, so no reciprocity is possible.
One area where there is a more formal reciprocity is with DFARS 7012. This is also not quite accurate, however, because DFARS 7012 is less of a framework and more of a set of benchmarks. The DoD has acknowledged that FedRAMP Moderate and above meet or exceed the targets set out in DFARS 7012, so FedRAMP Moderate is acceptable as a way to self-attest DFARS compliance.
The story is generally the same with any other framework you could name. It’s either:
- Much narrower than FedRAMP, so any reciprocity would be one-way on the part of the non-FedRAMP entity.
- Broadly equivalent but with no official reciprocity, similar to the situation with CMMC.
- More stringent than FedRAMP, so FedRAMP doesn’t meet the needs, and reciprocity can’t be established.
If you have more specific questions, feel free to reach out and ask; complying with FedRAMP can still be a beneficial option and can get you ahead of the game with many frameworks; there’s just very little in the way of official 1:1 reciprocity.
No Reciprocity? No Problem!
Reciprocity is, in many ways, the “easy way” towards obtaining multiple cybersecurity certifications. When two programs have formal reciprocity, complying with one gets you access to the benefits of both, albeit in an often partial or limited fashion.
However, nothing stops you from pursuing full, formal compliance with both, even where reciprocity does not (or cannot) exist.
This is one area where the Ignyte Assurance Platform excels. We built the platform as a centralized, non-siloed way for organizations and their implementation teams to collaborate on documenting the implementation of security controls. You can use it to track progress and store artifacts, attestations, and data to back up your implementation.

Since many security frameworks are aiming for the same goals, and there are only so many routes to achieve those goals, complying with FedRAMP puts you in a good position to have a lot of the work done for other frameworks already. While the specific documentation may be different, it can all be tracked and stored in the Ignyte Platform, ready to be accessed and reviewed by an auditing organization.
That means, through robust and centralized documentation, you can minimize the amount of duplicate work and repeated reviews that are necessary to comply with multiple frameworks. It’s like having your own built-in reciprocity where official reciprocity is missing.
If this sounds like something valuable to you, it’s quick and easy to book a demo and see what the Ignyte Platform has to offer you.
*** This is a Security Bloggers Network syndicated blog from Ignyte authored by Max Aulakh. Read the original post at: https://www.ignyteplatform.com/blog/fedramp/fedramp-reciprocity-other-frameworks/
Original Post URL: https://securityboulevard.com/2025/05/how-fedramp-reciprocity-works-with-other-frameworks/?utm_source=rss&utm_medium=rss&utm_campaign=how-fedramp-reciprocity-works-with-other-frameworks
Category & Tags: Security Bloggers Network,FedRAMP – Security Bloggers Network,FedRAMP
Views: 4






















































