Source: www.databreachtoday.com – Author: 1
Fraud Management & Cybercrime
,
Governance & Risk Management
,
Healthcare
HHS: Group Seems to Favor Targeting Small & Midsized Entities that Lack MFA on VPNs
Marianne Kolbasuk McGee (HealthInfoSec) •
September 13, 2023
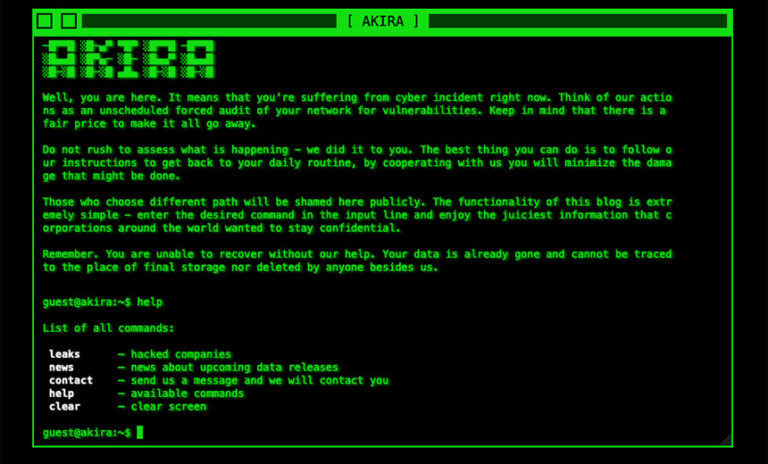
Federal authorities are warning the health sector about threats posed by Akira, a ransomware-as-a-service group that surfaced about six months ago and has been linked to several dozen attacks on predominately small and midsized entities across many industries.
See Also: Live Webinar | Unmasking Pegasus: Understand the Threat & Strengthen Your Digital Defense
The group seems to favor organizations in which multifactor authentication has not been deployed on virtual private networks, the Department of Health and Human Services’ Health Sector Cybersecurity Coordination Center said in a threat alert issued Tuesday.
Akira, which carries out double-extortion attacks involving data theft and then ransomware encryption, appears to obtain initial malware delivery through several methods, including leveraging compromised credentials and exploiting weaknesses in virtual private networks, especially where multifactor authentication is not used, HHS HC3 said.
Additional attack methods have included phishing emails, malicious websites, drive-by download attacks, and Trojans, HHS HC3 said.
Researchers have observed that Akira appears to have similarities with the disbanded Conti ransomware group, HHS HC3 said. “This was a result of some identified code overlap and the implementation of ChaCha 2008, as well as the code for key generation, both of which resemble the one used by Conti,” the agency said.
The two groups also share other similarities: The list directory exclusions that Akira’s ransomware avoids encrypting, including winnt and Trend Micro, are the same in Conti ransomware strains, and researchers have found overlaps in the cryptocurrency wallets used by Akira and Conti, HHS HC3 said.
In addition to healthcare, Akira has been targeting other sectors such as finance, real estate and manufacturing, the agency said.
Double Extortion
Prior to encrypting files, Akrira exfiltrates the victim organization’s data, threatening to publicly release sensitive information unless a ransom is paid. “The group also offers victims a lower-cost option to not pay for a decryptor and to not have the especially sensitive information published,” HHS HC3 writes.
“Once infected, the malware will launch PowerShell to remove shadow volume copies, and once encryption is complete, the file’s extension will be reassigned with the ‘.akira’ extension. The attackers also attempt lateral movement and privilege escalation through LSASS credential dumps,” the agency said.
Akira’s ransom payment demands have ranged from $200,000 to $4 million, HHS HC3 said.
Attack Patterns
In June, security firm Avast released a free decryptor for Akira ransomware that the company said can decrypt both affected Windows and Linux files (see: Are Akira Ransomware’s Crypto-Locking Malware Days Numbered?).
But it is uncertain whether the availability of a free decryptor has deterred Akira’s attacks. In June, the group’s dark web site claimed to have 63 victims. But as of Thursday, that number had risen to 96 organizations, according to threat intelligence firm Darkfeed.io, which monitors the dark web.
In a recent blog that was updated last Thursday, Security firm Rapid7 reported that its managed detection and response teams have observed increased threat activity targeting Cisco ASA SSL VPN appliances – physical and virtual – dating back to at least March 2023 – around the time of Akira first surfaced.
“Several incidents our managed services teams have responded to ended in ransomware deployment by the Akira and LockBit groups,” Rapid7 reported.
Also, nearly 40% of all incidents to which Rapid7’s managed services teams responded in the first half of 2023 stemmed from lack of MFA on VPN or virtual desktop infrastructure, the firm reported.
“These incidents reinforce that use of weak or default credentials remains common, and that credentials in general are often not protected as a result of lax MFA enforcement in corporate networks,” Rapid7 wrote.
Indeed, when employees’ credentials get compromised through phishing or other methods, an organization that is not using MFA “is far more likely to have a bad outcome than one that is,” said threat analyst Brett Callow of security firm Emsisoft.
“The best thing organizations can do to reduce their risk profile is to make themselves less vulnerable – and they can do that by using MFA and ensuring they tick off the other cybersecurity 101s,” he told Information Security Media Group.
“The bottom line is that most cyberattacks are opportunistic and preventable,” he said.
Aside from implementing MFA, HHS HC3 recommends healthcare sector entities take several other critical preventative steps, including updating and patching systems regularly, implementing account lockout policies to defend against brute-force attacks, applying network segmentation, and having a robust recovery and incident response plan.
Original Post url: https://www.databreachtoday.com/feds-warn-healthcare-sector-akira-ransomware-threats-a-23073
Category & Tags: –