Source: hackread.com – Author: Waqas.
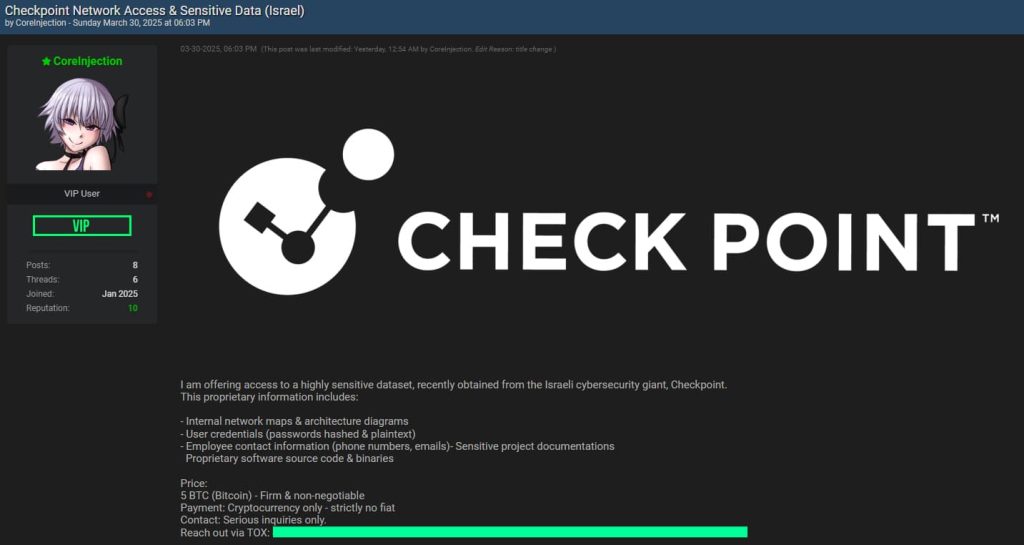
A hacker operating under the alias “CoreInjection” is claiming responsibility for the breach of Israeli cybersecurity company Check Point, alleging access to sensitive internal data and network systems.
The hacker published their claims on Breach Forums on Sunday, March 30, 2025, and announced the sale of the stolen content for a price of 5 Bitcoin ($434,570). The hacker emphasized that the price is “firm and non-negotiable,” with cryptocurrency being the only accepted form of payment. Interested parties were directed to make contact via the TOX messaging platform.
In the forum listing, CoreInjection said the data for sale includes:
- Internal project documentation
- User credentials, both hashed and in plaintext
- Internal network maps and architecture diagrams
- Source code and compiled binaries of proprietary software
- Employee contact details, including phone numbers and email addresses
Check Point Responds
Shortly after the post gained attention, Check Point issued a statement denying any recent breach of this scale. According to the company, the claim relates to an “old, known and very pinpointed event” that affected a limited number of organizations and did not touch any core systems.
“This was handled months ago and didn’t include the description detailed on the dark forum message,” Check Point said in a statement. “These organisations were updated and handled at that time, and this is not more than the regular recycling of old information.”
The company insists there was no security threat to its customers, infrastructure, or internal operations. They clarified that the affected portal did not involve production environments or systems containing sensitive architecture.
Who is CoreInjection?
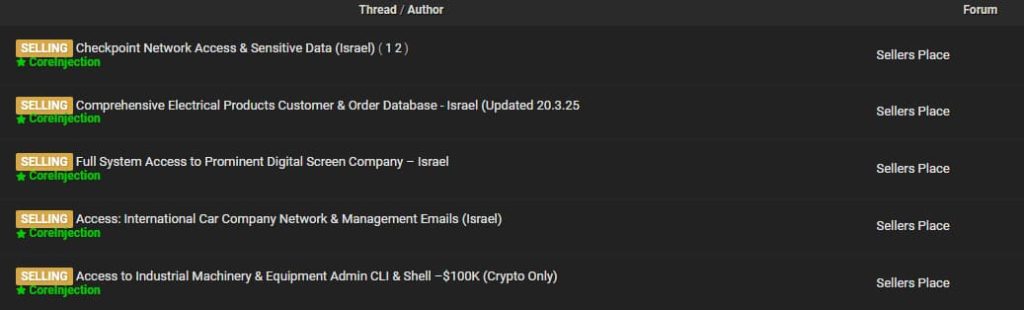
CoreInjection is a relatively new player in cybercrime but has quickly made a name for itself by targeting critical infrastructure and high-profile networks, particularly in Israel. The hacker’s first appearance on Breach Forums was on March 15, 2025, and since then, they’ve posted five listings offering network access to various companies.
Their earliest post was for access to an industrial machinery and equipment admin panel for a U.S.-based company, priced at $100,000. But the pattern that emerged shortly after points to a specific geographic focus: Israel.
On March 16, CoreInjection claimed to be selling access to the network and management emails of an Israel-based international car company. According to the listing, the access includes “full control over the company’s Israeli network infrastructure,” with a price tag of $50,000.
Two days later, on March 18, another listing surfaced, this time offering “Full System Access to a Prominent Digital Screen Company” based in Israel. Priced at $100,000, the listing described access to a central server responsible for managing a large inventory of digital displays across shopping malls. The post highlighted that the access allowed “instantaneous content and propagation,” effectively enabling real-time control over public display systems.
