Android infections are also prevalent on the dark web, according to Kaspersky. Learn how to keep your workforce safe from these mobile and BYOD security threats.

New research from Kaspersky focuses on the types of malicious services provided by cybercriminals on the dark web, based on the monitoring of pastebin sites and restricted underground online cybercrime forums.
The security researchers found that Google Play threats and Android phone infections are big business. For example, a Google Play developer account can be bought for around $60-$200 USD depending on account characteristics such as the number of developed apps or the number of downloads. Bot development or rent ranges between $1,000 USD and $20,000 USD.
Jump to:
- How could malware be on Google Play?
- What are Google Play Loaders?
- How does file binding obfuscate malware?
- Costs to increase the infection rate vary based on the country
- Android malware for any kind of cybercrime
- How to protect from this security threat
How could malware be on Google Play?
On Google Play, before an Android app is available to users, it undergoes a review process to verify that it meets certain standards and adheres to the developer policies, to ensure that it is not harmful or malicious.
However, there are still ways for cybercriminals to distribute malicious content via the platform. One of the most common methods is to have a benign app approved on Google Play and then updated with malicious content or malware, which might compromise all users of that application and possibly their employers’ networks.
It’s not uncommon for users to bring a personal mobile device to work, which might store corporate passwords or other information that could help an attacker compromise the corporate network.
SEE: Learn how BYOD and personal apps can be a recipe for data breaches.
Additionally, companies that own Google Play developer accounts can be targeted for supply chain attacks by having some of their code modified to add malware, such as information stealers.
What are Google Play Loaders?
Google Play Loaders are pieces of code whose purpose is to inject malicious code into a Google Play application. They are some of the most common offers on the dark web.
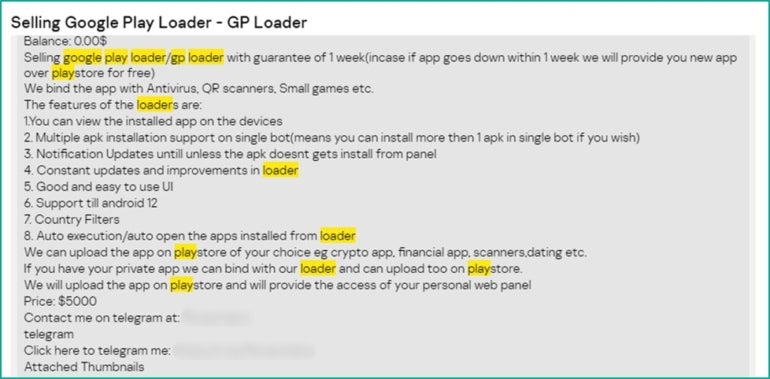
The injected code is then updated on Google Play. When the victim downloads the malicious update onto their device, they may receive the final payload or a notification asking them to allow installation of unknown apps and then install it from an external source.
In the latter scenario, the notification persists until the user agrees to install the additional app. Upon installation, the user is prompted to grant access to critical data such as Accessibility Services, the camera and microphone. Until these permissions are granted, the victim may not be able to use the original legitimate app.
The sellers usually indicate the kind of legitimate apps they can use for their loader and the number of downloads of the app. Those apps are often cryptocurrency trackers, financial apps, QR-code scanners or dating apps, according to the researchers. Attackers have compromised legitimate popular apps used in corporate environments such as a document scanning app, or used applications mimicking famous ones such as WhatsApp or Telegram.
Loader source code is available for sale. Kaspersky reports a loader source code being auctioned with a starting price of $1,500 USD, with bid increments of $200 USD and an instant purchase price of $7,000 USD.
How does file binding obfuscate malware?
File binding is a technique used by attackers to combine or merge malicious code with legitimate files on any operating system, making it harder for security solutions to detect the malware. Those files are often not spread in Google Play, but via social engineering or websites distributing cracked games or software.
As the distribution of such applications is more difficult than for those offered through Google Play, the prices are much cheaper than for loaders, ranging between $50-$100 USD.
A similar service is the malware obfuscation service, where the provider obfuscates a given malware code to bypass security systems. This service can be paid on a subscription basis or for a single file. A file would cost around $30 USD, while a subscription for 50 files is about $440 USD.
Costs to increase the infection rate vary based on country
Some cybercriminals offer services to increase infection rate by increasing the app traffic through Google ads. Using that technique, the malware comes as the first Google search result and is downloaded by unsuspecting victims. While search engine optimization is legitimate and used to bring as many downloads as possible, it can also be used to spread fraudulent content in different countries. The costs to increase the infection rate vary according to the country, as some countries are more interesting for cybercriminals than others.
These costs vary from approximately $0.10 USD to $1 USD, with the U.S. being amongst the most expensive at approximately $0.80 USD, along with Canada and Australia. This is followed by European countries at approximately $0.50 USD and so-called Tier-3 countries at around $0.25 USD.
Android malware for any kind of cybercrime
Malware on Android might be used for any kind of fraud. All kinds of malware are sold and bought on the dark web, including banking trojans and cyberespionage malware.
Attackers interested in financial fraud tend to target as many Android devices as possible in order to collect data, such as credit card information. It therefore makes sense for them to try to get their malware on Google Play to spread it as much as possible.
Targeted attacks are different because they mostly rely on social engineering tricks to entice a targeted user into installing a malicious application. Because they approach their victims through email or instant messaging apps, they need their malware to be more discreet and often do not use Google Play for those attacks.
How to protect from this security threat
- Use multifactor authentication for your developers’ accounts on application platforms such as Google Play.
- Monitor the dark web for credentials and access leaks that might enable an attacker to compromise any application built by a developer from your company.
- Educate employees about mobile phone threats. Advise them to never download any application from any non-official store, even if the installation link seems to originate from the company. If they’re unsure an install link is valid and legitimate, they should contact IT.
- When installing an application, users should carefully check the privileges that the application requests. For example, a QR Code scanner should not ask for permission to send SMS.
- Remind employees to keep the OS for their mobile devices up to date and patched.
Disclosure: I work for Trend Micro, but the views expressed in this article are mine.




















