That detail alone raises flags for cybersecurity experts. Groups linked to Iran, Hezbollah, and Palestinian hacktivists have a history of targeting CCTV cameras, television feeds and public-facing screens, often defacing them with political messages. If CoreInjection’s claim is accurate, the sale of such access could open the door to similar high-visibility attacks.
On March 20, another listing followed; this time for an Israeli company in the electrical products sector. CoreInjection claimed to have an “exclusive and up-to-date customer and order database” from the firm, with the asking price set at $30,000.
(Screenshot credit: Hackread.com)
Altogether, CoreInjection’s listings suggest a focused campaign with a clear pattern: high-value access, critical systems, and a strong interest in Israeli infrastructure. Whether operating independently or as part of a broader effort, the hacker’s activities have drawn attention in both underground forums and the cybersecurity community.
Questions Remain
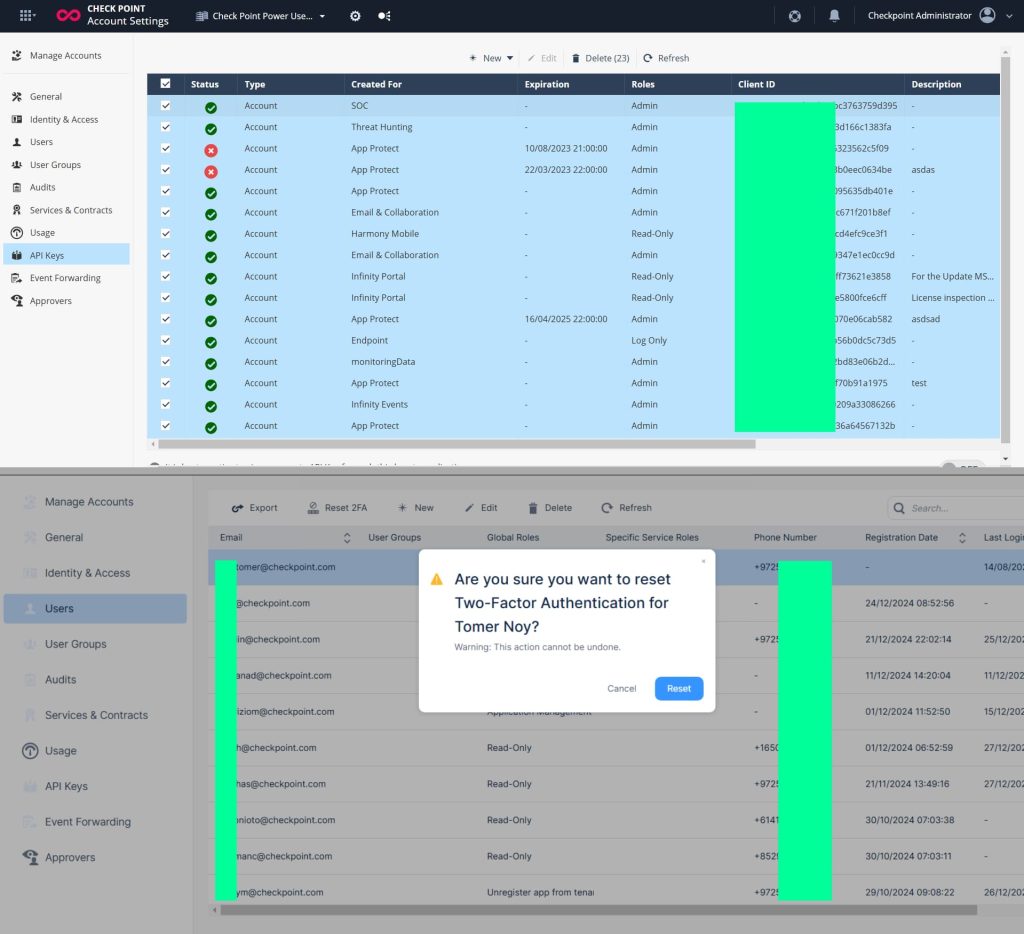
Despite the company’s reassurance, the hacker’s detailed description of the alleged stolen materials has raised concerns. The mention of internal network diagrams, plaintext credentials, and proprietary software could point to deeper access than Check Point admits if the data is genuine.
Several questions are still unanswered. If this is indeed an old event, why was it never publicly disclosed at the time it happened? Transparency is expected, especially from a cybersecurity vendor of Check Point’s size. The lack of details about how the incident occurred also leaves a gap in understanding the nature of the breach. Was it a misconfigured portal, a credential compromise, an insider threat, or something else entirely?
Furthermore, Check Point hasn’t addressed whether they’ve identified the method of breach or if they have any suspects linked to the event. Without that information, it’s difficult to assess whether the threat has been fully contained or if there’s an ongoing threat.
This incident comes at a time when cybercriminals are increasingly targeting cybersecurity vendors themselves, often exploiting smaller missteps to escalate into bigger breaches. Whether CoreInjection’s claims hold weight or not, the situation shows that even firms specializing in defense aren’t safe from threat actors.
Original Post url: https://hackread.com/hacker-breach-check-point-cybersecurity-firm-access/
Category & Tags: Security,Cyber Attacks,Check Point,Cyber Attack,Cybersecurity,Data,Israel,security – Security,Cyber Attacks,Check Point,Cyber Attack,Cybersecurity,Data,Israel,security
Views: 2